Flood of emails to reset your Instagram password: what happened and how to protect your account
Avalanche of emails to reset your Instagram password: what happened, what real risks there are and how to secure your account in a few simple steps.

Avalanche of emails to reset your Instagram password: what happened, what real risks there are and how to secure your account in a few simple steps.

TikTok is flooded with fake tutorials that install malware and steal passwords. Learn how they work and what you can do to protect your personal data.

Roblox requires age verification via facial recognition or ID to use the chat feature. Here's how the age-based system works and what the implications are.

Trust Wallet extension attack: millions stolen, what went wrong, how the platform is responding, and what you can do to protect your cryptocurrencies.

Discover the pros and dangers of free VPNs, why many are risky, and how to choose a secure VPN to protect your privacy.

Spotify is considering mass access to its catalog after Anna's Archive copied 99,6% of its music, raising concerns about rights and piracy.

Television and the press lead in media responsibility in Spain, while social networks and YouTube are sinking in transparency, data and public trust.

Discover the ethical dilemmas of digital twins: identity, privacy, legacy, and responsible use in business and society.

Discover how to protect digital twins in OT/ICS, their risks, cybersecurity advantages, and the best safeguards for critical infrastructures.

Learn what incognito mode really does, how to activate it in each browser, and how to improve your privacy while browsing the internet.

Discover how Edge AI reduces latency and protects your privacy in the cloud, with real-world examples in industry, healthcare, and smart homes.

Viewing the country of an account on X: steps, accuracy, VPN warnings, and privacy. Implications in Spain and the EU. Learn how to use the new label.

Iberia is investigating an unauthorized access to exposed customer data. What was leaked, what measures have been taken, and how to protect yourself.

Gmail can use your emails to train AI. What changes, privacy risks, and how to disable it step by step in your account.

This is how emotional chatbots are growing: benefits, risks, and what Europe is preparing for safer use in mental health and support.

The Louvre's camera server used "LOUVRE" as its password. Audits and system failures explain the jewel theft. Everything that is known.

Configure your privacy settings on social media, avoid risks, and protect your data. A complete guide with settings, laws, and best practices.

A guide to erasing your online past: the right to be forgotten, search engines, social networks, and browsers. Key steps and useful resources to protect your digital footprint.

A US judge bans NSO from WhatsApp and reduces the fine from $167 million to $4 million. Key points about the ruling, reactions, and impact on Pegasus.

OpenAI and Ive's gadget is in trouble: technical, privacy, and cost issues call into question the 2026 launch plan.

WhatsApp is testing Writing Help, a voice answering machine, and new settings to limit Meta AI in chats. This is how your messages are changing.

Google confirms data access via Salesforce. 2.500 billion emails at risk of phishing. Key measures to protect your Gmail.

If the question arises Who visits my TikTok? Do not worry in this publication we explain how you can discover it.

There are times when we have to use public computers in various places, such as Internet cafes, libraries, hotels, airports, laboratories...

Why would I want to hide my windows and running programs? It is perhaps the question you are asking yourself, well…

Do you notice anything different? Does it look prettier? I hope so because this week I have been doing the…

Facebook with its billions of users is without a doubt the most important social network, in terms of…

Spam is one of the most hated things on the Internet, it is an unwanted visitor that arrives every day...

A mistake that we usually make when installing applications on our Smartphone is not reading the permissions that a…

There are unavoidable moments when we have to step away from the computer for a moment, and during that time we feel the need to hide…

Every user has that sensitive information that they do not want to be seen by outside eyes, we are talking about private files...

Private browsing or “incognito mode” of browsers is perfect for not leaving traces of the sites you have…

The most accurate title for this publication should be “How to revoke access to applications in Gmail”, because that…

Computers on the Internet are identified by the IP address, making an analogy, it could be said that the IP is...

We well know that when installing an application on Facebook, it asks us for certain permissions to access our information, by…

SecretFolder is one of those free applications that should not be missing from our computer, it is a small but…

There are times when we need to send confidential information, whether for work or friends, but there is fear...

We all have our sensitive files, we talk about those private files that we don't want anyone to know about their existence and...

The Internet is so vast and uncensored, thousands of adult sites are just a click away, so…

On several occasions we find ourselves in the need to get away from the computer for a few moments, and the first thing I know…

On Facebook everyone expresses themselves as they want and shares what they want, but there comes a time when…

If you think it's time to sell or donate your old PC, it's also time to erase…

Encoding Decoding is a small but powerful free tool, very easy to use, that offers you…

Surely you already know Likelo.com, the free application that allows you to get many likes or likes on your Facebook profile, already…

We all have important data that we often delete, because they are private and we do not want them to be seen by third parties...

A long time ago we commented on the privacy problem with emails on Facebook, referring to what can be found…

Facebook was born with the idea of being a meeting place with old friends, contact with relatives who live...

Whenever we use the computer, there is a record of all the programs that we have executed, the recent documents, the files that...

With so many applications to which we daily give authorization to access our personal information on Facebook, it is recommended…

We well know that at all times we always leave traces of the use of the PC, a lot of information that can compromise us, especially...

If you are a user of public computers, whether at work, Internet cafe, school or university, then Anti Tracks is…

Creating a temporary and anonymous email can be very useful, for example, to access existing links in forums,...

There are hundreds of alternatives to protect our information, ranging from the simple camouflage of files, to the encryption of folders,...

Spy programs or Spyware obtain passwords, usernames and all kinds of valuable personal information from their victims,…

Locking the computer is so simple that it is enough to press Win+L, but we know that this method is not the…

If you need to send secret and confidential messages by email, with extreme security, which is what you are always looking for, then…

PrivaZer is an interesting free tool that comes to add to our kit of maintenance utilities, essential for everything...

The technique is called 'Steganography' and it consists of writing hidden messages in such a way that no one except the sender and…

There are times when we delete an important and private file, with the fear that it may be recovered and…

One of the most common problems that every user faces, especially those that we are used to visiting…

If your computer is not exempt from foreign gazes, and you have the need to get away from it momentarily, leaving all…

ClearkLock is a free utility designed to maintain our privacy, ideal for those times when we temporarily move away from…

It is common knowledge that while we surf the net, we are leaving traces of everything we do during…

Every user has his secret files and that only he knows them, so to deprive them of foreign eyes by…

Going to serve yourself a coffee and leave the computer in sight and availability of third parties, can be a serious...

Every time we insert a USB memory (flash memory, pen drive...) to the computer, information is stored in the Windows Registry...

When it comes to sharing confidential information, of extreme privacy, the first way that comes to mind…

KeyFreeze – BlueLife is the name of this useful free application, which is designed to lock your keyboard and…

AppAdmin is a very good free application, very useful, that comes to enhance the privacy and security of our…

And it is that there are so many existing applications to encrypt files (understood as placing a password), that to be honest, it…

We well know that when we delete a file, either by emptying it from the Recycle Bin or directly (Shift+Del);...

One more year with you my reader friends, I thank you for always being aware of the blog and…

Security and privacy, two relevant words that should above all be a priority for all of us. Even more so…

It is common knowledge that when we delete a file, folder or document, either by sending it directly to the Trash…

The Word document format (.doc – .docx) is used all over the world. Many companies use it to…

Young children, by nature, tend to be curious and rummage through all the things within reach...

Hiding running windows/programs is quite useful, if for example we use our computer surrounded by many people, where our activities…

Before I start to describe to you the details about today's free app; Free File Camouflage, if I may…

If what you need is to disable access to USB ports in Windows, either because you own…

And it is that Facebook has become so addictive for many, that even at work they are always connected...

Addictive Tips besides being an excellent IT and Technology blog, is also developing free applications, many of you…

TheLetterEncrypter is a free application exclusively designed to generate encrypted secret messages, from the text you enter in your…

I tell you friends that I have finally found the ideal application to prevent someone from entering my computer in…

We know that when you delete a file in the usual way, it is not permanently deleted. This means that always...

It is at work for example, where we are prohibited from using programs not related to the company. Is…

There are times when we must temporarily absent ourselves from our PC, leaving the equipment exposed to outside eyes, then what…

The downside of having a family computer, that is for us, siblings, parents and even sometimes for...

Taking advantage of the fact that Facebook has millions of users and that it grows more every day, cyber-criminals are on the prowl 'intelligently' infecting,…

Methods to protect our files and/or folders, we have several available; As we well know, the most common are: encrypt, camouflage, block,…

Hiding folders and running applications can be very useful to maintain our privacy, in the event that…

Privacy is one of the most relevant aspects that every user needs, since the fact of keeping our files…
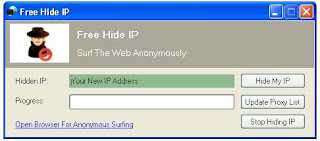
As a concept and as we already know, an IP (Internet Protocol) address serves to identify each computer...