We Reveal The TruthHiding In Plain SightWe RevealThe Truth HidingIn Plain Sight
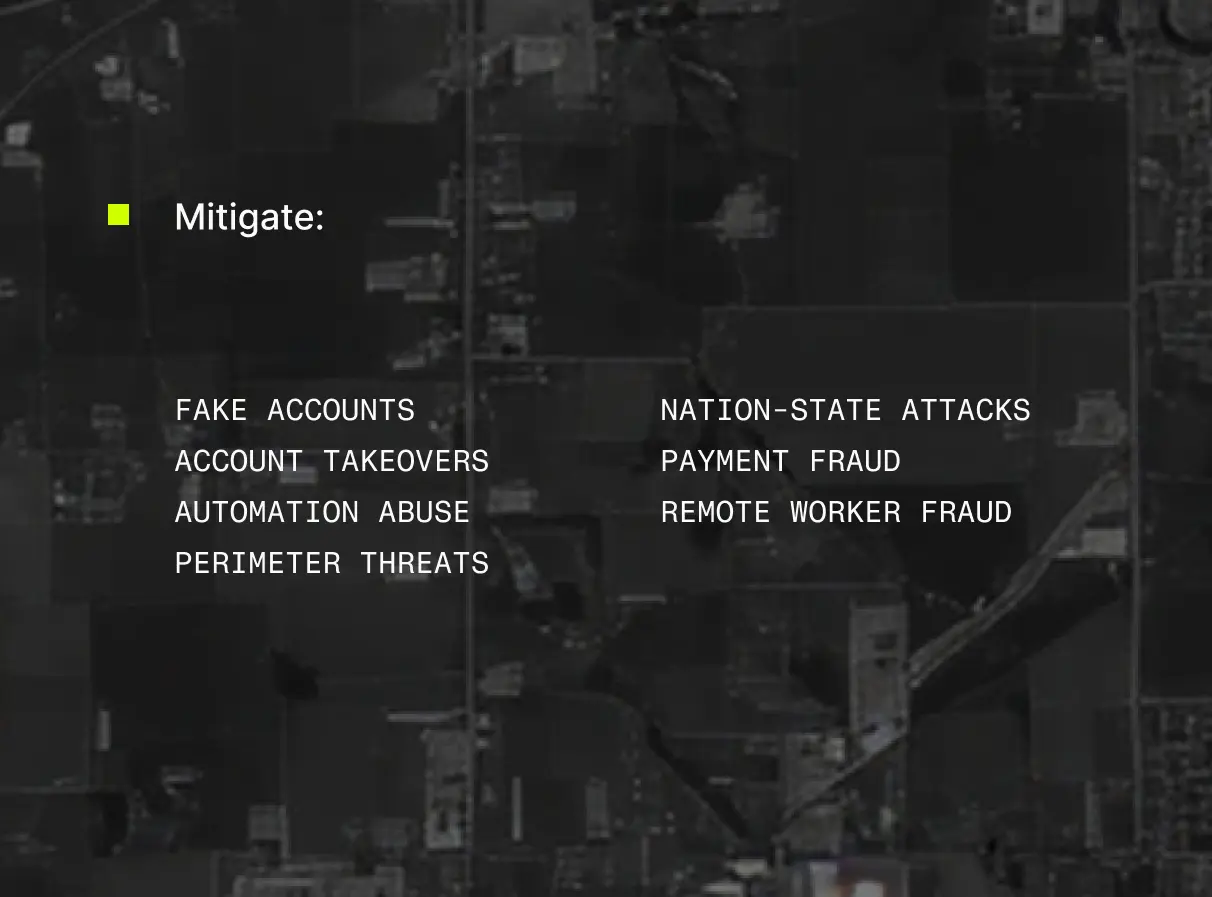
Our high-fidelity IP intelligence mitigates fake account creation, account takeovers, automation abuse, payment fraud, and other online threats.
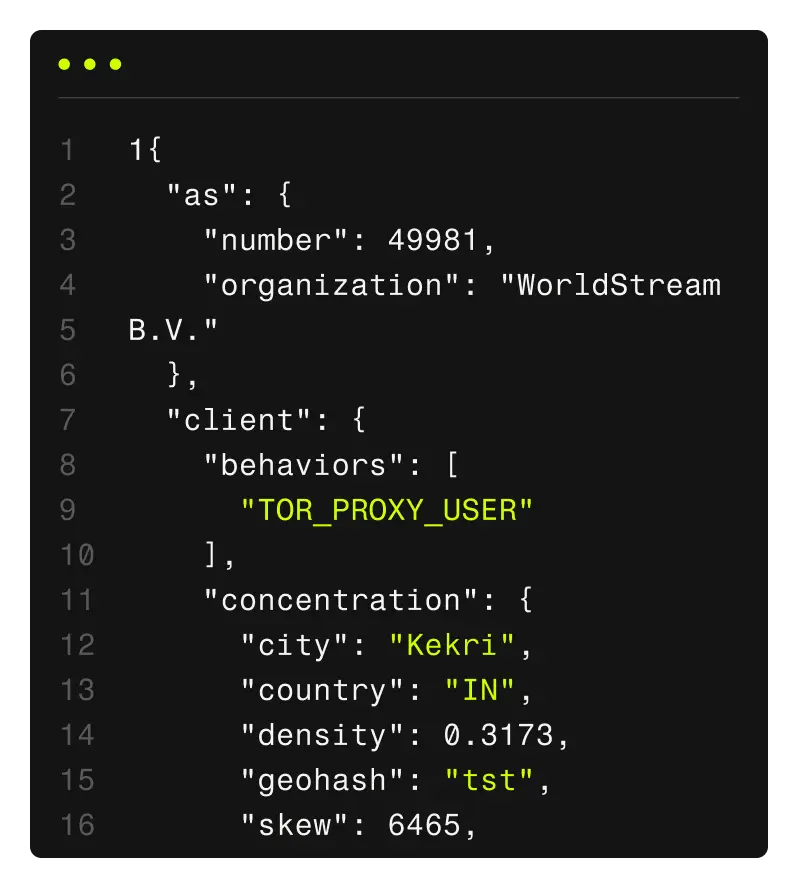
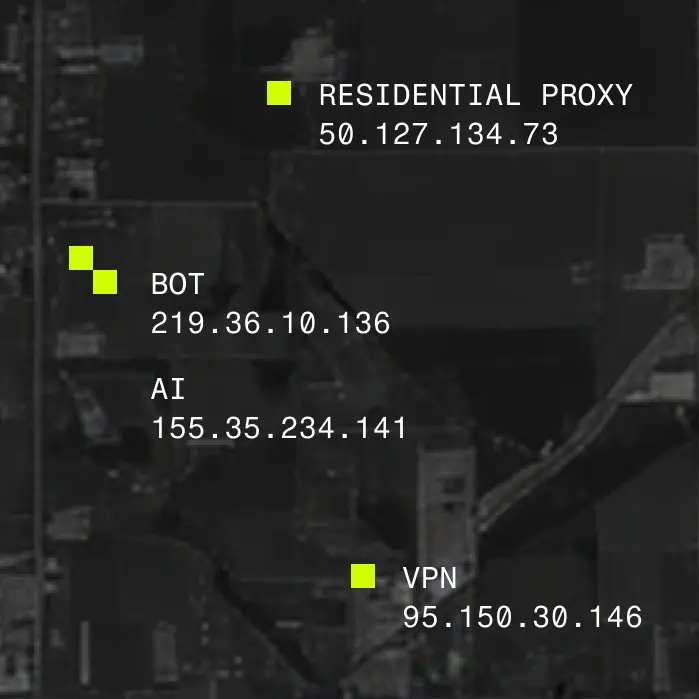
Every day, attackers mask their activity behind residential proxies, VPNs, and bot networks to commit fraud, scrape data, and evade detection. Spur cuts through that noise by enriching every IP address with deep, verified intelligence that transforms obfuscation into evidence.
Built by security researchers and engineers, Spur delivers accurate IP intelligence that is trusted by teams who can’t afford to guess. From fraud prevention to threat attribution, Spur helps organizations detect what others miss and act with confidence.

Value Proposition

Why Spur Exists. Your Security Stack Is Strong — But Blind.
Modern security stacks are built from powerful tools, each watching for a different threat. But between these tools are blind spots. Threat actors exploit those gaps to impersonate real users, hide behind residential IPs, and bypass your defenses long before your tools notice.
Spur makes those blind spots visible. By validating every IP with real-world behavioral and network attributes, Spur uncovers the truth your stack can’t see.
- 01

CDNs/WAFs
Weak on residential proxy attribution & AI-driven bot detection. Traffic can easily look like a “real user” from a residential IP. Rules are either too permissive or risk blocking legitimate users.
Evaluates the individual session and detailed IP attributes, enabling you to intelligently increase user friction or deny risky sessions for smarter edge enforcement.
[See how we compare]CDNs/WAFs
- 02
Fraud & Bot Management
Lack of session-level anonymization detection and attribution. May harm conversion or interfere with desirable agentic automation.
Most granular detail into specific residential/ malware proxy networks links tradecraft across campaigns and allows for targeted user friction or alerts.
[See how we compare]Fraud & Bot Management
- 03
Fingerprinting
High rates of false positives for VPN and residential proxy detection. Less accurate for security and fraud use-cases. Privacy concerns and considerations.
Highest-level accuracy in session-level VPN and residential proxy detection vs. traditional browser and device attribute tracking with security features tacked on.
[See how we compare]Fingerprinting
- 04

Geolocation
Providers often rely on incorrect or self-reported data. VPNs and proxies are used to hide the end-user location creating a mismatch between stated and actual location.
Accurate geolocation with geo-mismatch detection beats self-reported data with no VPN/proxy context.
[See how we compare]Geolocation
- 05
Cyber Threat Intel
Focused on inside-out connections; not outside-in. Misses the “clean” last-mile IPs used for inbound attacks.
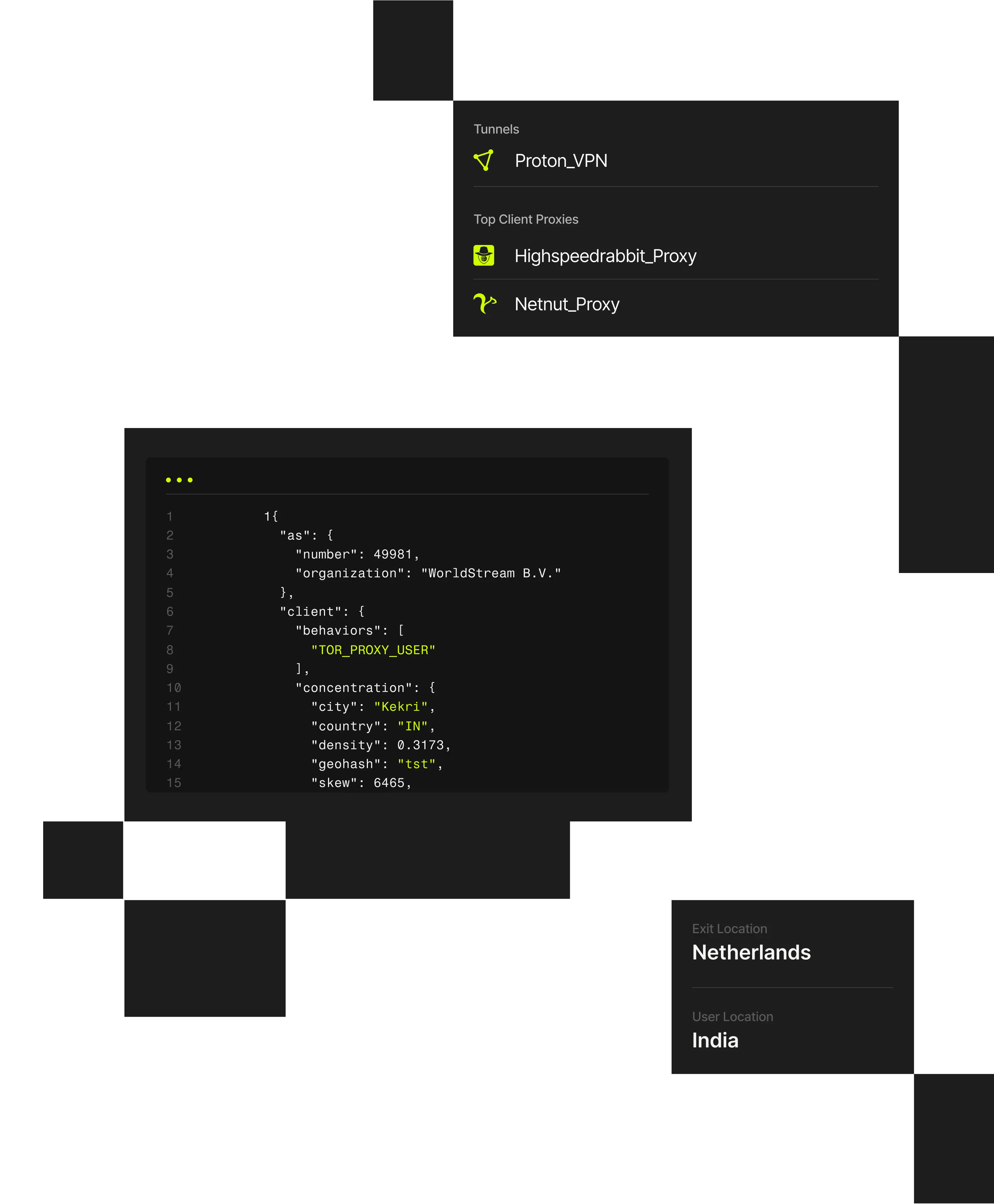
Accurate identification of VPN/proxy service that an IP/session is using, plus tunnel entry/exit context, device/ connection type, usage concentrations, and client behaviors.
[See how we compare]Cyber Threat Intel
How it Works. How Spur Turns Hidden Signals Into Trusted Intelligence.
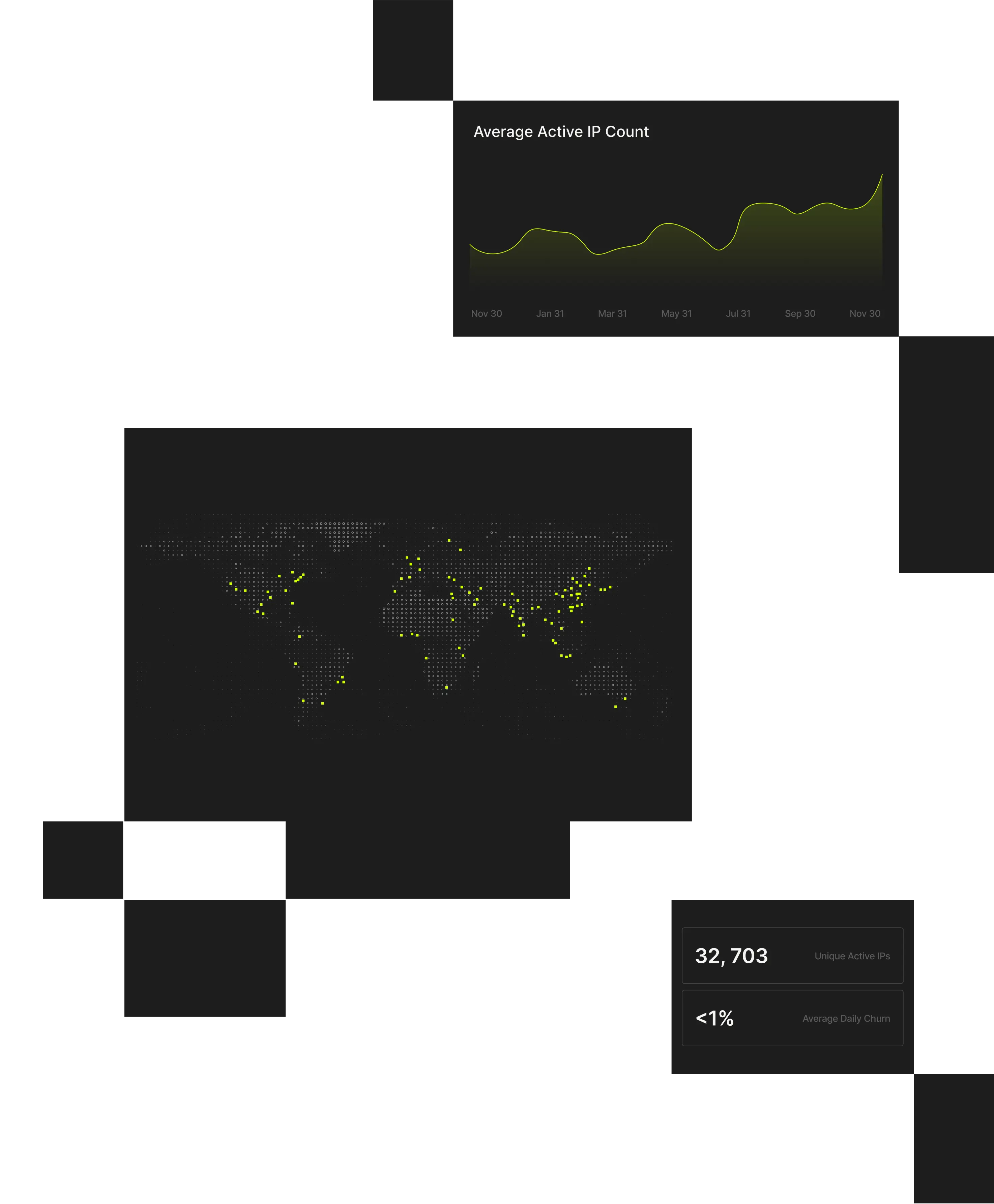
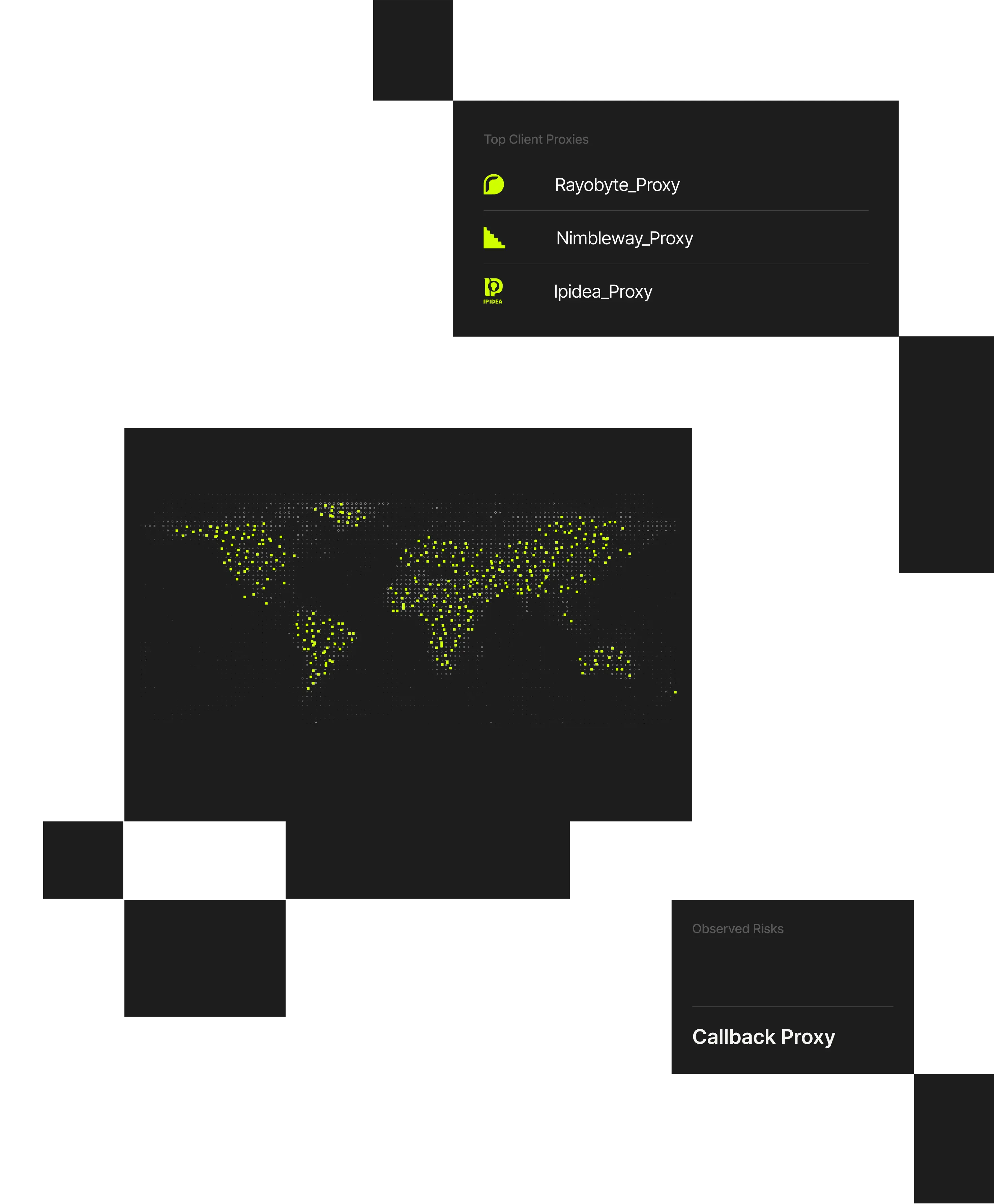
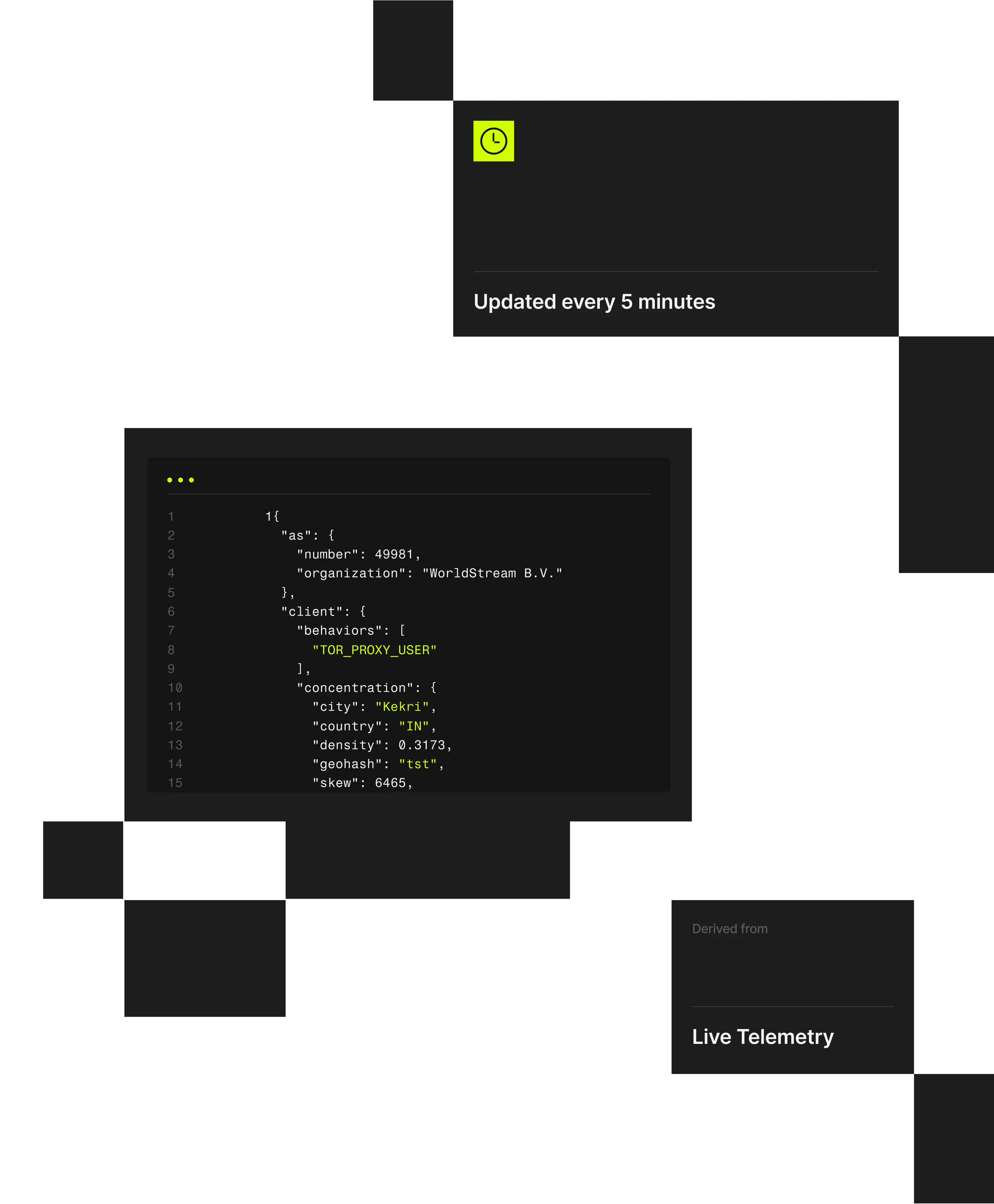
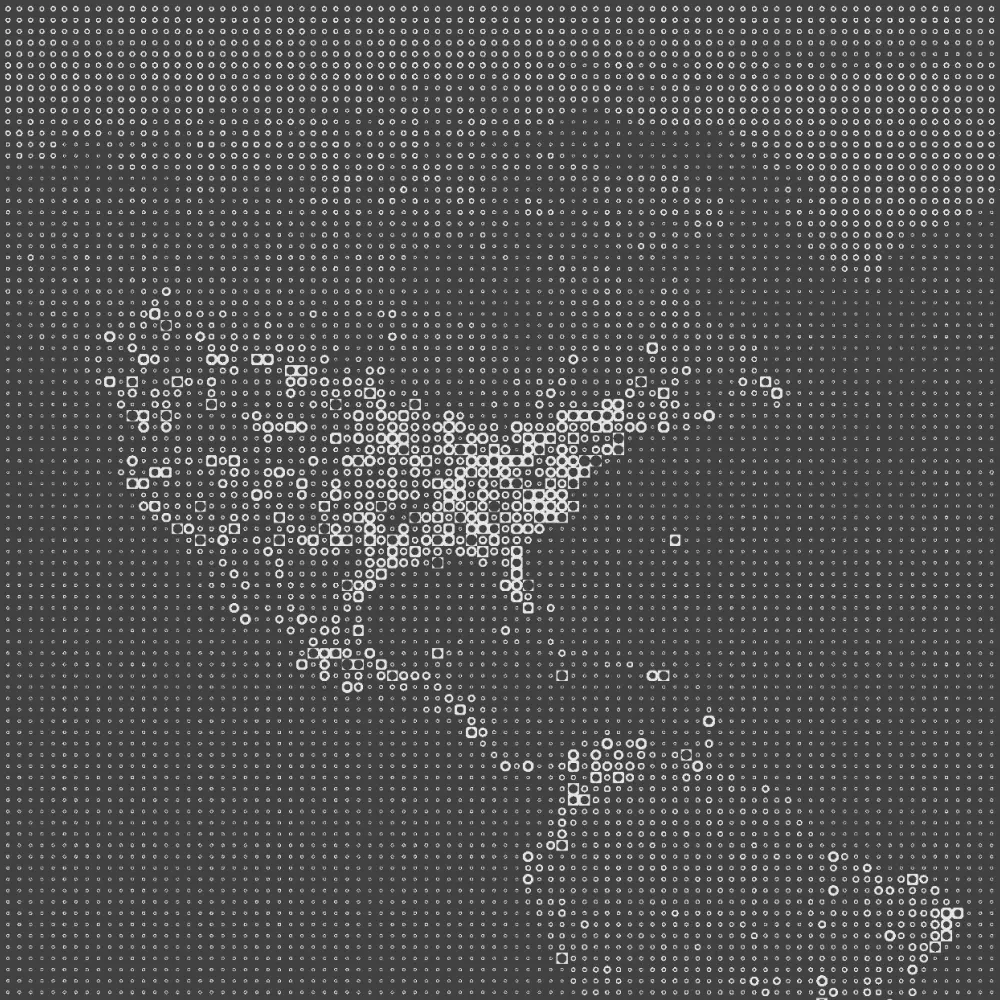
Spur continuously observes the full churn of anonymization infrastructure, detecting 230M+ unique anonymized IPs every 90 days and distilling that into ~60M suspect IPs daily. With coverage spanning 1,000+ VPN and proxy services, Spur exposes the real scope of rotating, ephemeral infrastructure that other vendors miss.
Observe
Continuous observation of global anonymization infrastructure.

Enrich
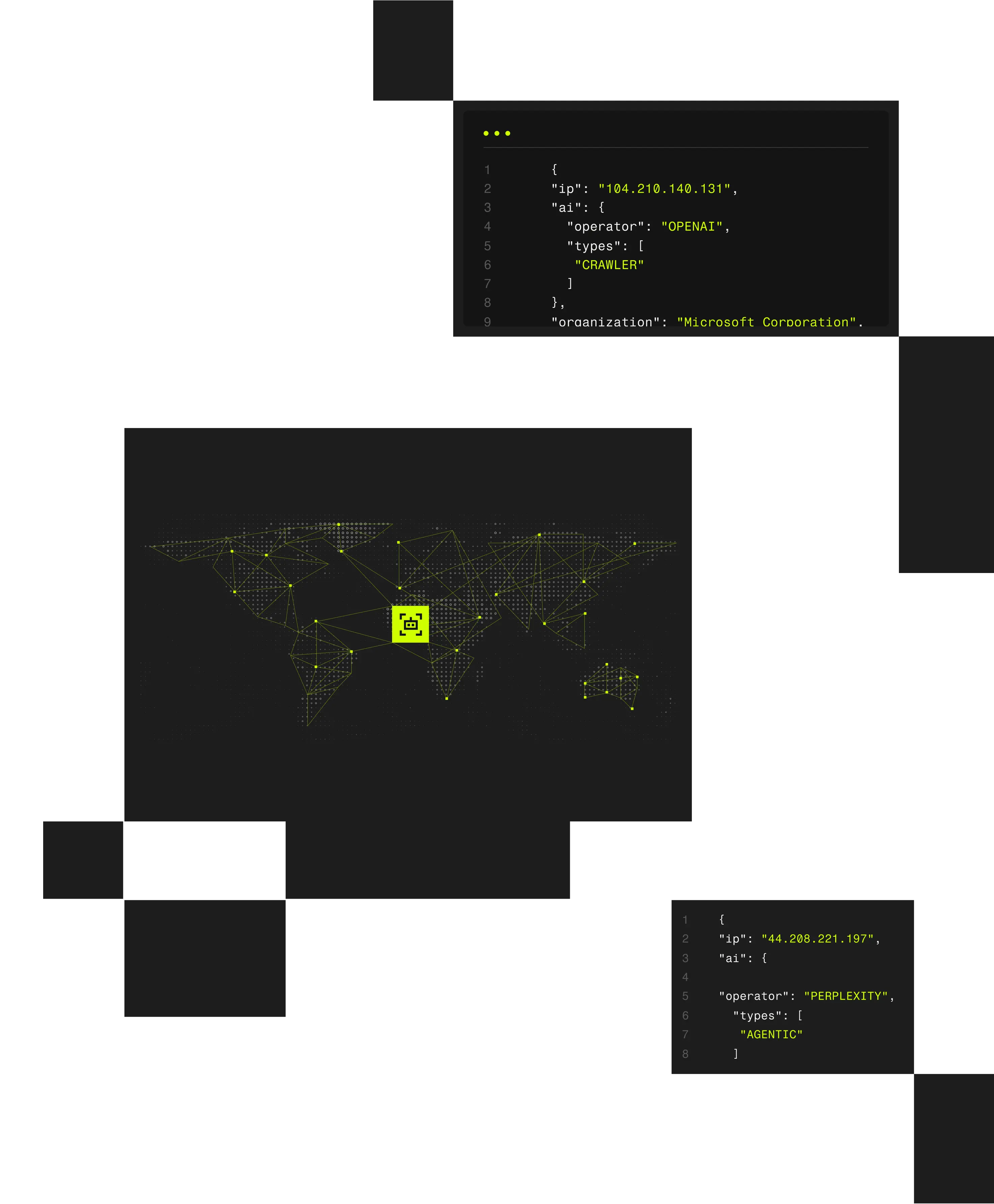
Classify every IP using 20+ verified attributes across network, behavior, geography.
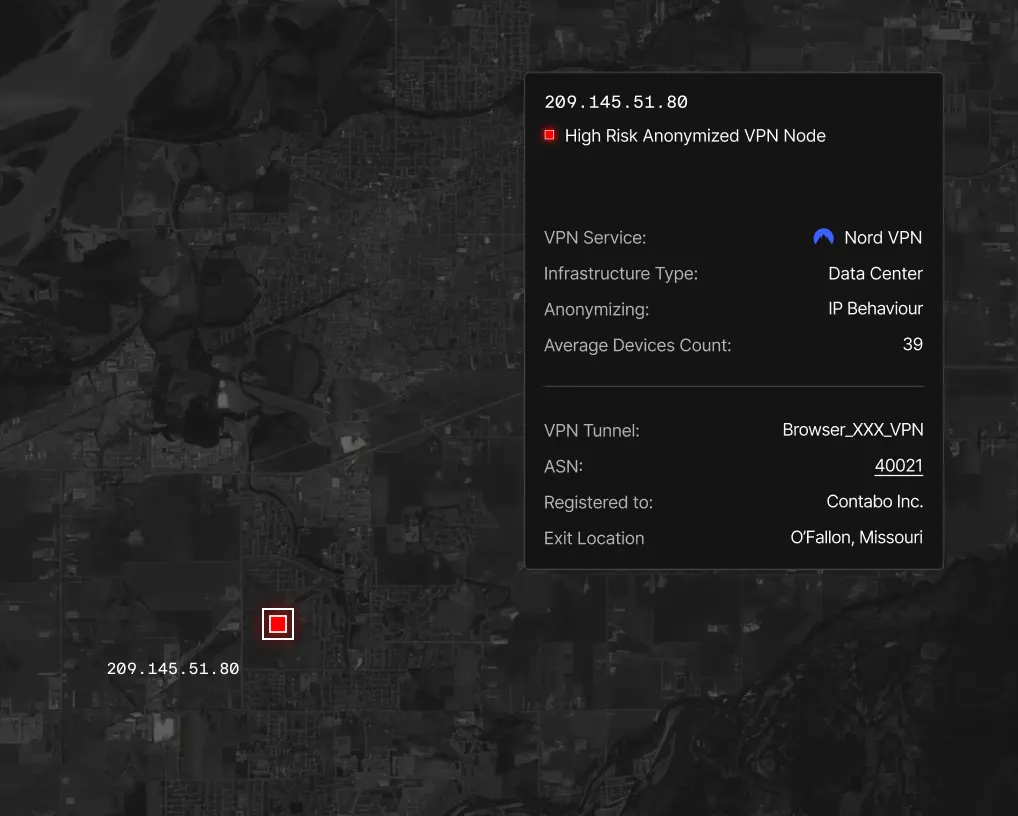
Act
Integrate findings into your enrichment pipelines to act on risky IPs.
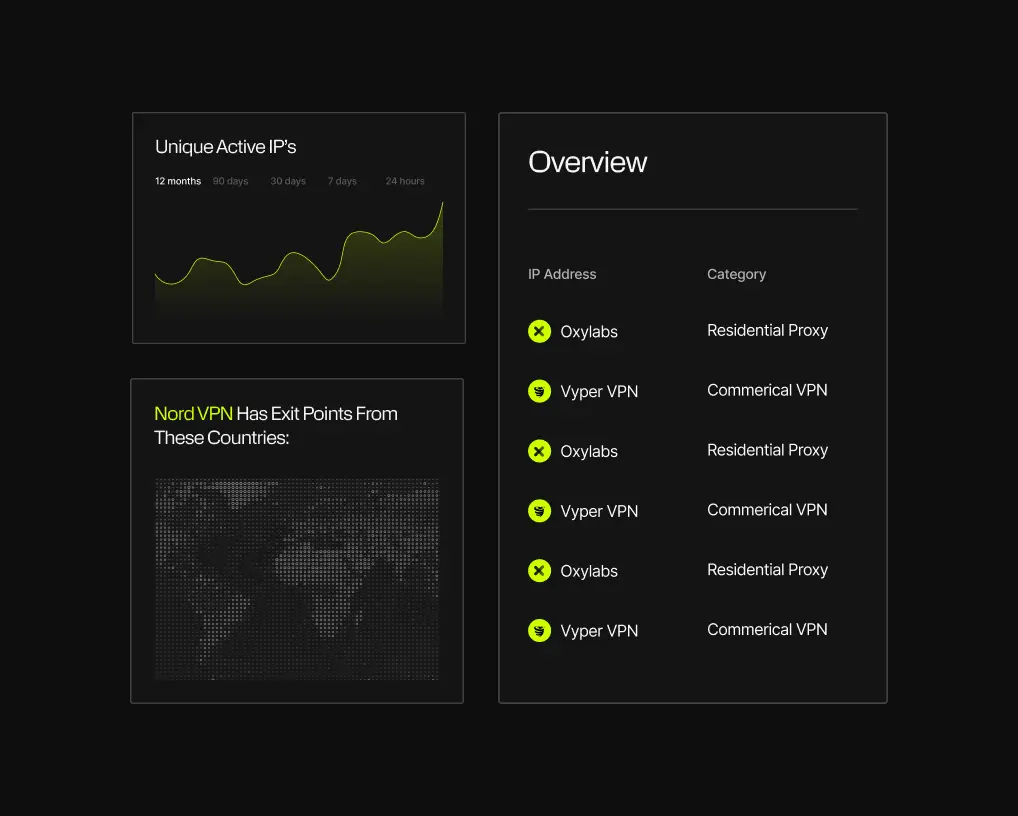



Trusted by teams who fight fraud, not false positives.
Over 95% of Spur customers renew their subscriptions each year. Here are a few reasons why:
7x
increase in fraud detection accuracy.
[Read Case Study]90%+
reduction in fraudulent account creation.
[Read Case Study]Millions
of dollars saved annually.
[Read Case Study]
Where Spur Strengthens Every Layer of Defense.
Best IP reputation product on the market … I simply can’t figure out how they have such breadth and depth of coverage in the space.
Trusted intelligence for every team.
Whether you need real-time detection or large-scale analysis, Spur connects every team to the same verified intelligence.
The Spur platform reveals ~60M active suspect IPs daily by continuously observing global traffic, anonymization infrastructure, and routing behavior across hundreds of millions of IP addresses and 1,000+ current, validated VPN and proxy services.
See the Difference Between Raw Data & Real Intelligence
Start enriching IPs with Spur to reveal the residential proxies, VPNs, and bots hiding in plain sight.