-
-

one of hundreds of posters we plastered around hack the north
-

the first screen players see when a game isn't running
-

the login flow
-

the leaderboard after day 1 (look at those faces! we put in plenty of work to automatically scrape them from linkedin and github)
-

reverse-engineering hack the north's internal api
-

So. What were all those weird posters about? What in the honk is goosechase? And where are the hot single geese in my area that I was promised?
Great question: what's goosechase?
Goosechase is a massive game of tag, of sorts.
We littered hundreds of cryptic QR code posters all around Hack the North.
- Someone scans the QR code and is prompted to scan their Hack the North badge and enter their phone number to register.
- At some point we run a game. Every registered user receives a text message out of nowhere that It Is Beginning somewhere on the hackathon grounds.
- One person is randomly selected as "it" and every other player is notified to look for them. Whoever finds the target first and scans their badge with goosechase wins the round.
- Both the tagger and the target earn points based on how fast they got tagged.
Over time the crowd SNOWBALLS as unsuspecting bystanders wonder what all the ruckus is about and join in. Along the way, everyone makes new friends, has a load of fun (the video is proof of that!), and scores points to rank them on the goosechase leaderboard.
And the whole time, everyone is still wondering "who made this weird goosechase thing?"
How we built it
Stack-wise, we converged on tech we were all familiar with that let us build really quickly... Next.js, Prisma, Postgres, Twilio.
We did some really cool technical things, though. For example, we reverse-engineered Hack the North's internal API and abused the "connection" feature to auth and get info (name, social media profiles, etc.) on users just by scanning their badges. (As a side effect of this, Lexi now has probably the most "connections" of anyone at Hack the North.)
We then went a step further by scraping profile pictures from said social media profiles to show in the leaderboard.
Challenges we ran into
We (semi-accidentally) spent about $140 on the project... ~$40 to print our posters at the Waterloo library and for rolls of tape (*cough cough* "marketing budget") and another ~$100 on Twilio fees for the THouSANDS of game-related text messages we sent out:
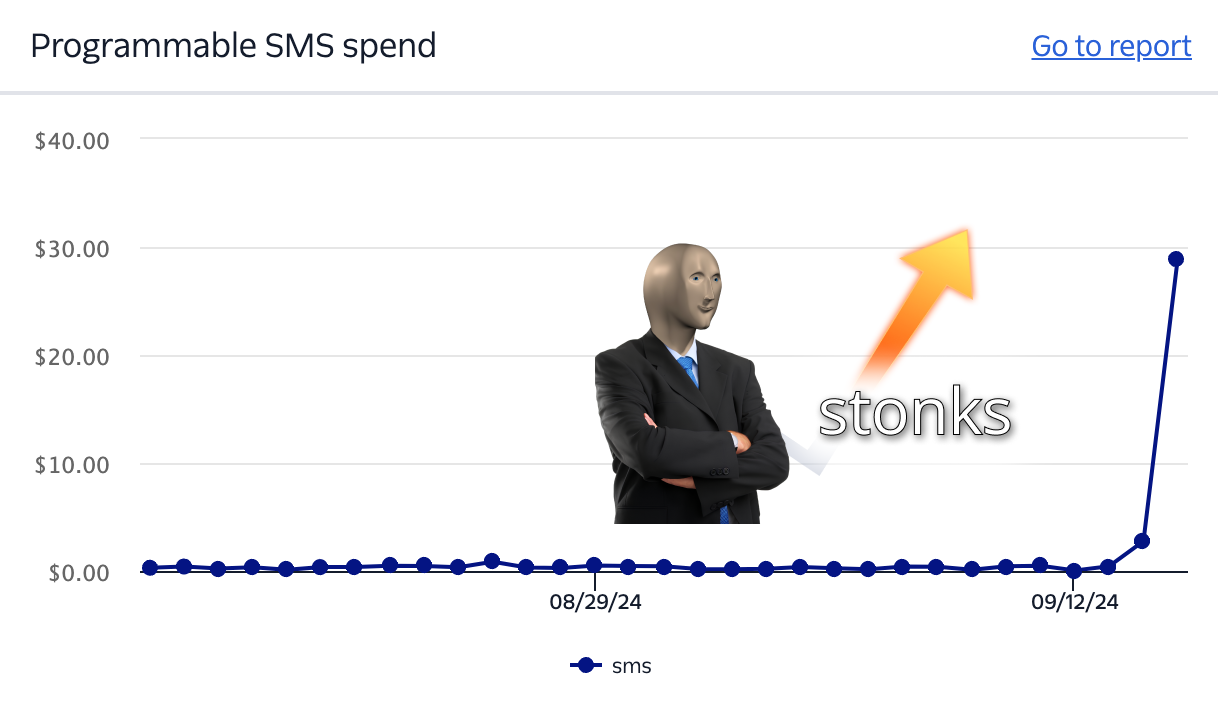
(Yes, we meticulously traced the stonks guy at 4am for the bit.)
Then we learned the hard way that SMS is not the ideal platform for running games when we got blacklisted by several major cell carriers for being too... suspicious, or something. (Ouch :/) After this experience, we iterated on the game to offload as much game-related communication as possible into our web client.
Also, game design is hard! It took a lot of talking and iteration to ensure that everyone had the right incentives and the game was actually fun. (We ended up making some counter-intuitive game design decisions, for example, being tagged earns you points.) In-person games are hard to design and hard to bootstrap from few players.
Making a good scoring algorithm and finding reliable ways to extract profile pictures and user profiles were also fun challenges. (Plus, dealing with the quirks of a very broken QR code scanning library.)
Accomplishments that we're proud of
We ran a game on Saturday night. It started out quiet and we were worried nobody was going to participate, until the most magical moment happened: people we had never met before started streaming into the room from the staircase, answering the call of their phone.
We ended up running 12 rounds and it was an absolute blast. We spent an hour running around with others as a crowd built up and we chased elusive players such as the infamous Gregory Gu.
By the end of Saturday, over 300 hackers had already signed up.
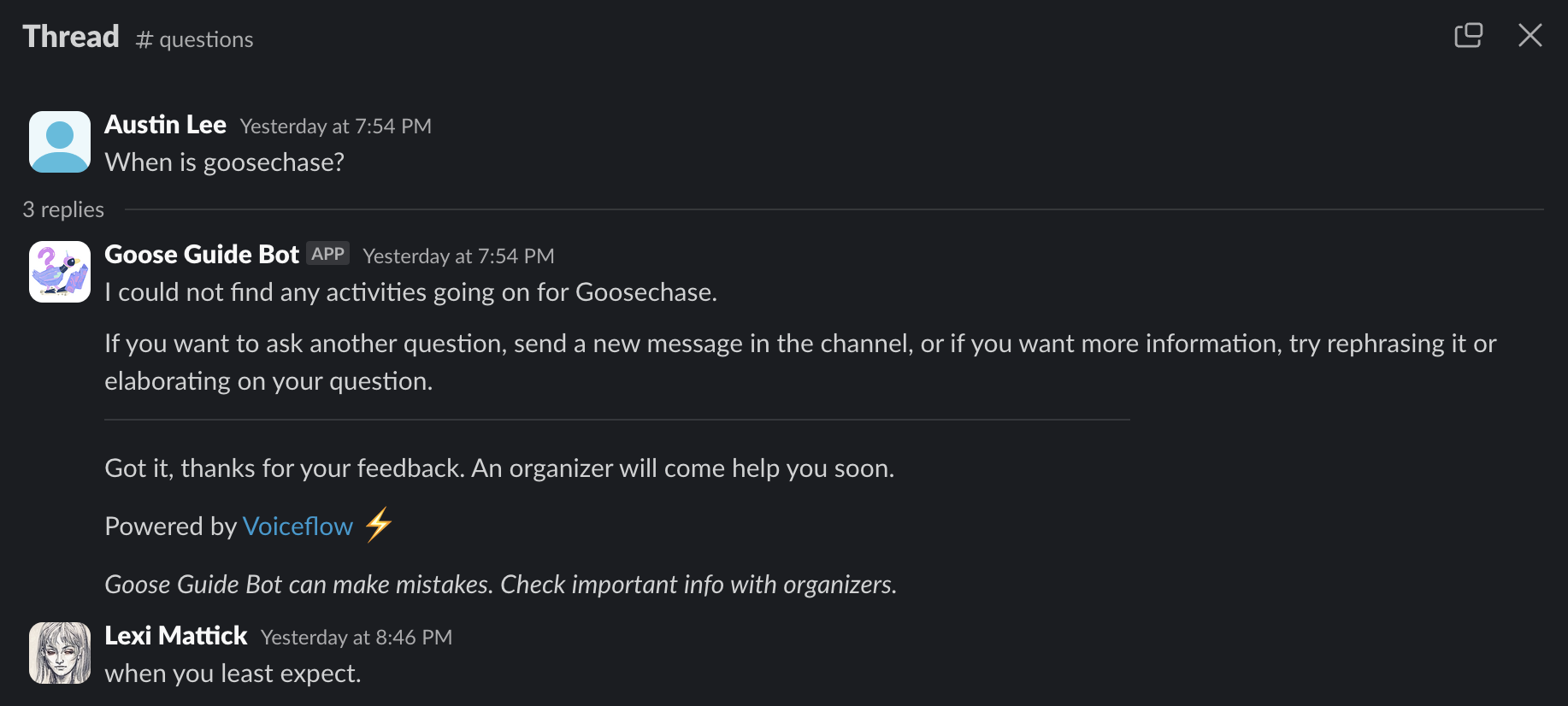
At the end of the day, it's all about the friends you made along the way. It was a great weekend :)
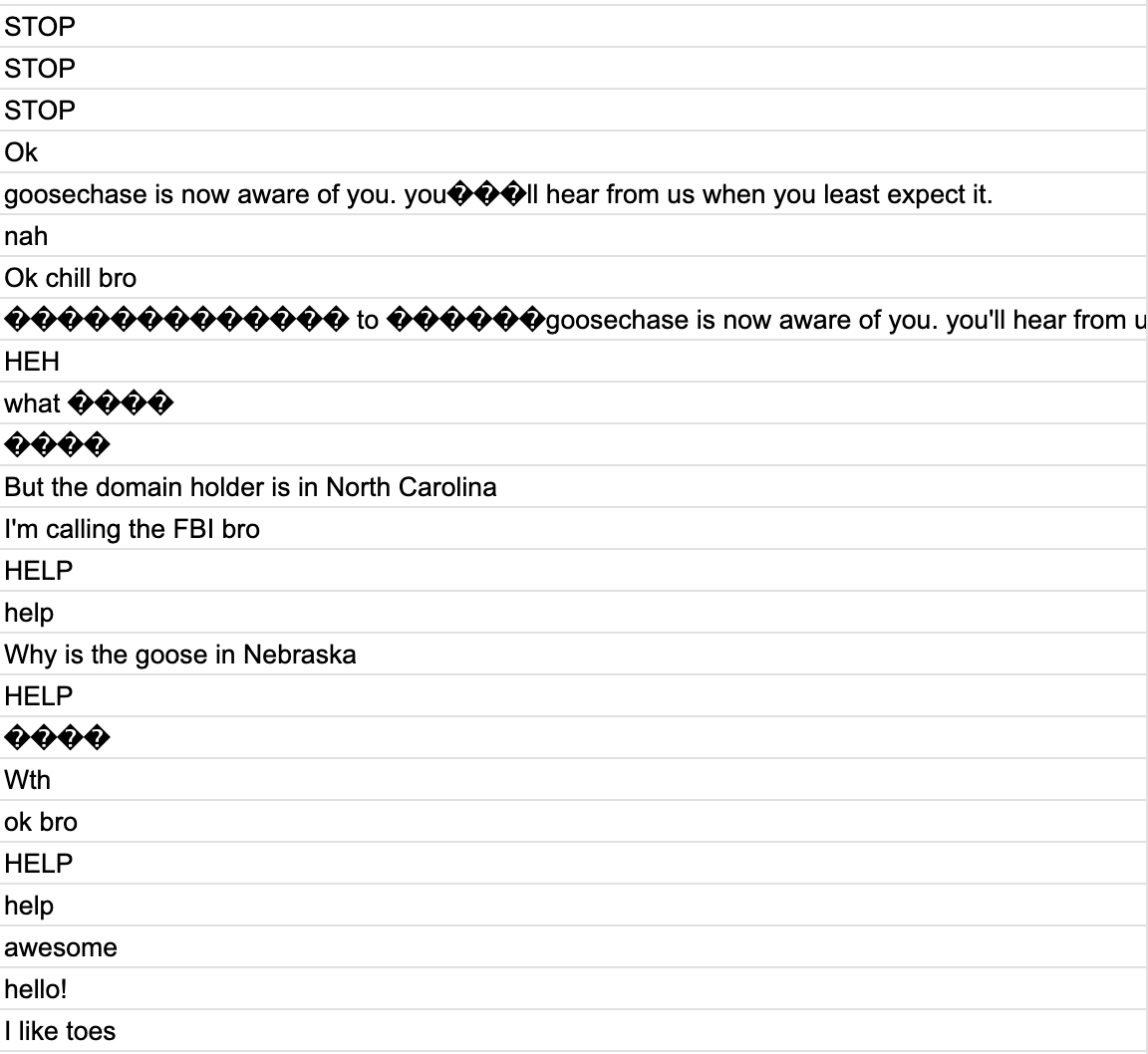
Addendum: messages you sent us
Bet you didn't know we could read these through Twilio's dashboard, huh?
Built With
- next
- node.js
- postgresql
- prisma
- twilio








Log in or sign up for Devpost to join the conversation.