SecuX leverages Physical Unclonable Function (PUF) technology to deliver military-grade hardware security solutions to users worldwide. From personal wallets to enterprise infrastructure, every cryptographic key is rooted in an unclonable physical fingerprint—truly eliminating supply chain risks and insider threats.

Your Hardware Fingerprint
Description: Every silicon chip has a unique physical structure.
PUF technology reads this microscopic difference to generate an
unclonable hardware fingerprint. Not even manufacturers can
replicate the same key—it's guaranteed by physics.
Keys Are Born, Not Injected
Traditional hardware security modules require key
injection during manufacturing, creating theft risks. SecuX keys
are "born" with the device—never written or stored. Your device
is unique from day one, completely eliminating supply chain
attack vectors.
Control Your Digital Assets
No centralized custodians. No third-party trust
required. SecuX keeps your private keys entirely in your hands—
stored in your hardware, protected by physics. This is the
freedom blockchain was meant to deliver.

● Private keys are injected during manufacturing, creating
heft risks.
● If the manufacturer is compromised, all keys are exposed.
● Private keys stored in software can be extracted by hackers.
● Risk: Single point of failure, complete collapse.
Connected Across Continents. Committed to Local Excellence.
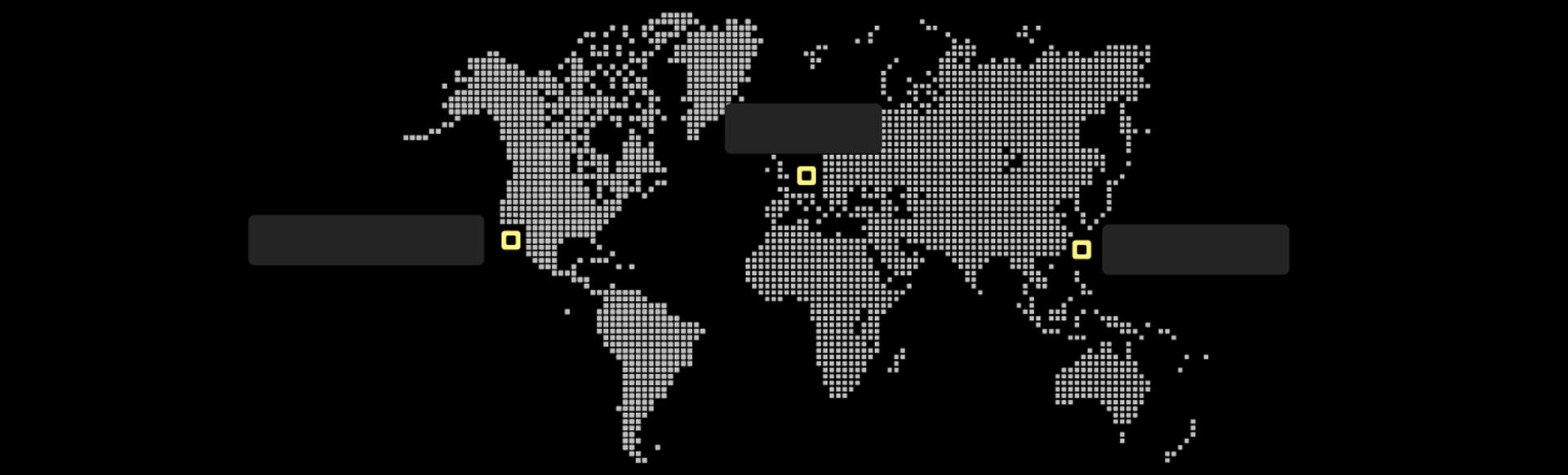
Global Headquarters
Europe Office
Americas Office

Role: Global R&D, Manufacturing, and Marketing Hub
Functions: Product innovation, quality control, global strategy

Role: Americas Sales & Service Center
Functions: Sales, distribution, partner management, local support

Role: Europe Sales & Service Center
Functions: Sales, warehousing, distribution, European market
development
Stay ahead with insights on cybersecurity trends, challenges, and solutions to ensure robust protection for your digital.