10 mins read
Organizations of all sizes can outsource their management of security devices and systems to a Managed Security Service Provider (MSSP)....
3 mins read
Organizations often need cybersecurity-certified IT professionals who can design, develop, implement, and manage information security programs at an enterprise level....
3 mins read
To become certified CCSK means that an IT professional has passed examinations for the Certificate of Cloud Security Knowledge (CCSK)....
4 mins read
The National Security Agency (NSA) is the most important intelligence agency in the United States. The NSA’s mission is to...
3 mins read
REvil was a Ransomware-as-a-service (RaaS) ransomware attack that affected a number of larger corporations and famous individuals. Read this article...
3 mins read
The AWS Certified Security – Specialty certification program provides skills and knowledge essential for managing the AWS platform securely. Learn...
4 mins read
The CRISC (Certified in Risk and Information Systems Control) certification is a qualification that shows proficiency in risk management. It’s...
3 mins read
The Colonial Pipeline Ransomware Attack was a major ransomware attack perpetrated against the oil and gas company, Colonial Pipeline, in...
3 mins read
The Ryuk ransomware is a strain of malware that attempts to infect and encrypt victims’ files, rendering them inaccessible to...
4 mins read
The Computing Technology Industry Association, abbreviated as CompTIA, is a U.S.-based nonprofit association formed to provide professional certifications in the...
3 mins read
AdamLocker ransomware, or RW.adm_64, is a screen-locking virus designed to prevent access to a computer system and rename the files...
3 mins read
SHA-256 is an algorithm used for hash functions and is a vital component of contemporary cybersecurity. It is part of...
3 mins read
Conti ransomware first emerged in 2020. It uses a ransomware as a service (RaaS) model in which a malicious group...
4 mins read
Crypt888, also known as Mircop, is ransomware that encrypts files on desktops, downloads, pictures, and documents with RSA algorithms. The...
3 mins read
AutoLocky is ransomware written in the popular AutoIt scripting language. It uses strong RSA and AES ciphers to encrypt files...
3 mins read
XiaoBa is a type of file-encrypting ransomware that runs on Windows and encodes victims’ files using RSA and AES algorithms....
5 mins read
The 2021 ransomware cyberattack on U.S.-based software solutions company, Kaseya, is known as the Kaseya ransomware attack. The attack affected...
3 mins read
On March 13, 2002, the ExecuPharm ransomware attack was used to encrypt and steal corporate and employee data of ExecuPharm,...
3 mins read
DarkSide ransomware, first discovered in August 2020, is used to perform sensitive data theft and send threats to reveal that...
4 mins read
LogMeIn Rescue is a software-as-a-service (SaaS) solution that offers remote desktop software and communication technology support. Founded in 2003 as...
6 mins read
LastPass is a cloud-based password manager that stores users’ login information online in a secure database and allows users to...
3 mins read
End-to-end encryption (E2EE) involves encrypting data and information between sending and receiving devices, so no other interceptors without the correct...
4 mins read
Arctic Wolf Networks (AWN) is a cybersecurity company offering cloud-native managed security operations solutions as an alternative to a traditional...
6 mins read
Fortinet is a cybersecurity vendor with two decades of experience and an extensive stack of solutions for channel partners, service...
3 mins read
Sucuri is a web application security company specializing in comprehensive website security for individual sites up to enterprise web content...
5 mins read
Imperva is a cybersecurity company focused on protecting web applications, APIs, data, cloud networks, and edge networks for business clients....
4 mins read
Barracuda Networks is a multinational cybersecurity company specializing in email and web security with industry-recognized web application firewalls (WAF) and...
3 mins read
When a system administrator finds anomalous or malicious behavior within network traffic, evidence could show it is an indicator of...
3 mins read
For the cloud-first organization, Firewall as a Service (FWaaS) brings all the features of next-generation firewalls to a convenient and...
3 mins read
A brute force attack is a frequently used cryptographic method where threat actors rely on computing power to estimate potential...
4 mins read
RSA SecurID is multi-factor authentication (MFA) technology used to protect network resources, such as applications and websites. Its purpose is...
4 mins read
Contrast Security is a cybersecurity company specializing in application security testing, embedded systems, and threat prevention for organizations relying on...
3 mins read
Threatware (malware, spyware) is a category of malicious computer programs designed to harm computers. The programs are spread by cybercriminals...
6 mins read
1Password is a password management system employed by enterprises to store employee passwords. 1Password allows users to save complex, strong...
3 mins read
Any unauthorized access to a computer network, computer data, devices, or applications is considered a security breach. Typically, a security...
3 mins read
Infosec, shortened from information security, is the field of protecting digital data and information from unauthorized or malicious access or...
3 mins read
Kerberos is a computer network authentication protocol used for service requests over an untrusted network like the internet. It is...
2 mins read
HTTPS (Hypertext Transfer Protocol Secure), the secure update of HTTP, uses an authentication process to encrypt the connection between web browsers (or clients) and servers. This process overlays Transport...
9 mins read
A password manager is a software application or a hardware device used to store and manage a person’s passwords and...
2 mins read
Security orchestration, automation, and response (SOAR) is a threat management strategy that identifies security threats against organizations and responds to...
7 mins read
Password managers store passwords for both enterprises and personal users. Password management software is useful because it allows users to...
7 mins read
What is a Denial of Service (DoS) Attack? A Denial of Service, or DoS as it is often abbreviated, is...
3 mins read
Scraping is the process of using automated tools to collect large amounts of data output from an application, website or...
4 mins read
Any person or business that connects to the internet is at risk of potential cybersecurity threats. The key to stopping...
3 mins read
Reviewed by Web Webster A key fob is a physical device that uses radio frequency identification (RFID) and symmetric encryption...
10 mins read
What is phishing? Phishing is a type of cybercrime in which a hacker poses as a trustworthy entity to obtain...
4 mins read
Cybersecurity awareness training informs employees of the attack surfaces and vectors in their company and how they can avoid falling...
3 mins read
Also referred to as DNS cache poisoning, Domain Name Server (DNS) spoofing is a form of computer security hacking in...
2 mins read
A POODLE (Padding Oracle on Downgraded Legacy Encryption) attack is a form of man-in-the-middle attack that takes advantage of a...
2 mins read
A threat intelligence feed lists trends in malicious activity, typical cyber attacks, and habits of attackers within networks. Threat intelligence...
3 mins read
East-west traffic, or lateral movement, is the passage of data packets between servers, applications, and other points within a network....
2 mins read
North-south traffic is the movement of data packets that are initially entering a network from the outside. These packets may...
3 mins read
PCI compliance is the strict adherence to the guidelines of the Payment Card Industry Data Security Standard (PCI DSS), required...
3 mins read
Intrusion detection and prevention systems observe all activity within a network, keep records of that activity, and look for intrusions...
2 mins read
An attack vector is a method by which a cybercriminal attacks a computer or network. While an attack surface is...
3 mins read
Incident response is the process of preparing for cybersecurity threats, detecting them as they arise, responding to quell or mitigate...
3 mins read
Lateral movement, or lateral traffic, is a network attacker’s progression through the network once they have breached it. Lateral movement...
2 mins read
A security zone is a specific portion of a network to which certain security protocols and guidelines apply. These protocols...
2 mins read
A one-time password, or OTP, is a series of characters generated by a device, application, or online portal for an...
3 mins read
Enterprise risk management (ERM) is an ongoing business process that assesses, identifies, and plans for risks to an organization s...
3 mins read
Remediation, also known as threat remediation, is the process by which organizations address possible attacks and vulnerabilities in advance and...
4 mins read
An attack surface is an area or point at which an attacker is most likely or most able to breach...
2 mins read
A PIN code is a series of numbers, typically four or six digits, that is required by applications, networks, or...
3 mins read
Least privilege access is the principle of limiting employees’ access to only the accounts, documents, and data that they must...
4 mins read
Perimeter security is the protection of a network by monitoring and filtering the traffic that passes through it. A network...
4 mins read
A social security number (SSN) is a nine-digit number issued by the U.S. government s Social Security Administration to U.S....
3 mins read
Fraud in technology is the falsifying or stealing of information with the intention of obtaining unearned finances or sensitive personal...
2 mins read
A royalty is a legally-binding payment made by one party to another for the ongoing use of their originally-created assets,...
3 mins read
The Zero Trust Security framework is based on the concept of trust nothing and verify everything. It affirms that organizations...
2 mins read
Microsegmentation is a method for creating granular secure zones in data centers and cloud deployments down to individual workloads using...
2 mins read
A replay attack is a type of man-in-the-middle attack where a hacker intercepts a network session and reuses the legitimate...
2 mins read
Credential dumping is a type of cyber attack where a computer is breached and usernames and passwords are obtained by...
2 mins read
Privileged access management is a strategy used by enterprises to secure privileged employee access to systems and confidential information. It...
3 mins read
A cyber attack is the unauthorized access of private or confidential information contained on a computer system or network. It...
3 mins read
XDR (extended detection and response) provides a comprehensive solution for security management, endpoint detection and response, and threat intelligence. Enterprises...
2 mins read
Pwned, or Have I Been Pwned (HIBP), is a website that allows internet users to check whether their personal data...
4 mins read
What’s Geo-blocking? Geo-blocking is the restriction of access to digital content, based on your geographic location. Your location is determined...
2 mins read
Network intelligence analyzes data that passes through computer networks, filtering Internet protocol information to monitor data patterns.
2 mins read
The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
2 mins read
A Bug Bounty Program (BBP) is a crowdsourcing initiative, offered by companies or developers, that rewards individuals for identifying software bugs.
2 mins read
A Faraday cage is a metal cage or enclosure that distributes an applied electrical charge evenly across its surface, protecting anything inside.
2 mins read
WireGuard is a free and open source Virtual Private Network (VPN) software application and communication protocol. Learn more from Webopedia.
3 mins read
Data in motion, also known as data in transit, refers to data that is actively moving across devices and networks. Learn more from Webopedia.
2 mins read
A credential stuffing attack is a cyber attack method in which stolen account credentials are used to gain unauthorized access to user accounts.
2 mins read
A security operations center (SOC, pronounced sock) is a centralized unit within an organization that deals with security issues.
2 mins read
Geo-spoofing is the process of hiding a true location by making a device appear to be in a different location than it is. Learn more from Webopedia.
2 mins read
WPA3 is the third installment of the Wi-Fi Protected Access, offered by the Wi-Fi Alliance to secure Wi-Fi connections and devices that use them.
1 min read
OpenVPN is virtual private network software that provides secure private connections for organizations over different servers and locations.
2 mins read
A misconfiguration is a computing system that has been set up incorrectly, leaving it vulnerable to hackers. Learn more on Webopedia.
2 mins read
RFID hacking occurs when a hacker uses a device to rewrite or copy the information stored on a radio frequency identification (RFID) chip or tag.
2 mins read
DNS over HTTPS protects data by disguising and encrypting Domain Name System traffic as standard HTTPS website use. Learn more with Webopedia.
3 mins read
An internal certificate authority creates its own digital certificates rather than hiring an established certificate authority to make them.
SOAR is a set of security software solutions that helps security teams improve efficiency. Read more about SOAR at Webopedia.
2 mins read
Enterprise encryption software is encryption software made for the unique needs of enterprise-sized organizations. Businesses of all sizes have started...
2 mins read
Identity proofing is a detailed authentication process that businesses use to ensure their clients are who they claim to be....
2 mins read
Input sanitization is a cybersecurity measure of checking, cleaning, and filtering data inputs from users, APIs, and web services of...
2 mins read
Managed Security Service Provider (MSSP) is a technology firm that provides cybersecurity services to companies and organizations. MSSP offers a...
3 mins read
Rootkits are a collection of stealthy software that provide privileged access in an operating system while concealing their presence. Behaving...
8 mins read
A web application firewall (WAF) is a security solution that filters, tracks, and blocks Hypertext Transfer Protocol (HTTP) traffic to...
2 mins read
User and Entity Behavior Analytics (EUBA) is a comprehensive cybersecurity process that protects a company s IT infrastructure. It uses...
2 mins read
Security as a Service, or SECaaS, is a third-party IT security service that businesses can use in place of their...
2 mins read
Penetration testing, or pen testing, is a simulated security testing process conducted by an enterprise or third party “ethical hacking”...
5 mins read
A cloud access security broker (CASB) is cloud-based or on-premises security software positioned between users and cloud services. A CASB...
9 mins read
Endpoint Detection and Response, or EDR, is a form of technology that provides continuous monitoring and response to advanced cybersecurity...
2 mins read
Cyber security threat mitigation refers to policies and processes put in place by companies to help prevent security incidents and...
4 mins read
The following Cybersecurity facts provide a brief introduction, enabling students, developers, and organizations to stay updated with the latest information....
2 mins read
Threat intelligence is the knowledge of the capabilities, resources, motives, and goals of potential security threats to an organization and...
3 mins read
A threat actor is a person or entity that has the ability or intent to impact the security of other...
3 mins read
Business email compromise (BEC) is a type of corporate financial scam that specifically targets organizations conducting business abroad. This scam...
10 mins read
Cryptojacking is a cybercrime where hackers use victims’ computers to mine cryptocurrency without their knowledge through cryptomining malware. Hackers employ...
3 mins read
Zyklon is a strain of malware that first emerged in the wild in early 2016 before largely going dormant until...
1 min read
Email threat prevention (ETP) is a security prevention technique that helps minimize the risks associated with a data breach by...
1 min read
The General Data Protection Regulation (GDPR) is a regulation that sets rules related to the protection of personal data, with...
2 mins read
Devil’s Ivy is a security vulnerability that when exploited enables an attacker to remotely access a video feed and deny...
2 mins read
CrashOverrride is an industrial control system cyberattack launched in December 2016 that created a massive blackout in Kiev, Ukraine. Also...
2 mins read
Also known as mobile information management (MIM), mobile content management typically falls within the overarching Enterprise Mobility Management (EMM) philosophy...
5 mins read
WannaCry was one of the most damaging malware attacks in history. On Friday, May 12, 2017, WannaCry ransomware infected computers...
From generating strong passwords to using a password manager many security experts, business owners, and vendors contributed their very best...
1 min read
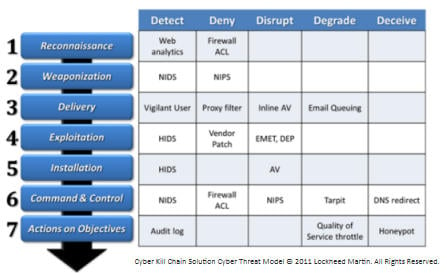
A kill chain is used to describe the various stages of a cyber attack as it pertains to network security....
3 mins read
Free VPN refers to services and tools that let you browse the Web securely and anonymously. The tools are typically...
2 mins read
A network investigative technique, or NIT, is a drive-by download computer program designed to provide access to a computer in...
2 mins read
A drive-by download refers to potentially harmful software code that is installed on a person’s computer without the user needing...
1 min read
Comodo Firewall is one of several free Internet security tools for Microsoft Windows, developed by Comodo Group. The Comodo Firewall...
1 min read
Enterprise identity management (IdM), or ID management, is the part of identity and access management systems (IAM) responsible for identifying,...
Sharing threat intelligence is an old idea that appears to be earning new credibility. Researchers, security professionals and government entities...
2 mins read
IDaaS is an acronym for Identity-as-a-Service, and it refers to identity and access management services that are offered through the...
8 mins read
Identity and access management (IAM), also known as identity management (IdM), is a combined term used to create and manage...
2 mins read
VENOM refers to a security vulnerability that results from a buffer overflow in a kernel-level driver included in many default...
1 min read
Secure delete means to overwrite data in a file when the file has been deleted from your computer. Using the...
2 mins read
Superfish is a form of adware that has the ability to hijack encrypted Web sessions and open a system up...
6 mins read
“If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you...
2 mins read
The GHOST bug is a buffer overflow security vulnerability in some distributions of Linux that can potentially enable attackers to...
2 mins read
GameOver Zeus is a sophisticated evolution of the ZeuS malware that cybercriminals created to steal usernames and passwords from users...
2 mins read
Cridex is a sophisticated strain of banking malware that can steal banking credentials and other personal information on an infected...
1 min read
Dridex is a strain of banking malware that leverages macros in Microsoft Office to infect systems. Once a computer has...
1 min read
SoakSoak is a strain of malware that leverages security vulnerabilities in a WordPress plug-in. These vulnerabilities are found in the...
1 min read
Anti-malware is software tools and programs designed to identify and prevent malicious software, or malware, from infecting computer systems or...
2 mins read
Bootkits are an advanced form of rootkits that take the basic functionality of a rootkit and extend it with the...
2 mins read
Shellshock is a bug that uses a vulnerability in the common Unix command execution shellbash (Bourne-Again SHell) to potentially enable...
2 mins read
Windows Defender is an anti-malware tool built into Microsoft’s Windows 8 and newer operating systems that is designed to protect...
1 min read
Microsoft Security Essentials is a free anti-malware tool available for Microsoft’s Windows Vista and Windows 7 operating systems that is...
1 min read
Use-After-Free vulnerabilities are a type of memory corruption flaw that can be leveraged by hackers to execute arbitrary code. Use...
1 min read
Google Project Zero is a little-known research group whose focus is finding security vulnerabilities in Google’s software products like the...
1 min read
An Apple iOS and OS x Secure Socket Layer (SSL) software vulnerability that allows a malicious user or hacker to...
4 mins read
New ways of collecting and analyzing data are creating new opportunities for companies to gain an edge over their competitors...
3 mins read
The Heartbleed Bug is an OpenSSL vulnerability that would allow malicious hackers to steal information from websites that would normally...
1 min read
A worm that takes advantage of a vulnerability in the PHP scripting language to attempt to gain access to a...
2 mins read
A strain of malware that allows unauthorized access and control of an affected system. Linux/Ebury is a backdoor Trojan and...
2 mins read
A collection of malware developed to create a sophisticated network of botnets that can distribute spam, redirect Web traffic and...
1 min read
An advanced form of ransomware that first surfaced in September 2013, attacking individuals and companies in the U.K by arriving...
1 min read
An advanced persistent threat (APT) is a targeted attack by cyber criminals or in some cases government institutions that uses...
1 min read
A technique for obfuscating the true origin of packets on an IP network in order to preserve privacy and shield...
1 min read
Hand of Thief Trojan is Trojan malware developed to enable cyber criminals to compromise Linux systems and steal user information...
1 min read
A wearable computing device which is designed to replace the need to remember passwords. The Nymi bracelet is equipped with...
1 min read
A service offered by cyber criminals that provides paying customers with distributed denial of service (DDoS) attack capabilities on demand....
1 min read
The RCMP computer scam (FBI computer scam) is a type of ransomware that attempts to trick users into paying money to have their computer unlocked.
1 min read
Citadel Trojan is malware created by a malicious code generating program. Citadel was designed to steal personal information, including banking...
A company-wide process from Microsoft for performing regular code reviews for Microsoft software products to reduce security issues and resolve...
1 min read
A term that refers to any number of security exploits in Oracle’s Java software, which has a long history of...
1 min read
An unintended flaw in software code or a system that leaves it open to the potential for exploitation in the...
1 min read
Shylock refers to a family of malware that relies on browser-based man-in-the-middle (MITM) attacks and fake digital certificates to intercept...
1 min read
The Skype worm is a strain of the Dorkbot family of malware that made headlines in October 2012. The Skype...
1 min read
A malware worm that first appeared in July 2012, targeting Iranian nuclear facilities and turning infected PCs on at night...
1 min read
An extremely sophisticated strain of malware more commonly referred to as Flame (or Flamer), although some security experts classify the...
2 mins read
An extremely sophisticated strain of malware that shares similarities with Stuxnet, although Flame is much more massive in terms of...
1 min read
DNSChanger, also referred to as DNS Changer and nicknamed the “Internet doomsday” virus, is a type of malware used by...
1 min read
Collateral hacking refers to when a company’s critical data is compromised as a result of a third party in possession...
1 min read
Short for Browser Exploit Against SSL/TLS, SSL Beast is an exploit first, revealed in late September 2011, that leverages weaknesses...
1 min read
Extensible Threat Management (XTM) is the next generation of Unified Threat Management (UTM). Where UTM describes a category of network...
1 min read
A hacker that breaks into a Certificate Authority (CA) company in order to issue fake certificates that help bogus websites...
1 min read
DigiNotar is a Dutch Certificate Authority (CA) that issues SSL (Secure Sockets Layer) and EVSSL (Extended Validation) certificates, which help...
1 min read
Morto is computer worm that spreads via the Windows Remote Desktop Protocol (RDP) and infects Microsoft Windows workstations and servers....
1 min read
Nickispy is a family of Trojan horse viruses that targets smartphones powered by the Android operating system. The most recent...
1 min read
The most widespread botnet in history, ZeuS is a Trojan horse that infiltrates computers in order to steal data by...
1 min read
Coinbit is a Trojan horse designed to steal users’ Bitcoin wallets. Coinbit targets Windows computers by homing in on the...
1 min read
Stuxnet is a family of cleverly written malware worms that primarily target SCADA (Supervisory Control and Data Acquistition) control systems...
1 min read
A mobile botnet is a type of botnet that targets mobile devices such as smartphones, attempting to gain complete access...
4 mins read
We look at why it’s essential to secure your wireless network as well as some of the most effective options...
4 mins read
American businesses spend a whopping $712 per worker, per year, in the battle against spam. Even though 60 percent of...
1 min read
In the context of information technology, a personnel security specialist coordinates network security policies to control user access to the...
3 mins read
From anti-spam tools to application firewalls there are many open source software offerings that can replace popular security software. From...
3 mins read
Ransomware is a form of malware that holds a computer system hostage until a ransom fee is paid. Ransomware typically...
1 min read
Network security is a specialized field in computer networking that involves securing a computer network infrastructure. Network security is typically...
1 min read
Software for monitoring the desktop and online activities of employees, family members, roommates or other users of a computer. Sometimes...
1 min read
The Symantec Certification Program offers certification credentials as a means to validate an person’s technical skills, knowledge and competence for...
Certification for Information System Security Professional (CISSP) is a vendor-neutral certification reflecting the qualifications of information security professionals with an...
3 mins read
What is Security Software? Security software, also called cybersecurity software, refers to any software that serves to protect a computer...
1 min read
A Firefox extension that was designed to demonstrate the serious issue of HTTP session hijacking (sidejacking). Many websites allow its...
1 min read
The CompTia Security+ certification is an internationally recognized industry credential. Security+ certifies that information security professionals are knowledgeable and experienced...
A firewall is a protective system that lies, in essence, between your computer network and the Internet. When used correctly,...
4 mins read
Cookies are messages that a Web server transmits to a Web browser so that the Web server can keep track...
4 mins read
Spam has become ubiquitous – one of the facts of life, like taxes. Until strong anti-spam laws are passed and...
1 min read
The phrase used to describe a type of purchase or license agreement associated with tangible, shipped goods, for example boxed...
1 min read
Short for cloud application, cloud app is the phrase used to describe a software application that is never installed on...
1 min read
Mariposa is the name of a malicious botnet. Dubbed Mariposa, this widespread malware campaign managed to infiltrate more than 13...
1 min read
The name given to a malicious botnet that is used to collect log-in credentials to online financial systems, social networking...
1 min read
In software development, storage testing is a part of the development test cycle that ensures the software program stores data...
1 min read
Abbreviated as ACE, access control entry is an entry in an access control list (ACL) that will grant or deny...
1 min read
Reputation-based security is an approach to system security that evaluates the reputations of the files and applications running on your...
3 mins read
What is Malvertising? Malvertising (malicious advertising) is one of the newest ways that hackers are using to attempt to steal...
1 min read
A new way for cybercriminals to lure users into clicking obfuscated URLs. With image spam the obfuscated URL is hidden...
1 min read
Also called a hyperlink trick, an obfuscated URL is a type of attack where the real URL that a user...
1 min read
Win32/Winwebsec is a Trojan horse that is delivered via a fake YouTube link that entices users to download and install...
1 min read
In virus and malware terms, a variant refers to new strains and slightly modified version of malware. Malware is often...
1 min read
(kred’it freez) (n.) Also known as a credit security freeze or security freeze. A credit freeze is a method by...
3 mins read
One step financial account holders can take to protect themselves against identity theft is to freeze their credit. The credit...
1 min read
In security terminology, a hole refers to a software or operating system vulnerability that could be exploited to compromise the...
1 min read
Any undesirable software program that is able to track a user’s system activity or gather system information and provide the...
1 min read
A program that is used to change your Web browser settings without the consent of the user. A browser hijacker...
1 min read
(card skim’ming) (n.) The act of using a skimmer to illegally collect data from the magnetic stripe of a credit,...
1 min read
A term used to describe code that has been developed to demonstrate possible vulnerabilities in software and operating systems, and...
1 min read
Short for Alliance to Save Energy, it is a non-profit coalition of business, government, environmental and consumer leaders. The Alliance...
4 mins read
Every time a new communication method becomes popular, fraudsters look for a new way to commit identity theft. One of...
1 min read
Short for “exploits”, sploitz is a slang term used to mean vulnerabilities in software that can be used by hackers.
1 min read
An extension of the Linux kernel that is used for rebootless updates. Security and source code patches are applied without...
4 mins read
The following tips will help you create a secure password that are difficult to hack. Most people have multiple passwords...
1 min read
The Conficker/Downadup worm was first tracked in November 2008 (Win32/Conficker.A) and has infected thousands of business networks and millions of...
2 mins read
Also called smitfraud, scareware, or rogue security software, this type of software is defined as malware – it is designed...
1 min read
A term used by the Symantec Security Response Centerto describe tools that are used by a hacker (or unauthorized user)...
1 min read
A term used by the Symantec Security Response Centerto refer to a plan and set of principles that describe the...
1 min read
On Unix-based platforms a command-line scanner is a scanning tool that disinfects viruses, worms and Trojan horsesin all major file...
1 min read
A type of computer virus that inserts its malicious code into executable files on a system. When the infected file...
1 min read
The action or condition that causes a virusto activate. Some viruses may activate on pre-determined user actions, a certain program...
1 min read
In channel partner terminology, accrual is a financial stipend that is provided to the sales channel by the vendor or...
1 min read
In computer viruses .dam is part of the McAfee naming convention for viruses and Trojans.
1 min read
In computer viruses .dr is part of the McAfee naming convention for viruses and Trojans. McAfee attaches the .dr suffix...
1 min read
In computer viruses @mm is part of the McAfee naming convention for viruses and Trojans.
1 min read
In computer viruses, @m is part of the McAfee naming convention for viruses and Trojans. McAfee attaches the @m suffix...
1 min read
A boot sector virus that can infect floppy boot records and hard disk master boot records. AntiExe will infect hard...
1 min read
In Web site security terminology, the word defacement is most often used to describe the changing or defacing of a...
1 min read
Also called W32/Rjump, this virus is known to open a back door on a computer that runs Microsoft Windows, then...
1 min read
The name given to a computer worm that uses Facebook’s messaging system to infect PCs in an attempt to gather...
1 min read
Clickjacking, or clickjack attack, is a vulnerability used by an attacker to collect an infected user’s clicks. The attacker can...
6 mins read
Do It Yourself SSL Guide [cont’d from page 1] Filling in the Certificate Fields As I mentioned earlier, issuing a...
1 min read
Short for Internal Hostile Structured, it is a threat defined by Symantec Corporation to mean an individual or group within...
1 min read
Short for Internal Hostile Unstructured, it is a threat defined by Symantec Corporation to mean an individual within an organization...
1 min read
Short for Internal Nonhostile Structured, it is a threat defined by Symantec Corporation to mean an individual within an organization...
1 min read
Short for Internal Nonhostile Unstructured, it is a threat defined by Symantec Corporation to mean an individual within an organization...
1 min read
Known as W32.Gammima.AG, it is a worm that spreads through removable media such as USB drives and external hard drives,...
6 mins read
wirelessThe term WPA2-PSK refers to Wi-Fi Protected Access 2—Pre-Shared-Key or WPA2-Personal, which is used to protect network access and data...
1 min read
The term SmitFraud is used to describe a type of spyware that tricks users into purchasing fake antispyware and antivirus...
1 min read
A type of computer virus that compromises a feature of DOS that enables software with the same name, but different...
1 min read
A type of malicious software that is designed to commit crimes on the Internet. Crimeware may be a virus, spyware...
1 min read
A type of computer virus that will copy its own code over the host computer system’s file data, which destroys...
In this Did You Know…? article, we discuss two areas of concern for Internet users: viruses and spyware. We look...
1 min read
Abbreviated as FIM, IBM’s Tivoli Federated Identity Manager is a model for managing identity and providing resource access. Federated Identity...
1 min read
Refers to any computer software that has restrictions on any combination of the usage, modification, copying or distributing modified versions...
1 min read
Short for Vista Service Pack 1 (SP1), Vista SP1 is a collection of end-user features, security fixes, bug fixes, improvement...
1 min read
A slang term used to describe an above and beyond, an exaggerated, an omnipresent 24/7 electronic surveillance. Not only does...
9 mins read
Vishing is a scam where attackers use phone calls to impersonate trusted figures and steal sensitive information by exploiting emotions...
4 mins read
A browser uses the Temporary Internet file to store data for every webpage you visit. Read this article to learn...
1 min read
In computer and network security terminology, a Banker Trojan-horse (commonly called Banker Trojan) is a malicious program used in an...
1 min read
A specific type of spyware that will allow a hacker or malicious perpetrator to spy on the infected computer’s Internet...
1 min read
Any malicious attacks on a corporate system or network where the intruder is someone who has been entrusted with authorized...
1 min read
In computer and network security terminology, a layered defense is used to describe a security system that is build using...
1 min read
Any malicious attack that targets any computer other than the computer the attacker is currently logged on to. For example,...
1 min read
In computer and network securityterminology, a targeted attack is one that has been aimed at a specific user, company or...
1 min read
A Web document found on a company or organization’s Web site that details the type of personally identifiable informationthe company...
1 min read
Abbreviated as PII or pii, personally identifiable information is any information that can identify an individual. This type of information...
1 min read
In computer security, Discretionary Access Control (DAC) is a type of access control in which a user has complete control...
1 min read
In computer security Mandatory Access Control (MAC) is a type of access control in which only the administrator manages the...
1 min read
A malicious program that is programmed to “detonate” at a specific time and release a virus onto the computer system...
1 min read
Short for Open Source Vulnerability Database, OSVDB is an independent community-driven open source database. The project promotes greater, open collaboration...
6 mins read
WPA has been a mainstream technology for years now, but WEP remains a standard feature on virtually every wireless router...
1 min read
A type of computer virus that associates itself with the execution of programs by modifying directory table entries to ensure...
1 min read
A term loosely used to describe the growing trend of malicious software (malware) that has been designed to scan a...
1 min read
A type of antivirus program which runs in the background and actively scans your computer system constantly for viruses and...
1 min read
A type of antivirus program that actively scans your computer system for viruses only when prompted to do so by...
1 min read
A type of computer virus that will attempt to hide from an antivirus program by garbling its own code. When...
1 min read
A function of an antivirus program which attempts to remove and disinfect infections on the computer system including viruses, worms...
1 min read
Also called a Boot Sector Infector, a bimodal virus is one that infects both boot records and files on the...
1 min read
Based on the biological term retrovirus, a computer retrovirus is one that actively seeks out an antivirus program on a...
1 min read
Electronic discovery, or e-discovery, is a type of cyber forensics (also referred to as computer or digital forensics) and describes...
1 min read
Execute Disable Bit (EDB) is an Intel hardware-based security feature that can help reduce system exposure to viruses and malicious...
1 min read
A tool developed by hackers that is used to perform malicious attacks on computer systems. They are usually scripts that...
1 min read
A security model that is used to protect an entire platform and secures the entire span of software or devices...
1 min read
The process of correcting errors in data that may have been corrupted during transmission or in storage. Data transmissions are...
1 min read
In home networking, port forwarding, also called port mapping or punch-through, enables you to create a permanent translation entry that...
1 min read
Abbreviated as PAM, Port to Application Mapping is a feature of the Cisco IOS Firewall that allows you to customize...
1 min read
A type of port forwarding where outbound traffic on predetermined ports sends inbound traffic to specific incoming ports. Port triggering...
1 min read
An SSH service that provides secure and encrypted connections to traditionally non-encrypted services, such as e-mail or news. SSH port...
3 mins read
In networks, air gap is a type of security where the network is secured by keeping it separate from other...
1 min read
(1) A security device used to shut off any other device in an emergency situation in which a normal shut...
1 min read
A type of cellphone Trojan horse that infects mobile phones running Java (J2ME).
1 min read
A cellphone (also called a mobile phone) virus is the equivalent to a computer virus, only it infects consumer cellphones...
1 min read
A type of cellphone virus that became known in 2004. Mosquito was distributed as a part of a downloadable game....
1 min read
A type of cellphone virus that deactivates all links to your cellphone applications, including e-mail, IM, and calendar. It replaces...
1 min read
) Abbreviated as TN, turning number is a randomly generated security code, usually a series of digits, displayed as an...
1 min read
) Kevin David Mitnick is one of the most famous criminal hackers to be jailed and convicted. Born August 6,...
1 min read
The term used to describe the theft of laptop computers when the perpetrator literally grabs the laptop out of the owner's hand and runs away with it.
6 mins read
Almost every worldwide government agency responsible for identity theft issues will tell you the same thing: The first step to...
6 mins read
I’ve been reading a lot about undetectable malware and rootkits and the like recently. Without a doubt, these attack tools...
1 min read
A type of virus that attempts installation beneath the antivirus program by directly intercepting the interrupt handlers of the operating...
1 min read
A type of a Trojan horse that is designed to provide the attacker with sensitive data such as passwords, credit...
1 min read
A type of Trojan horse designed to destroy and delete files, and is more like a virus than any other...
1 min read
A type of Trojan horse designed to open port 21 (the port for FTP transfer) and lets the attacker connect...
1 min read
A type of Trojan horse designed to use the victim’s computer as a proxy server. This gives the attacker the...
1 min read
Abbreviated as RATs, a Remote Access Trojan is one of seven major types of Trojan horse designed to provide the...
1 min read
A type of Trojan horse designed stop or kill security programs such as an antivirus program or firewall without the...
1 min read
A virus that inserts a copy of its malicious code at the end of the file. The goal of an...
1 min read
A type of virus that has been designed to thwart attempts by analysts from examining its code by using various...
1 min read
(1) A tool that combines two or more files into a single file, usually for the purpose of hiding one...
1 min read
Now a generic term for several TCP/IP DoS attacks, but originally made infamous by the WinNuke DoS attack, which crashed...
1 min read
A security and antivirus term used to describe an approach to system security where multiple layers of security are deployed...
1 min read
In system security masquerade attack is a type of attack in which one system assumes the identity of another. See...
1 min read
The process of attempting to guess or crack passwords to gain access to a computer system or network. Crackers will...
1 min read
Short for antivirus Killer, a malicious tool used to disable a user's antivirus program to help elude detection.
1 min read
Character sequences that reprogram specific keys on the keyboard. If ANSI.SYS is loaded, some bombs will display colorful messages, or...
1 min read
A type of malware that uses common, dynamic scripting languages (e.g. Java, Javascript, Active X, or Visual Basic). Vulnerabilities in...
1 min read
Malicious code is the term used to describe any code in any part of a software system or script that...
1 min read
A zero-day exploit or vulnerability is a security flaw in a computer system or program that allows hackers to perform...
1 min read
Commonly used in IPS (intrusion prevention system), a countermeasure is a defensive technology method used to prevent an exploit from...
11 mins read
In this Webopedia article we look at the “Internet junk mail” terminology and discuss best practices for protecting your system...
5 mins read
SIEM – security information and event management Security Incident and Event Manager (SIEM) is a set of network security tools,...
1 min read
A hardware device with several asynchronous connectors and an X.25 attachment. This commercially available device can be connected to a...
1 min read
Short for Open Secure Shell, OpenSSH is a free suite of tools (similar to the SSH connectivity tools) that help...
1 min read
A honeymonkey is a computer or a virtual PC that actively mimics the actions of a user surfing the Web....
1 min read
A program that is often used to maliciously redirect Internet connections. When used in a malicious way, it disconnects the...
1 min read
Unified Threat Management (UTM) is a term first used by IDC to describe a category of security appliances which integrates...
1 min read
Acronym for Open Vulnerability and Assessment Language. OVAL is an XML-based language that provides a standard for how to check...
1 min read
Symantec provides products and services to help individuals and enterprises assure the security, availability, and integrity of their information. Headquartered...
1 min read
BRS or Big Red Switch is a phrase used to describe an immediate shut down of a system using the...
1 min read
Snort is an open source network intrusion prevention system (IPS) capable of performing real-time traffic analysis and packet-logging on IP...
1 min read
WebSEAL is a high-performance, multi-threaded Web server that applies fine-grained security policy to the Tivoli Access Manager protected Web object...
1 min read
A security policy is a document that outlines the rules, laws and practices for computer network access. This document regulates...
1 min read
Virus Application Programming Interface, or Virus API (VAPI) is also referred to as Antivirus API (AVAPI), or Virus Scanning API...
1 min read
SIM is short for security information management. It is a type of software that automates the collection of event log...
1 min read
Short for automatic identification, Auto ID is the term used to describe the process of automatic data collection and identification...
1 min read
Short for Spam URI Real-time Block Lists, it is used to detect spam based on message body URIs (usually Web...
1 min read
Short for longitudinal redundancy check, it is an error detection and checking method used to verify the accuracy of stored...
1 min read
Short for vertical redundancy check it is a method of error checking that attaches a parity bit to each byte...
1 min read
A sender transmits a volume of connections that cannot be completed. This causes the connection queues to fill up, thereby...
1 min read
A DoS attack where fragmented packets are forged to overlap each other when the receiving host tries to reassemble them....
1 min read
Short for Remote Access Trojan, a Trojan horse that provides the intruder, or hacker, with a backdoor into the infected...
1 min read
Programs that network users download and install on their computers usually without permission from or knowledge of the IT department....
3 mins read
Often used by organizations to ease remote management and to cut costs, a network server appliance is a typically inexpensive...
4 mins read
Often used by organizations to ease remote management and to cut costs, a network server appliance is a typically inexpensive...
1 min read
A rootkit is a type of malicious software that is activated each time your system boots up. Rootkits are difficult...
1 min read
Netbus, also called Netbus Trojan, is a Win32-based Trojan program. Authored by Carl-Frederik Neikter, it first appeared in March 1998...
1 min read
Greyware refers to a malicious software or code that is considered to fall in the “grey area” between normal software...
1 min read
Blended threats combine the characteristics of viruses, worms, Trojan Horses, and malicious code with server and Internet vulnerabilities to initiate,...
1 min read
Anti-adware refers to any software utility that scans your system and removes adware, spyware, keyloggers, trojans, and other malicious code...
1 min read
NAPT, or Network Address Port Translation, is a method by which many network addresses and their TCP/UDP (Transmission Control Protocol/User...
1 min read
Short for host-based intrusion prevention system, HIPS is an IPS or intrusion prevention systemdesigned for security over host-based systems where...
1 min read
An IPS, or intrusion prevention system is used in computer security. It provides policies and rules for network traffic along...
1 min read
L0phtCrack is a password auditing and recovery application. It uses multiple assessment methods to assist administrators in reducing security risks....
1 min read
Short for network-based intrusion prevention system, NIPS is an IPS or intrusion prevention systems designed for security over network-based systems....
1 min read
Similar in nature to email phishing, pharming seeks to obtain personal or private (usually financial related) information through domain spoofing....
1 min read
Shoulder surfing refers to a direct observation, such as looking over a person’s shoulder, to obtain information. In some cases...
1 min read
Common Vulnerabilities and Exposures (CVE) is a dictionary-type list of standardized names for vulnerabilities and other information related to security...
1 min read
Acronym for potentially unwanted program PUP or PUPs is a term used to describe unwanted programs such as Trojans, spyware...
5 mins read
The Internet Key Exchange (IKE) protocol is a key management protocol standard that is used in conjunction with the IPSec...
4 mins read
Seeing a need for some laws regarding the collection of information from children online, the FTC enacted rules to ensure...
1 min read
Cyber crime encompasses any criminal act dealing with computers and networks (called hacking). Additionally, cyber crime also includes traditional crimes...
1 min read
computer forensics, is the application of scientifically proven methods to gather, process, interpret, and to use digital evidence to provide...
2 mins read
A keylogger (keystroke logger) is a type of surveillance software used to record the keystrokes made on a device. This...
1 min read
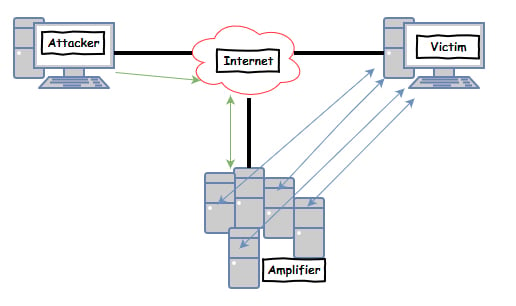
Flooding is a Denial of Service (DoS) attack that is designed to bring a network or service down by flooding...
1 min read
A proof of concept virus is written by an individual with advanced programming skills, usually to ‘show off’ their programming...
6 mins read
Not technically fitting into either the virus or spam category we have spyware and adware, which are growing concerns for...
4 mins read
Social engineering is the term used to describe many methods of stealing personal information and manipulating people to hack their...
1 min read
(n.) Also referred to as ARP poison routing (APR) or ARP cache poisoning, a method of attacking an Ethernet LAN...
1 min read
(f r w k-ing) (n.) Developed by Mike Schiffman and David Goldsmith, a technique for testing the vulnerability of a...
1 min read
(split tun &l-ing) (n.) The process of allowing a remote VPN user to access a public network, most commonly the...
1 min read
(pas iv ri-kon &-zents) (n.) The process of collecting information about an intended target of a malicious hack without the...
1 min read
(ham ing k d) (n.) In digital data transmissions, a method of error detection and correction in which every string...
1 min read
(n.) A type of antivirus program that searches a system for virus signatures that have attached to executable programs and...
1 min read
(n.) Adware is software that contains advertisements embedded in the application. Adware is considered a legitimate alternative offered to consumers...
1 min read
(n.) An object that is verified when presented to the verifier in an authentication transaction. Credentials may be bound in...
1 min read
(n.) Also referred to as TCP session hijacking, a security attack on a user session over a protected network. The...
1 min read
( kw&l er &r r t) (n.) Equal error rate is abbreviated as EER. Equal error rate (EER) is a...
1 min read
(f ls ak-sep t&ns) (n.) In biometrics, the instance of a security system incorrectly verifying or identifying an unauthorized person....
1 min read
(mul t -p r t t v rus) (n.) Also called a multi-part virus, a virus that attempts to attack...
I hate spam. You hate spam. We all hate spam. Webopedia offers this collection of articles and Web resources to...
3 mins read
A strong password describes a password that is difficult to detect by both humans and computer programs, effectively protecting data...
3 mins read
The first time it happened, you were probably confused and even a bit curious, especially if you were not aware...
1 min read
Cross-site scripting (XSS) is a security breach that takes advantage of dynamically generated Web pages. In an XSS attack, a...
1 min read
A form of attack on a database-driven Web site in which the attacker executes unauthorized SQL commands by taking advantage...
1 min read
A polymorphic virus is a virus that changes its virus signature (i.e., its binary pattern) every time it replicates and...
1 min read
A computer virus that actively hides itself from antivirus software by either masking the size of the file that it...
1 min read
Also called a dropper program or a virus dropper, a program that when run will install a virus, Trojan horse...
1 min read
A collection of networks, computers, and databases under a common administration, such as an enterprise’s intranet. The devices that operate...
1 min read
Short for Electronic Book Exchange, a DRM standard for protecting copyright in electronic books and for distributing electronic books among...
1 min read
Often referred to as simply a subright, in book publishing, a right to use content that is subsidiary to the primary right; for example, film rights or foreign-language translation rights to a book are subsidiary rights.
1 min read
The right to move, copy, or loan content.
1 min read
Short for International Standard Works Code, an internationally recognized reference number for the identification of musical works. The code that...
1 min read
An identity that is recognized throughout a network, such as the Internet or an enterprise s LAN. This concept is...
1 min read
In computer technology, the unique name of a person, device, or the combination of both that is recognized by a...
1 min read
Abbreviated as ICE, a computer chip that is used to emulate a microprocessor so that embedded system software can be...
A PC that is connected to the Internet via a cable modem is always vulnerable to a malicious hack attack...
1 min read
Formed by combining “hack” with “activism,” hacktivism is the act of hacking into a Web site or computer system in...
Since World War II scientists have known that EMR leaked from devices can be intercepted and with the proper equipment,...
1 min read
Also called slag code, programming code added to the software of an application or operating system that lies dormant until...
1 min read
A virus that stays in memory after it executes and after its host program is terminated. In contrast, non-memory-resident viruses...
2 mins read
Short for Constructive Cost Model, a method for evaluating and/or estimating the cost of softwaredevelopment. There are three levels in...
1 min read
Short for Open Web Application Security Project, an open source community project set up to develop software tools and knowledge-based...
Short for high-bandwidth digital-content protection, a specification developed by Intel for protecting digital entertainment content that uses the DVI interface....
1 min read
The automated process of proactively identifying security vulnerabilities of computing systems in a network in order to determine if and...
1 min read
Short for Realm-Specific Internet Protocol, an IP address translation technique that is an alternative to NAT. RSIP lets an enterprise...
1 min read
A software program that is designed to appear to be a real functioning network but is actually a decoy built...
1 min read
Short for port address translation, a type of network address translation. During PAT, each computer on LAN is translated to...
1 min read
Short for Role-Based Access Control, a system of controlling which users have access to resources based on the role of...
2 mins read
(Pronounced “sam-el”) SAML, short for Security Assertion Markup Language,) is an open standard that uses Extensible Markup Language (XML) to...
1 min read
Short for forward error correction, a method of communicating data that corrects errors in transmission on the receiving end. Prior...
1 min read
A form of DoS attack known as a degradation-of-service attack, as opposed to a denial-of-service attack. Unlike a regular zombie...
1 min read
A unique string of bits, or the binary pattern, of a virus. The virus signature is like a fingerprint in...
1 min read
An anti-piracy technology built into all Microsoft Office XP, Windows XP and Visio 2002 products. Product Activation requires that the...
1 min read
Stateful inspection, also referred to as dynamic packet filtering, is a firewall architecture that works at the network layer. Contrast...
1 min read
A software program from RealNetworks that allows the streaming of audio, video and rich media files.
1 min read
Backdoor is an undocumented way of gaining access to a program, online service or an entire computer system. A backdoor...
1 min read
AIP is short for application infrastructure provider. AIP is a hosting provider that offers a full set of infrastructure services...
5 mins read
A managed services provider, or MSP, is a firm that follows a business model in which it manages one or...
2 mins read
An intrusion detection system (IDS) inspects all inbound and outbound network activity and identifies suspicious patterns that may indicate a...
1 min read
To move an infected file, such as a virus, into an area where it cannot cause more harm. Antivirus softwares...
1 min read
Short for the Computer Emergency Response Team Coordination Center. CERT was started in December 1988 by the Defense Advanced Research...
2 mins read
Honeypot is an Internet-attached server that acts as a decoy, luring in potential hackers in order to study their activities...
1 min read
A person, normally someone who is not technologically sophisticated, who randomly seeks out a specific weakness over the Internet in...
1 min read
Kernel32.dll is the 32-bit dynamic link library found in the Windows operating system kernel. It handles memory management, input/output operations,...
1 min read
A bastion host is a gateway between an inside network and an outside network. Used as a security measure, the...
4 mins read
Steganography is the practice of hiding or concealing a message within a message that is not secret, such as hiding...
1 min read
Short for Open Profiling Standard, similar to P3P, but not worked on by the W3C. Instead, it has been adopted...
1 min read
Platform for Privacy Preferences is a specification that will allow users’ Web browsersto automatically understand Web sites’ privacy practices. Privacy...
1 min read
Also referred to as static packet filtering. Controlling access to a network by analyzing the incoming and outgoing packets and...
1 min read
Refers to the validity of data. Data integrity can be compromised in a number of ways: Human errors when data...
1 min read
A type of computer virus that is encoded as a macro embedded in a document. Many applications, such as Microsoft...
2 mins read
Network Address Translation (NAT) is an Internet standard that enables a local-area network (LAN) to use one set of IP...
1 min read
In computing, the phrase crack is used to mean the act of breaking into a computer system. The term was...
1 min read
Smurf attack is a type of network security breach in which a network connected to the Internet is swamped with...
1 min read
A formal description of a software system that is used as a blueprint for implementing the program. At minimum, a...
1 min read
A protocol for handling TCP traffic through a proxy server. It can be used with virtually any TCP application, including...
1 min read
Refers to mechanisms and policies that restrict access to computer resources. Also see ACL.
4 mins read
What’s a Trojan horse virus? A trojan horse virus, or trojan, is a form of malware. It disguises itself as...
1 min read
(1) Contention means competition for resources. The term is used especially in networks to describe the situation where two or...
1 min read
(n.) A widely used standard for defining digital certificates. X.509 (Version 1) was first issued in 1988 as a part...
1 min read
Closely related to hacking, using a computer or other device to trick a phone system. Typically, phreaking is used to...
1 min read
A type of security that uses two layers of encryption to protect a message. First, the message itself is encoded...
11 mins read
Symmetric encryption is a crucial technology responsible for the online security of sensitive data like credit card details. Symmetric key...
7 mins read
Hashing is a one-way process that converts data into a fixed-length string, ensuring security and data integrity in cybersecurity, database...
1 min read
Short for public key infrastructure, a system of digital certificates, Certificate Authorities, and other registration authorities that verify and authenticate...
1 min read
Short for Challenge Handshake Authentication Protocol, a type of authentication in which the authentication agent (typically a network server) sends...
1 min read
A dongle is a device that attaches to a computer to control access to a particular application. Dongles provide the...
1 min read
A digital code that can be attached to an electronically transmitted message that uniquely identifies the sender. Like a written...
1 min read
In linguistics, to divide language into small components that can be analyzed. For example, parsing this sentence would involve dividing...
1 min read
An extension to the HTTP protocol to support sending data securely over the World Wide Web. Not all Web browsers...
10 mins read
Authentication refers to the process of identifying an individual, usually based on a username, password, and some type of additional...
1 min read
The process of granting or denying access to a network resource. Most computer security systems are based on a two-step...
9 mins read
A firewall is a division between a private network and an outer network, often the internet, that manages traffic passing...
1 min read
Same as password, a series of characters and numbers that enables a user to access a computer.
2 mins read
1. In IT security, access refers to the permissions a user, program, or device has to interact with data, content,...
1 min read
A utility that searches a hard disk for viruses and removes any that are found. Most antivirus programs include an...
1 min read
A simple error-detection scheme in which each transmitted message is accompanied by a numerical value based on the number of...
1 min read
A computer, software product, or device that functions exactly like another, better-known product. In practice, the term refers to any...
2 mins read
(n) Indicates that a product can work with or is equivalent to another, better-known product. The term is often used...
1 min read
A special, non-printing character that begins, modifies, or ends a function, event, operation or control operation. The ASCII character set...
1 min read
Short for cyclic redundancy check, a common technique for detecting data transmission errors. Transmitted messages are divided into predetermined lengths...
1 min read
Not working. A computer system is said to be down when it is not available to users. This can occur...
1 min read
In communications, error detection refers to a class of techniques for detecting garbled messages. Two of the simplest and most...
1 min read
Refers to the parity-checking mode in which each set of transmitted bits must have an even number of set bits....
8 mins read
Hacking is the practice of entering a computing system and exploring its weaknesses, including both hardware and software. This exploration...
1 min read
A terminal (monitor and keyboard) that contains processing power. Intelligent terminals include memory and a processor to perform special display...
1 min read
Pronounced klooj.Kludge is a derogatory term that refers to a poor design. Like hacks, kludges use nonstandard techniques. But, whereas...
1 min read
(v.) To make a computer system or network recognize you so that you can begin a computer session. Most personal...
1 min read
The property of nickel-cadmium (NiCad) batteries that causes them to lose their capacity for full recharging if they are discharged...
1 min read
The mode of parity checking in which each 9-bit combination of a data byte plus a parity bit contains an...
2 mins read
Parity checking uses parity bits to check that data has been transmitted accurately. The parity bit is added to every...
1 min read
The quality of being either odd or even. The fact that all numbers have a parity is commonly used in...
1 min read
A password is secret series of characters that enables a user to access a file, computer, or program. On multi-user...
4 mins read
PC stands for personal computer. PCs are multipurpose computers suited for individual end users, as opposed to high-performance computers that...
1 min read
Characteristic of an object. In many programming languages, including Visual Basic, the term property is used to describe attributes associated...
12 mins read
Cyber security is the practice of protecting computer systems, networks, and data by using a variety of different strategies and...
2 mins read
What is a Username? A username is a unique identifier used to gain access to a computer, network, or online...