New Features!
Welcome to the new version of our Vulnerability Management platform!
This update introduces granular filters by date and severity in all of our sections (vulnerability, assets and workspaces), making it easier to locate vulnerabilities and track your team’s progress.
We’ve also added weekly reports that can be scheduled, helping teams better understand how their work is evolving over time and get a bigger picture of their attack surface.
And last but not least: after months of development, we’ve implemented bidirectional integration with Jira, so now you can seamlessly communicate between Jira and Faraday.
Let’s get right into it!
Highlights
Date Range Search
Severity Range Filter for Vulnerability Imports
Update: CVSS4.0 Support for Vulnerability Templates
Last detected date for Vulnerabilities
Weekly Workspace Security Reports (only paid-licenses)
Asset Deduplication Process (only paid-licenses)
Enhanced Jira Integrations: Bidirectional Status Sync
Notifications Log Search
Date Range Search
A new Date Range search operator has been added for date-type attributes. This operator allows you to easily filter results between a specific start and end date using a visual calendar picker. This enhances filtering for vulnerabilities (creation date – update date) and workspaces (end date – start date) across the platform. This can also be applied to Vulnerabilities inside a given asset or workspace.
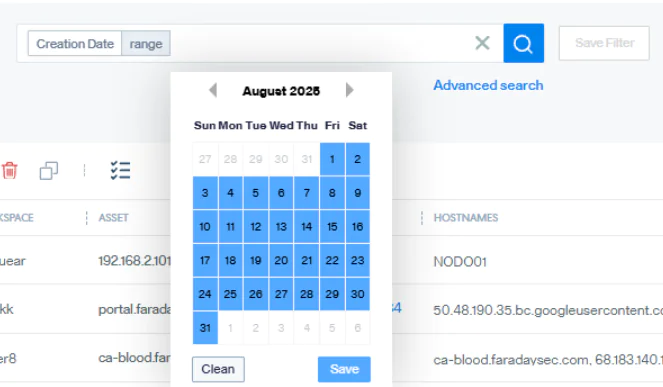
This feature is especially useful for Pentest Team and Reporting use cases, allowing you to identify which findings were detected within a specific date range. This makes it easier to decide whether or not to include them in a report.
Severity Range Filter for Vulnerability Imports
A new severity range selector has been added to all vulnerability import methods (CSV, Agents, Cloud Agents, and Schedulers). This feature allows you to define a custom range of severities to import using an interactive slider.
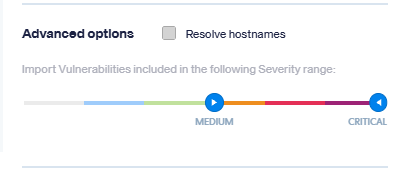
This feature is especially useful in Vulnerability Management, helping teams streamline triage by ignoring low-severity findings
UPDATE: CVSS4.0 Support for Vulnerability Templates
Vulnerabilities in the knowledge base now support CVSS4.0 vector. Creation of templates now allows you to input the last CVSS version score for this vulnerability.
Last Detected date for Vulnerabilities
A new Last Detected date field has been added to vulnerabilities, providing better visibility into when a specific threat was most recently observed on an asset.
Key Functionality:
- The field is automatically set when a vulnerability is first created with an Open status.
- It is updated to the current date whenever a subsequent scan (via Agent, plugin, or file import) rediscovers an existing vulnerability.
- This field is now available as a filter in the search bar, enabling you to find vulnerabilities detected within a specific time period easily
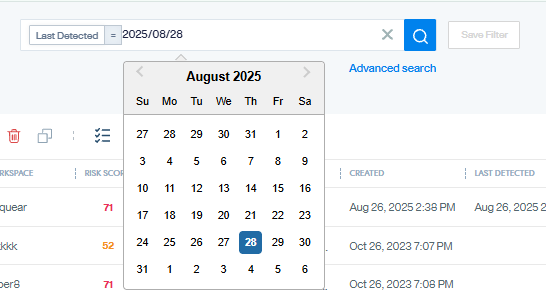
This feature is useful across use cases where vulnerabilities are repeatedly detected over time, such as Pentest Team and Reporting, PCI-DSS, Endpoint Security, and Attack Surface.
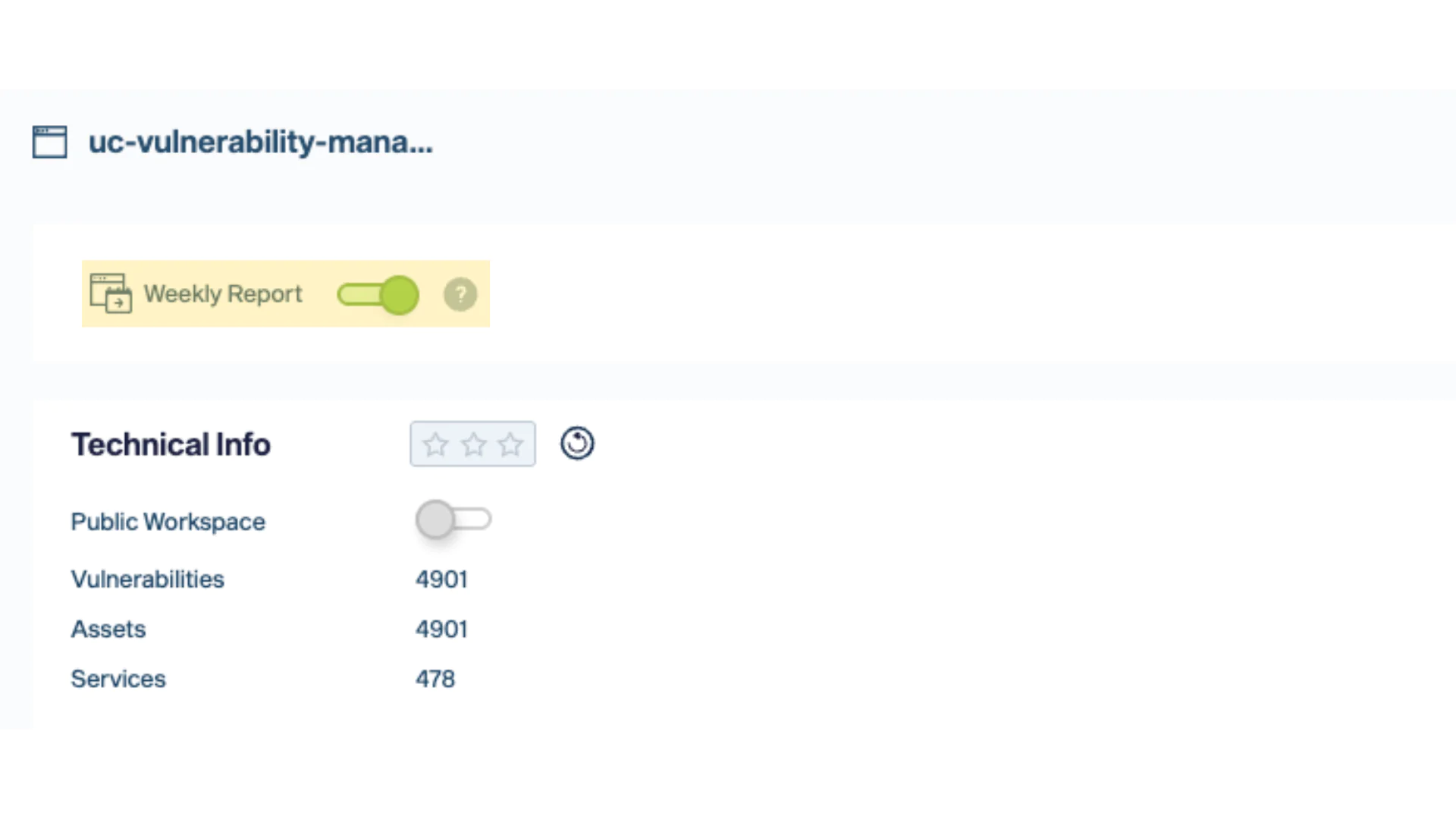
New Feature: Weekly Workspace Security Reports (only paid-licenses)
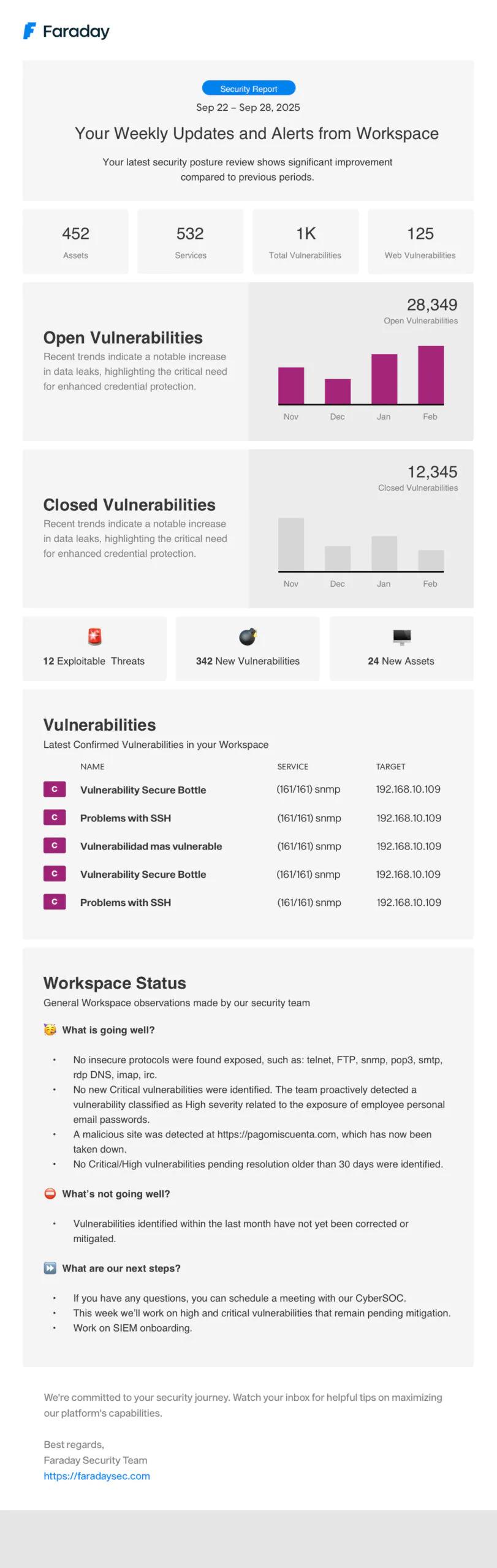
Users can now enable a weekly email with a completely redesigned report for any workspace they are assigned to, providing a comprehensive summary of the past week directly in their inbox every Sunday. A great way of making informed decisions.
The report includes:
- Key metrics: Total assets, services, vulnerabilities, and web vulnerabilities.
- Trend analysis: Month-over-month comparison charts for open and closed vulnerabilities.
- Threat summary: Count of exploitable vulnerabilities, new vulnerabilities, and new assets from the last week.
- Latest confirmed vulnerabilities.
- Security findings: Highlights such as re-opened issues, new high/critical vulnerabilities, and assets with insecure services.
How to get there:
New Feature: Asset Deduplication Process (only pro-corp)
A new automated process using faraday-manage interface has been added to merge duplicate assets within a workspace, to reduce unnecessary costs by duplicating assets
Key Functionality:
- Automatic Merging: The tool identifies assets with identical names and merges them into a single, lowercase-named asset.
- Consolidated Data: The resulting asset contains the sum of all services and a deduplicated set of vulnerabilities from the original group.
- Safe Execution: The process creates a backup of the original workspace before any changes are made for review purposes.
How to use it:
Running the following console command:
| faraday-manage deduplicate-assets -w <ws-name> |
|---|
a new workspace with the name
| ws-name_duplicated |
|---|
will be created. Original workspace is archived.
to instantly see all vulnerabilities marked as fixed in that date range.
Enhanced Jira Integration: Bidirectional Status Sync
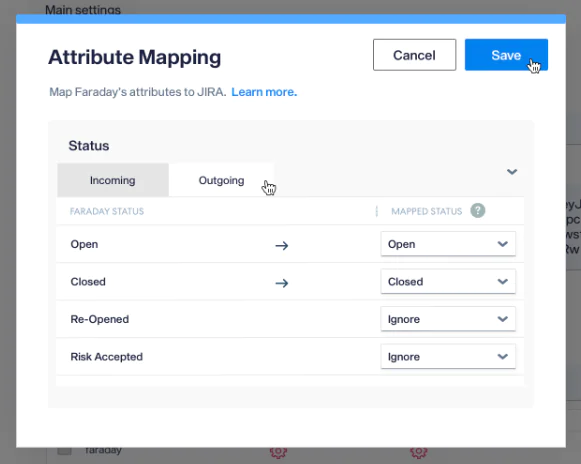
The Jira integration now supports bidirectional synchronization of the Status field, enabling seamless workflow management between Faraday and Jira.
Key Improvements:
- Outgoing Sync: Manual status updates in Faraday (e.g., changing a vulnerability to “Closed”) can now automatically trigger corresponding status transitions in linked Jira tickets.
- Incoming Sync: Status changes made directly in Jira (e.g., moving a ticket to “Done”) will now reflect in the linked Faraday vulnerability’s status, ensuring consistency across platforms.
Flexible Mapping: Admins can configure custom mappings for all statuses (Open, Closed, Re-Opened, Risk Accepted) to align with Jira project workflows. Invalid transitions (due to Jira constraints) are handled gracefully without disrupting sync.
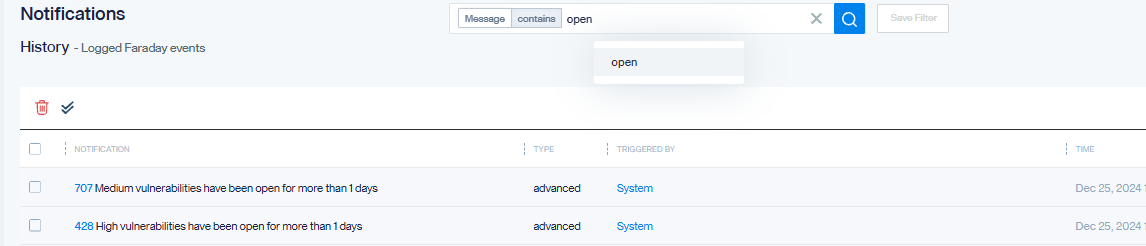
New Feature: Notifications Log Search
A new search bar has been added to the Notifications History/Log view. You can now quickly filter and find specific notifications using the following attributes:
- Notification Message
- Type ( Agents, pipelines, workspace, depending on where the notification came from)
- Triggered By
- Time
Simply use the search bar with the placeholder “Search notifications” to refine the log based on your criteria.
This feature is especially valuable for clients with large teams. It enables auditing of actions within the platform, giving Project Managers a powerful way to track performance.
Faraday v5.16 is designed to give your team control and clarity over fundamental tasks like tracking your team’s work and the entire vulnerability management process—helping you focus on what truly matters.
Your feedback is key: write to us at [email protected] and help us keep building a platform tailored to your needs.
See you next time!
¡Nos vemos la próxima!
Documentation:
Homepage
Documentation
Download
Issue tracker and feedback
Frequently Asked Questions
Twitter
Try our Quick Tour


