Last updated on December 15, 2025
Overview
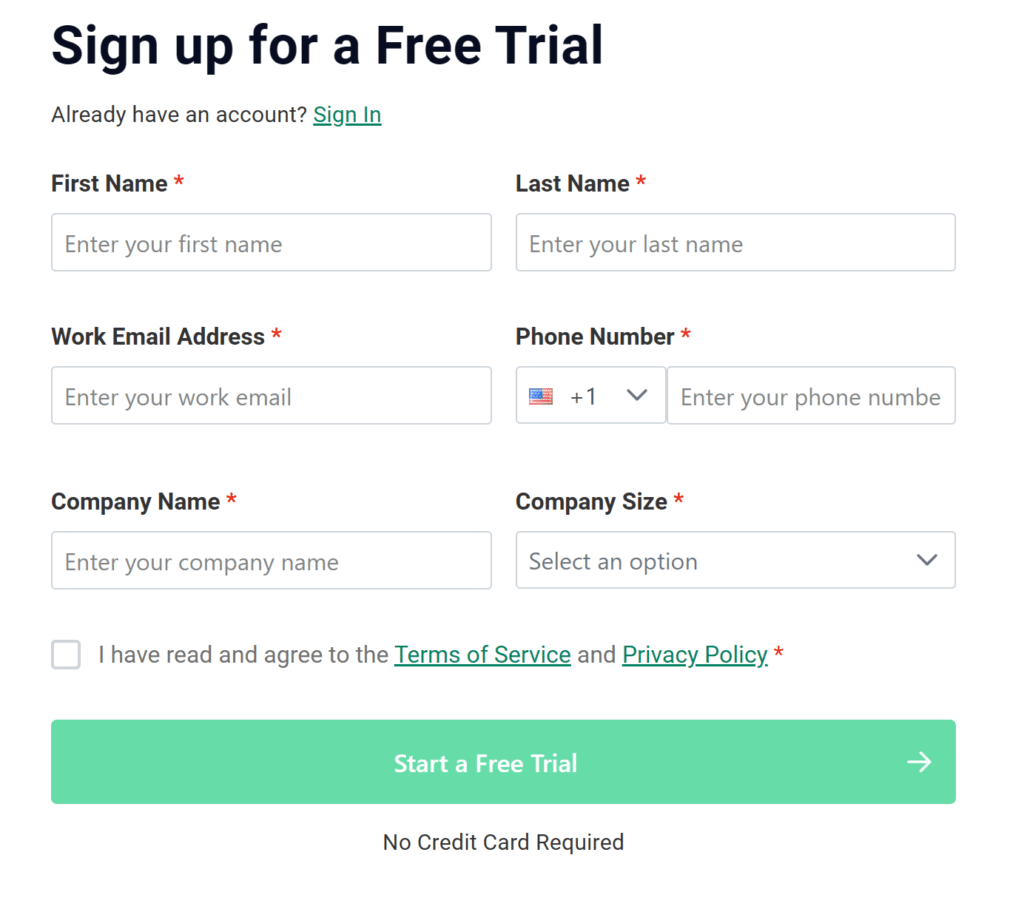
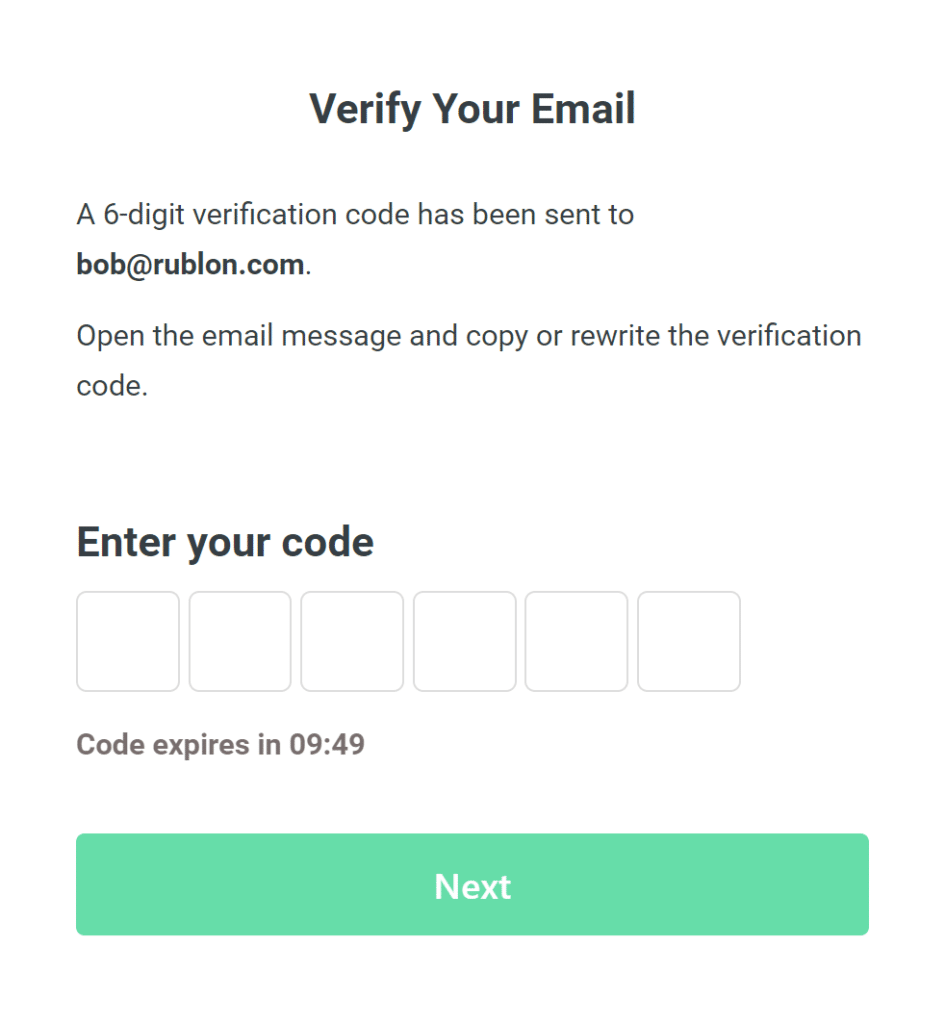
Rublon Account Registration
Note



Sign in to Rublon Admin Console


Password Reset




Configuration
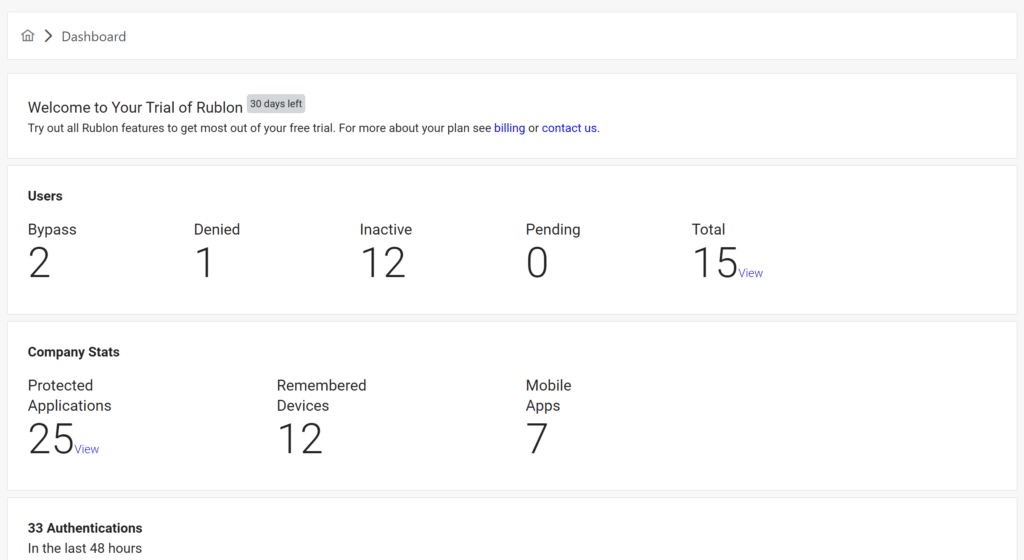
Dashboard
Applications
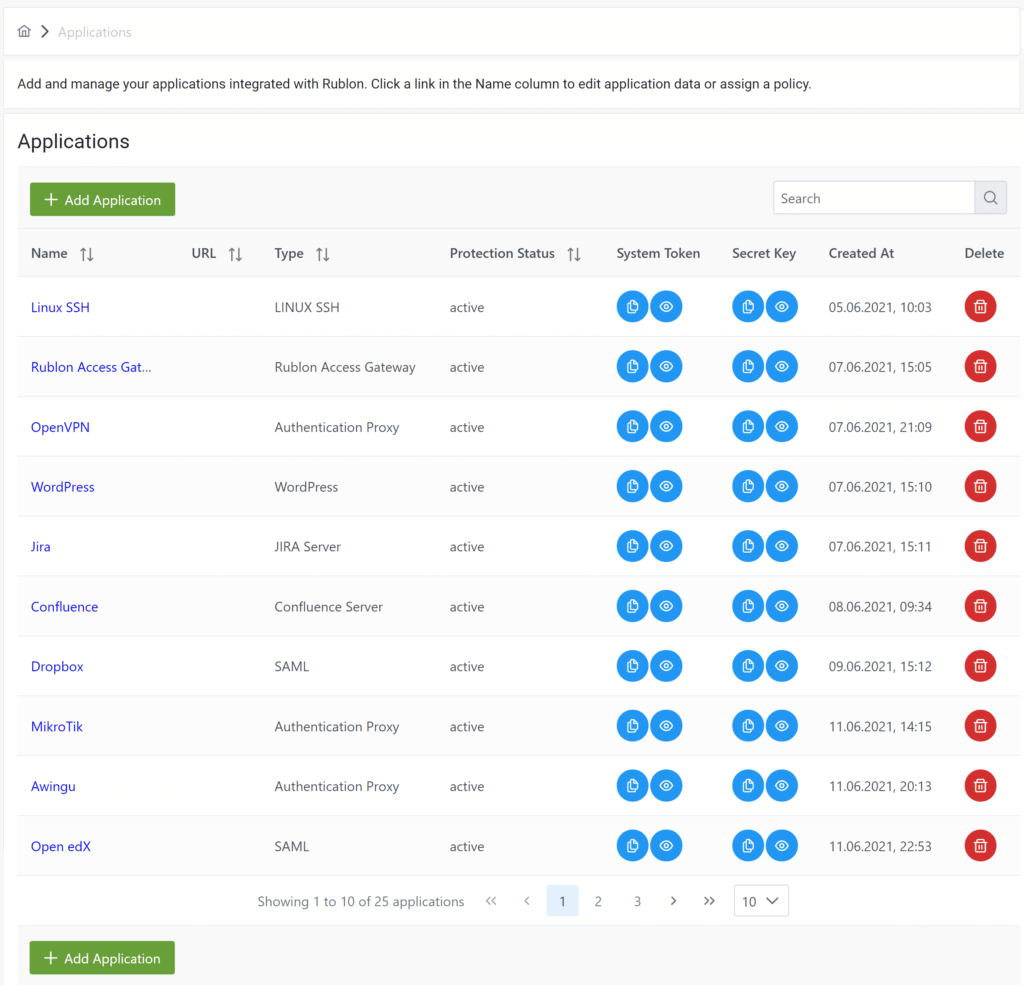
How to add an application

Note
How to edit an application



How to assign Application Policy to an application
Tip

How to assign Group Policies to groups within application

How to delete an application

Users

User Status
Search for users
How to export users to CSV


How to import users from CSV
Note


Note
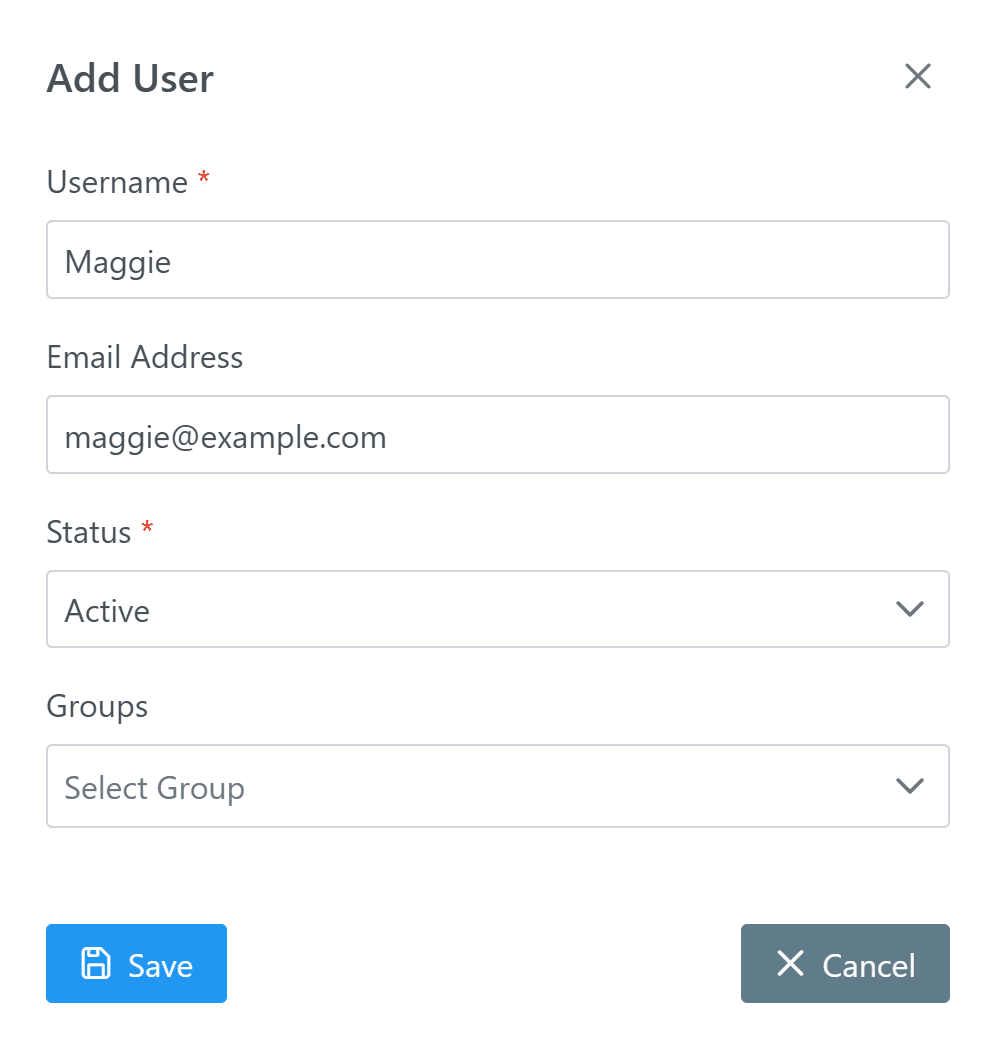
How to add user
How to edit user

How to change user status
How to delete user
How to add user phone
Note
How to delete user phone



Note
How to add user FIDO authenticator
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the name of a user you would like to add a FIDO authenticator for. You can use the search feature to find the user.
4. In FIDO Authenticators, click Add FIDO.

5. Enter a name for the key and click Add.

6. Follow the screen prompts to enroll the security key.
Note
Rublon MFA’s admin-side FIDO enrollment supports External authenticators and cloud-synced Built-in authenticators.
Examples of supported FIDO authenticators (admin-enrollable):
• Physical FIDO U2F & FIDO2 security keys (e.g., YubiKey, Google Titan)
• Cloud-synced passkeys with no shared space (e.g., Google Password Manager, iCloud Keychain)
• Cloud-synced passkeys with shared space – Learn more: Deploying Admin-Enrolled Passkeys With Enterprise Password Managers
Examples of unsupported FIDO authenticators (user self-enroll only):
• Windows Hello (TPM-backed passkeys strengthened with PIN, face, or fingerprint)
• On-device Touch ID / Face ID passkeys that never leave the Secure Enclave.
Note
At this time, administrators can enroll FIDO authenticators for user accounts only. Adding keys for other administrator accounts is not supported.
Note
How to send Enrollment Email

How to Bulk Enroll User Authenticators

Note
Note
How to add user to group

How to bulk add users to group


How to add, edit, and delete user aliases

How to add a Bypass Code for user


Directory Sync

How to synchronize users from Entra ID using Directory Sync?
How to synchronize users from other directories using Directory Sync?
Groups


Note
Permitted Groups

Using Groups to Manage Application Access



How to add group
How to add users to group
How to assign administrative units to group
How to edit group
How to delete group
Authenticators
Click the Authenticators tab to extend it and show its subtabs. Refer to the following subtabs to learn more about them.
Phones

How to add phone
How to edit phone

How to delete phone
How to send Mobile Activation Email



How to check user’s Rublon Authenticator information



Note
FIDO Authenticators
FIDO Authenticators allows you to see all FIDO U2F & FIDO2 security keys and passkeys in your organization. These authenticators are used when logging in to applications protected by Rublon MFA.
The FIDO Authenticators section depicts all FIDO authenticators in the form of a table.
Every FIDO authenticator in the table contains the following information:
- Name – the name of the FIDO authenticator
- Description – the FIDO authenticator model, including its name, purpose, or function
- Registered At – the date and time of FIDO authenticator registration
- Last Use – the date and time of the last use
- Actor – the actor (User or Admin) this authenticator belongs to
- Delete – click the trash bin icon next to a given FIDO authenticator to delete it

The following sorting, filtering, and searching options are available:
- The FIDO Authenticators table allows sorting by the following columns:
- Name
- Description
- Registered At
- Last Use
- Actor
- The FIDO Authenticators table also allows searching by the following data, thus narrowing down the results:
- Name
- Description
- Actor
Clicking a link in the Name column will show details of that specific FIDO authenticator.

How to add a new FIDO authenticator
- How to add user FIDO authenticator
- Learn how a user can self-enroll a new FIDO security key
- Learn how a user can self-enrll a new FIDO2 passkey
YubiKey OTP Authenticators
YubiKey OTP Authenticators allows you to see all YubiKey OTP security keys in your organization. These keys are used when logging in to applications protected by Rublon MFA.
The YubiKey OTP Authenticators section depicts all security keys in the form of a table.
Every YubiKey OTP authenticators in the table contains the following information:
- Name – the name of the YubiKey OTP authenticator
- Registered At – the date and time of key registration
- Last Use – the date and time of the last key use
- Actor – the actor (User or Admin) this authenticator belongs to
- Delete – click the trash bin icon next to a given key to remove it

The following sorting, filtering, and searching options are available:
- The YubiKey OTP Authenticators table allows sorting by the following columns:
- Name
- Registered At
- Last Use
- Actor
- The YubiKey OTP Authenticators table also allows searching by the following data, thus narrowing down the results:
- Name
- Actor
How to add a new YubiKey OTP authenticator
RFID Authenticators
RFID Authenticators allows you to see all RFID authenticators in your organization.
The RFID Authenticators section depicts all RFID authenticators in the form of a table.
Every RFID authenticator in the table contains the following information:
- Name – the name of the RFID authenticator
- Description – the description of the RFID authenticator (e.g., RFID card model)
- User – the user who registered the RFID authenticator
- Last Use – the date and time of the last authenticator use
- Registered At – the date and time of RFID authenticator registration
- Delete – click the trash bin icon next to a given security key to remove that security key

Clicking a link in the Name column will show the details of that specific RFID authenticator.

How to add a new RFID authenticator
Policies

Global Policy
Custom Policies
How to create new policy

Note
Policy Sections
Authentication Methods


The Hide deactivated authentication methods in the Rublon Prompt. checkbox controls whether authentication methods deactivated in this policy are hidden entirely from the Rublon Prompt or simply shown in a disabled (grayed‑out) state.
- When checked, any method you have deactivated will not appear at all in the Rublon Prompt.
- When unchecked, deactivated methods remain visible but are displayed in a grayed‑out, non‑selectable state.

Authorized Networks
# this comment will be ignored
# 192.168.1.1, 10.0.0.2 - these IPs will be ignored
202.201.200.192
17.5.7.8,17.5.100.0-17.5.100.50, 17.5.100.0/24
203.100.100.5

Note
Remembered Devices

Note
Note
Remembered Devices

Administrators

Administrator Roles
How to add admin


Resend Setup Email

How to add admin phone
How to delete admin phone
Note
How to add admin to administrative unit
Administrative Units


Using Administrative Units to Manage Admin’s User Management Privileges
How to add administrative unit

How to add admins to administrative unit
How to edit administrative unit
How to delete administrative unit
How to assign administrative unit to group
Admin Sign-in Settings
Admin Sign-in Settings allows you to manage administrator sign-in and authentication settings globally in your organization. Decide which authentication methods administrators can use to sign in to the Rublon Admin Console and set the time limit for Rublon Admin Console sessions to ensure NIST AAL3 or NIST AAL2 compliance.

All settings in the Admin Sign-in Settings tab are global, which means they apply to all administrators regardless of their administrator role. When you edit these settings, make sure you do not lock yourself or other admins out of the Rublon Admin Console. To help prevent that, the console enforces three safeguards:
- An administrator cannot deactivate the authentication method they used to access the Rublon Admin Console on their last sign-in. To deactivate that method, the admin must signs out of the Admin Console and signs in again with a different method.
- If Administrator B deactivated the authentication method that Administrator A last used to access the Rublon Admin Console, and Administrator A is still signed in the console, Administrator A will see a red-box warning about that and will not be able to save changes until they check this method again.
- If an administrator changed the available authentication methods and wants to save the changes, a confirmation window appears, asking them to ensure these changes do not block themselves or other admins from accessing the Rublon Admin Console.
Session Timeout
Set the time limit for Rublon Admin Console sessions. Administrators will be signed out automatically when the time expires.
- 15 min (compliant with AAL3, default)
- 30 min (compliant with AAL2)
Note that regardless of activity, re-authentication is required after 12 hours.
Reports
Authentications

Authentication Logs


How to export authentication logs
Audit Logs


How to export audit logs?
Note
Phone Logs

How to export phone logs?
Settings

Details
User Enrollment
Email Domain Allowlist
Third-Party Apps
Customization
Logo
Failed Authentications
API
Default Language
Billing
Overview
Note
How to start a Rublon Business subscription
Phone Credits

How to buy Phone Credits
Invoice Details

Profile Page
Note

Sign out
