Beat the Exploit Clock: From CVE Chaos to Proactive Remediation
Expose the Risk. Stop the Breach. Automate the Fix.
Introducing Attack surface management++
28.3% of new CVEs were
exploited within 24 hours
Traditional scanners leave
you drowning in alerts
graph tools cannot fix the
problems they find
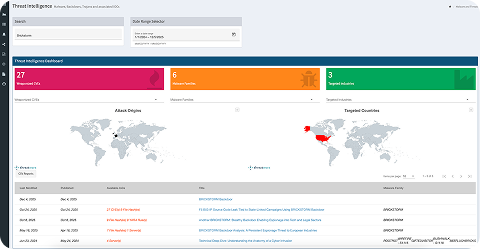
We combine Rocketgraph's massive-scale graph analytics with Threatworx's proactive, AI-powered discovery and remediation. The result? A vulnerability management solution that doesn't just list problems—it prioritizes them by business impact and fixes them before attackers can strike.
Explore our use cases
The “Kill Chain” Breaker
The CISO Pain
We are drowning in "Critical" alerts (CVSS 9.0+). We cannot patch them all. We need to know which one vulnerability allows an attacker to pivot from a low-value test server to our "Crown Jewel" production database.
The Solution
- Rocketgraph ingests our entire asset map (network, identity, cloud) into its xGT in-memory engine, which can traverse billions of relationships.
- Threatworx provides the high-fidelity vulnerability data.
- The Win: We ask Mission Control: "Show me all internet-facing assets with active exploits that have a direct path to the Payments Database."
Rocketgraph visualizes the path, “the blast radius”; Threatworx provides the patch. - The Difference: Scale & Speed. Other graph-based tools choke when loading the full enterprise dataset (logs, assets, and netflow). Rocketgraph's xGT engine handles this in memory, delivering answers in seconds, not hours.
ROI / Savings
- Calculated ROI: $1.2M annually in Operational Efficiency.
- The Math: An average Level 2 analyst spends 4 hours researching asset context per critical alert. With 50 criticals/week, that's 10,000 hours/year. The Integrated Rocketgraph and Threatworx Solution can reduce research time to <5 minutes per alert, a 98% reduction in research time.
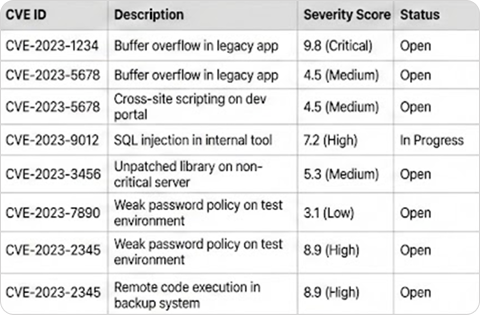
Before: Flat list of CVEs
(confusing scores)
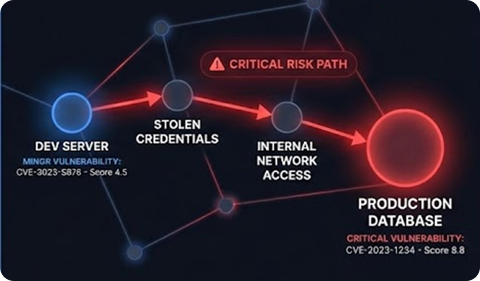
After: Rocketgraph kill
chain visualization
Zero-Day ”Flash Search”
The CISO Pain
When the next Log4j hits, the Board asks: "Are we exposed?" Our current answer is: "We are scanning, give us 48 hours." That is unacceptable.
The Solution
- Threatworx maintains a "Code-to-Cloud" inventory, including deep software dependencies (SBOMs).
- Rocketgraph indexes this entire web of dependencies.
- The Win: Type into Rocketgraph: "Where is log4j-core < 2.14.1 running right now?" Result: Instant global visibility across containers, code repos, and servers.
- The Difference: Unified Data Model. It connects the code (Threatworx finding) to the deployed Asset (Rocketgraph map). We see the risk before it's even compiled into production.
ROI / Savings
- Calculated ROI: $450k per Major Incident.
- The Math: During Log4j, we spent ~3,000 engineer hours on manual discovery and patching. Automated discovery cuts this by 90%.

No more Zero-day panic...
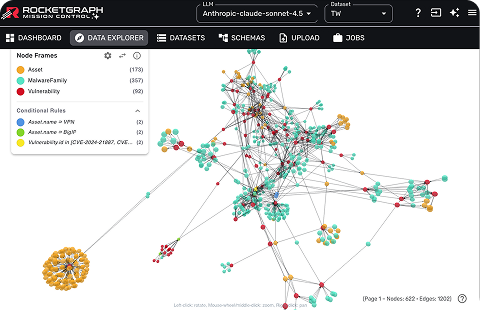
Global visibility within
seconds, not days
Automated Remediation of “Toxic Combinations”
The CISO Pain
Finding the threat is easy. Fixing it is hard. We have a 60-day backlog because Ops teams ignore security tickets that lack clear fix instructions.
The Solution
- Rocketgraph identifies a "Toxic Combination" (e.g., Asset A has a vuln + Asset A has admin privileges + Asset A is internet exposed).
- Threatworx automatically generates AI-validated remediation code or script.
- The Win: Security sends Ops a solution, not a problem. "Here is the script to update the library and close the port."
- The Difference: Native Remediation. Threatworx doesn't just trigger a ticket; it offers the actual code-fix/patch/remediation for any threat reported on your attack surface.
ROI / Savings
- Calculated ROI: 30% reduction in Mean Time to Remediate (MTTR).
- The Math: Reducing the exposure window from 45 days to 30 days significantly lowers the breach probability curve. Hard savings come from retiring standalone patching tools (~$150k/year).
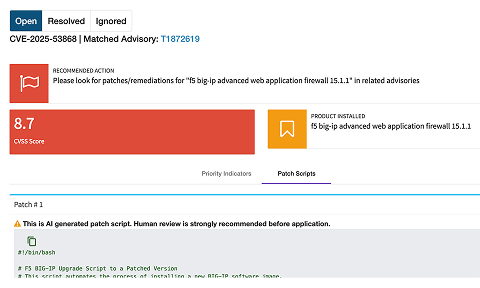
One-click fix for
“Ticket Toss” gridlock
False Positive Elimination (The “Attenu8” Filter)
The CISO Pain
Our scanners report 10,000 vulnerabilities. Threat intel says only 100 are actually being exploited. We waste massive resources chasing ghosts.
The Solution
- Threatworx Attenu8: Uses AI to curate threat intel from the dark web, flagging only active threats.
- Rocketgraph: Adds environmental context (e.g., "This asset is air-gapped").
- The Win: We auto-close 90% of "High" severity tickets that have no active exploit and no path to the internet.
- The Difference: Contextual Suppression. Standalone Intel tells you "CVE-2025-123 is bad." The Integrated Rocketgraph and ThreatworxSolution tells you "CVE-2025-123 is bad, BUT you are safe because of your firewall config."
ROI / Savings
- Calculated ROI: $500k in reclaimed Engineering Productivity.
- The Math: Developers spend 20% of their time dealing with security alerts. If 50% of those are false positives, we are wasting 10% of total engineering capacity. Reclaiming that creates massive value.
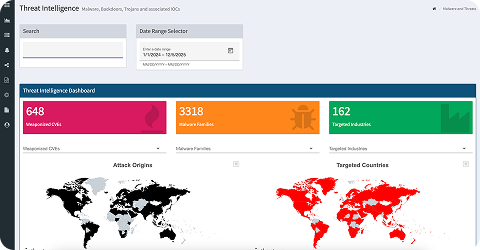
Analysts no longer drown in
endless “alert fatigue” …