AttackIQ Professional Services
Prove what works.
Improve what doesn’t.
Expert services that help teams turn adversary-driven validation into confident decisions and measurable security improvement—fast.
Why AttackIQ Professional Services
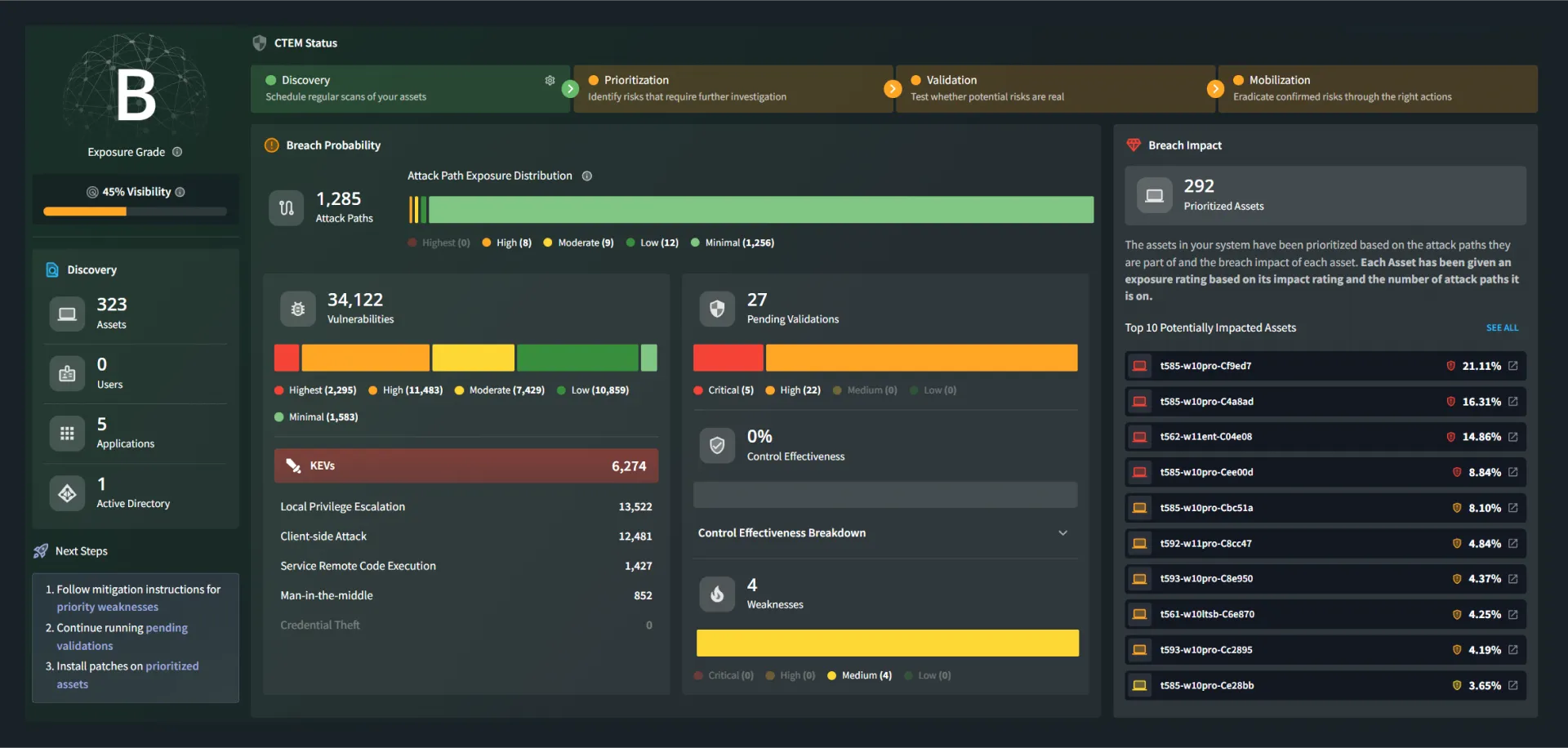
Enable confident decisions and measurable security improvement through adversary-driven validation. AttackIQ Professional Services helps teams assess control effectiveness, prioritize remediation, and establish repeatable practices—such as CTEM and threat-informed defense—that scale as threats, environments, and operations evolve.
Adversary-Driven and Validation-Led
Anchor improvement efforts in real attacker behavior using MITRE ATT&CK–aligned techniques and continuous validation.
Execution Over One-Time Assessments
Establish repeatable processes, clear ownership, and a regular cadence that drives ongoing improvement.
Decisions,
Not Just Data
Translate validation results into clear priorities, and actionable remediation teams can execute with confidence.
Mature
and Scale
Evolve from initial validation to sustained exposure management as programs grow and threats change.
Simplify. Validate. Transform.
With the right operating model in place, AttackIQ Professional Services helps teams move beyond visibility to measurable security improvement.
Simplify
Exposure Management
Bring structure and clarity to how exposure is understood, measured, and managed—aligning teams around a shared operating model.
Validate
Security Effectiveness
Confirm how controls and processes reduce exposure to enable confident, evidence-based remediation.
Transform
Security Operations
Embed continuous improvement into day-to-day security operations and optimize performance over time.
Professional
Service Offerings
Our engagements support organizations across the lifecycle of improving security effectiveness—from initial assessment and validation to sustained operational execution and optimization.
SOC Optimization
Build and mature exposure management as an operational discipline
CTEM
Implementation
Establish a clear operating model for understanding, measuring, and managing exposure across the organization.
Learn MoreThreat-INFORM
Your Defense
Prove how controls and processes reduce exposure across the environment to guide confident remediation decisions.
Learn MoreDefense
Optimization
Embed repeatable practices that continuously improve detection, response, and overall security effectiveness.
Learn MoreVanguard
Co-manage continuous security validation with AttackIQ experts.
Continuous Adversary Validation
Ongoing validation of security controls using realistic adversary techniques aligned to MITRE ATT&CK, running continuously and at scale
Prioritized Adversary Emulations
Curated adversary scenarios tailored to your environment and risk priorities, mapped to relevant tactics and techniques
Security Control Gap Identification
Identify where controls fail—including cloud and advanced defenses—and understand why attackers succeed
Our Engagement Approach
AttackIQ Professional Services delivers hands-on, outcome-driven engagements aligned to how security teams plan, execute, and improve. We focus on practical execution, early value delivery, developing the team and the organization, and repeatable practices that support long-term security improvement.
Fixed-scope implementations
Defined engagements to establish core CTEM capabilities and deliver clear, measurable outcomes within a predictable timeline.
Advisory-led optimization
Targeted guidance to refine operating models, improve security control effectiveness, and enhance validation processes.
Co-managed
validation
Ongoing partnership to continuously validate security controls, guide remediation priorities, and optimize detection and response capabilities.
Operational enablement
Hands-on support to prepare teams, processes, and workflows for sustained operation of threat-informed defense programs.
Training & knowledge transfer
Role-based training and hands-on workshops to build internal expertise, align teams on best practices, and enable organizations to independently sustain and evolve validation-driven security programs.
Ready to Get Value Faster?
Talk to an AttackIQ expert about how Professional Services can help you improve security effectiveness and drive measurable results.