Prevent PII Leaks Before They Happen – Right in Your IDE
Stop Oversharing & Overlogging at the Source
HoundDog.ai’s Privacy by Design Code Scanner helps organizations proactively detect and prevent the overexposure of sensitive data in high risk mediums that could lead to privacy violations. The scanner embeds privacy into every stage of development, from IDE to CI.
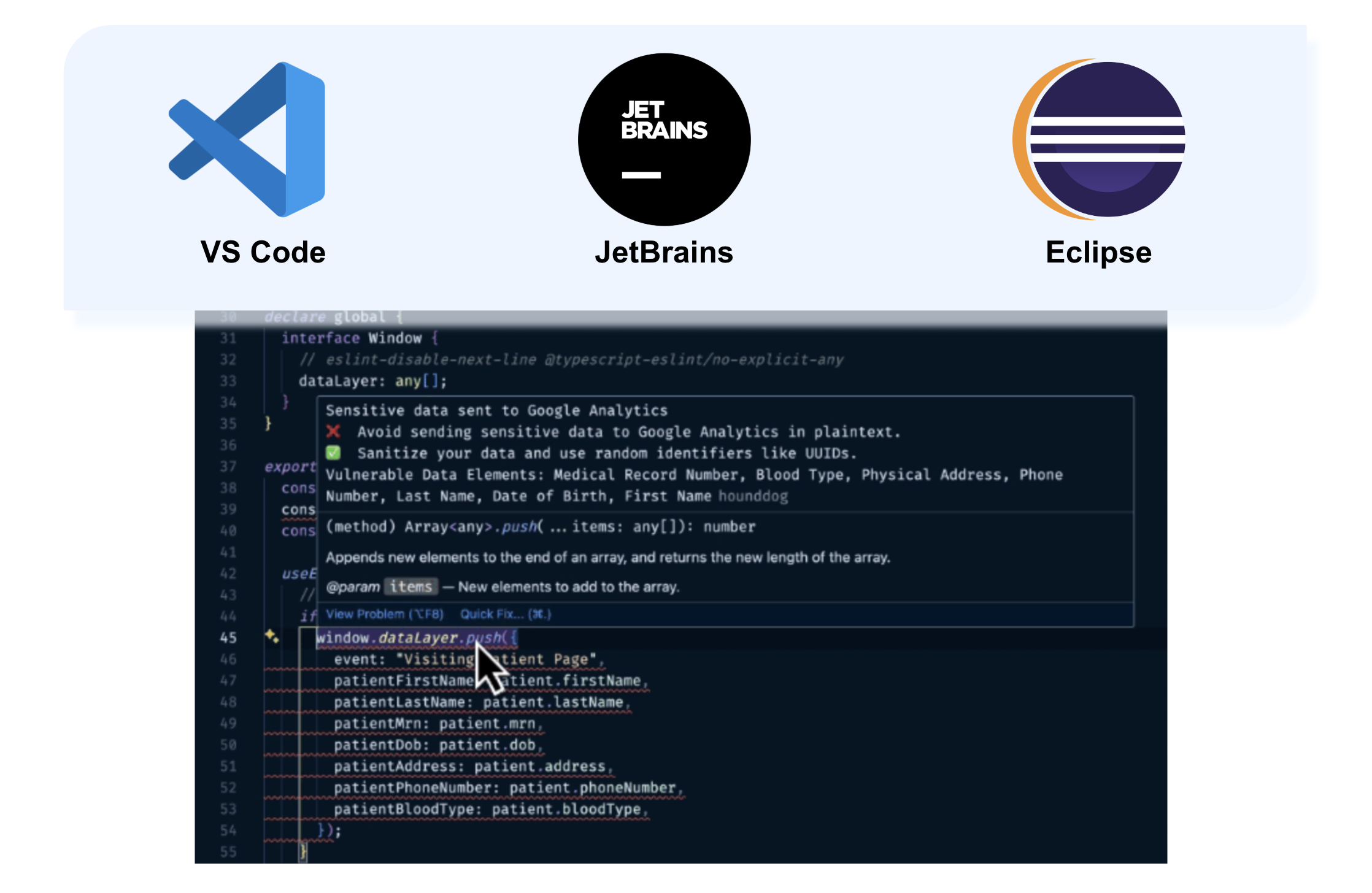
HoundDog.ai’s IDE extensions enable proactive detection of sensitive data leaks at the earliest stages of development. Available for VS Code, JetBrains, Eclipse, and now Cursor, our plugins identify sensitive data handling risks and provide simple remediation workflows before code is pushed to GitHub, GitLab, Bitbucket, or other source code management platforms. Designed to catch unintentional mistakes by developers or AI generated code, the scanner flags exposures of Personally Identifiable Information (PII), Protected Health Information (PHI), Cardholder Data (CHD), and authentication tokens across often overlooked surfaces such as logs, files, local storage, third party SDKs, and AI specific mediums like LLM prompts. This enables true privacy by design at the code level.
Key Features
🔍 Workspace-Wide Scanning
Automatically scans your entire open workspace to detect leaks of PII, PHI, or authentication tokens in LLM prompts, logs, files, cookies, local storage, and third party SDKs (such as Datadog, Sentry, Segment, and more).
🚨 Seamless Problem Integration
Detected vulnerabilities appear directly in your IDE’s “Problems” panel, making it easy to track, prioritize, and fix issues before your code is pushed to your source control management platform.
🛠 Smart Remediation Strategies
HoundDog.ai provides actionable fix suggestions, including:
✅ Omitting sensitive data if unnecessary
✅ Sanitizing data before exposure (e.g., masking, encryption, obfuscation)
Get Started in Seconds
📥 Download & Install the Plugins from your IDE marketplace or check our our documentation for more details:
Make Privacy-by-Design a Reality in Your SDLC
Shift Left on Privacy. Scan Code. Get Evidence-Based Data Maps. Prevent PII Leaks in Logs and Other Risky Mediums Early—Before Weeks of Remediation in Production.