
about
event


01
Positive Hack Camp is an onsite camp in Moscow, organized by Positive Technologies with the support of the Russian Ministry of Digital Development
2
weeks of this international camp, held annually
30
lectures from top Russian cybersecurity experts
70
cybersecurity experts worldwide will get hands-on IT infrastructure protection guidance from leading Russian specialists
ways
to escalate privileges across information systems, websites, operating systems, and network infrastructure
03





from the best experts
you will learn


02
tools
for analyzing network and protocol traffic and tuning client-server communication
02





how to
simulate attacks on IT infrastructure and investigate defenses using vulnerability exploitation tools
01






ways
to escalate privileges across information systems, websites, operating systems, and network infrastructure
03





tools
for analyzing network and protocol traffic and tuning client-server communication
02





how to
simulate attacks on IT infrastructure and investigate defenses using vulnerability exploitation tools
01





You provide
01




Round-trip flight to Moscow
Visa, if required
Included
02




Meals
Training
Accommodation
Cultural program
Requirements
03




You are a student
You understand how the internet and local networks work
Your English is B1 or higher
You are confident with Linux or Windows at an advanced user level, including installing software and basic configuration
conditions
for applicants


03
program
overview


04
days of hands-on learning
14
lectures from leading cybersecurity experts
30
cybersecurity experts from around the world
70
Setup and ethics
Prepare local and cloud environments, install tools, and learn ethical hacking principles for safe, responsible practice
Initial access and web exploits
Primary access techniques and web application attacks, including authentication bypass, SQLi, XSS, XXE, and command injection
Privilege escalation and lateral movement
Escalate privileges on Linux and Windows, compromise DMZ hosts, forward traffic, and move across the network
Evasion, Active Directory compromise, and professional growth
Evade detection, use encrypted channels, exploit Active Directory and domain controllers, plus countermeasures and ethics
Recon and scanning
External footprinting, domain and network discovery, host and port scanning to map the target environment
of events
timeline


05




of events
timeline


05






positive hack camp 2026
registration

06

Take the test and complete the form to participate, then wait for confirmation from the organizers.
from previous year
photos and videos


08
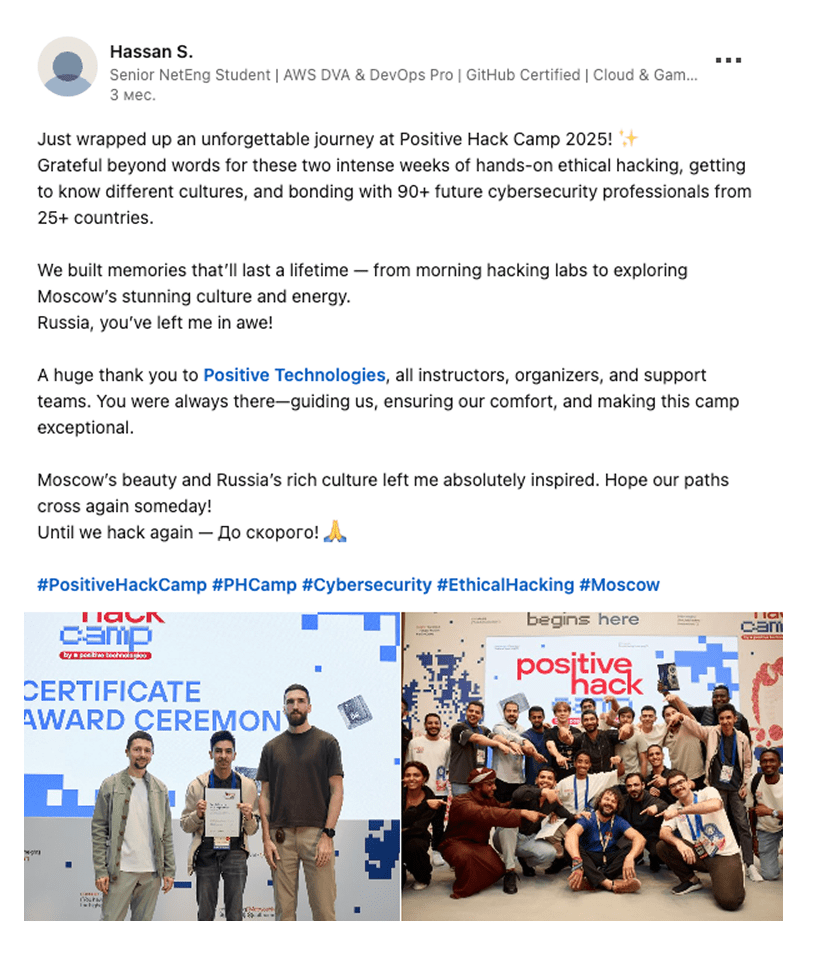
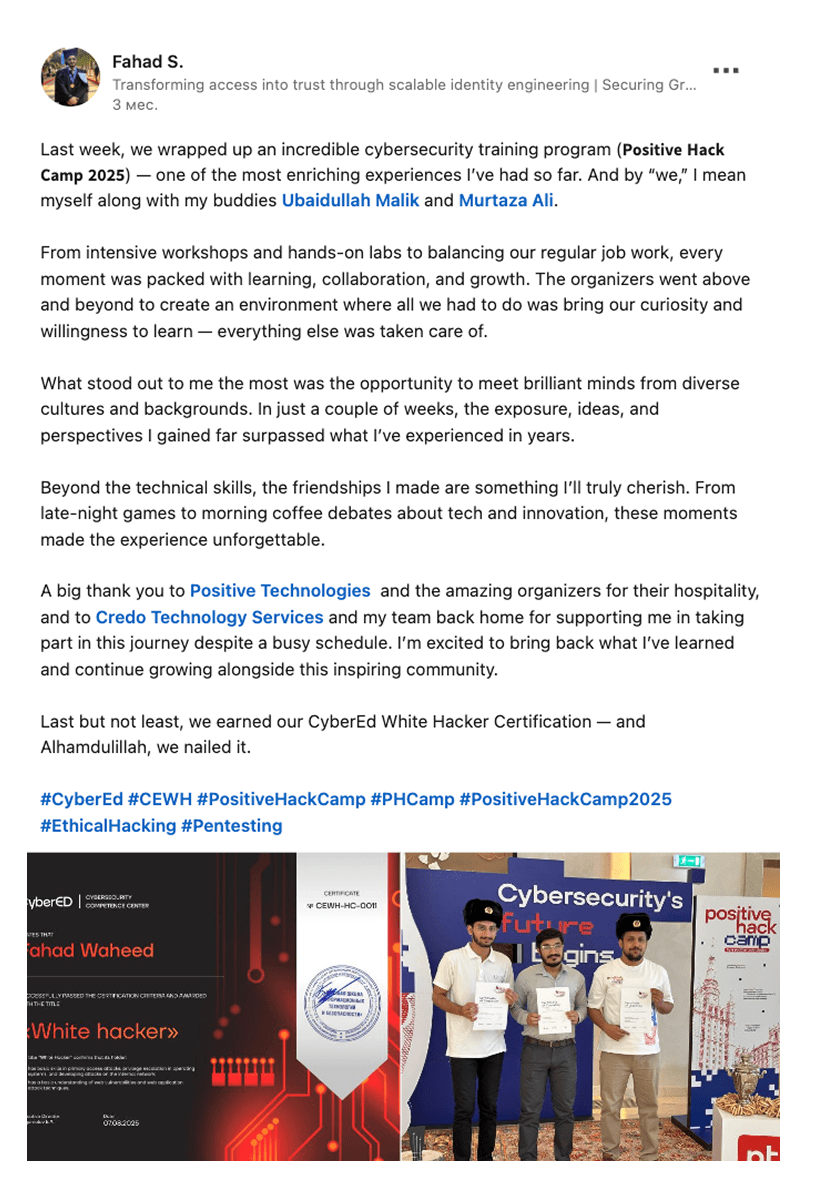
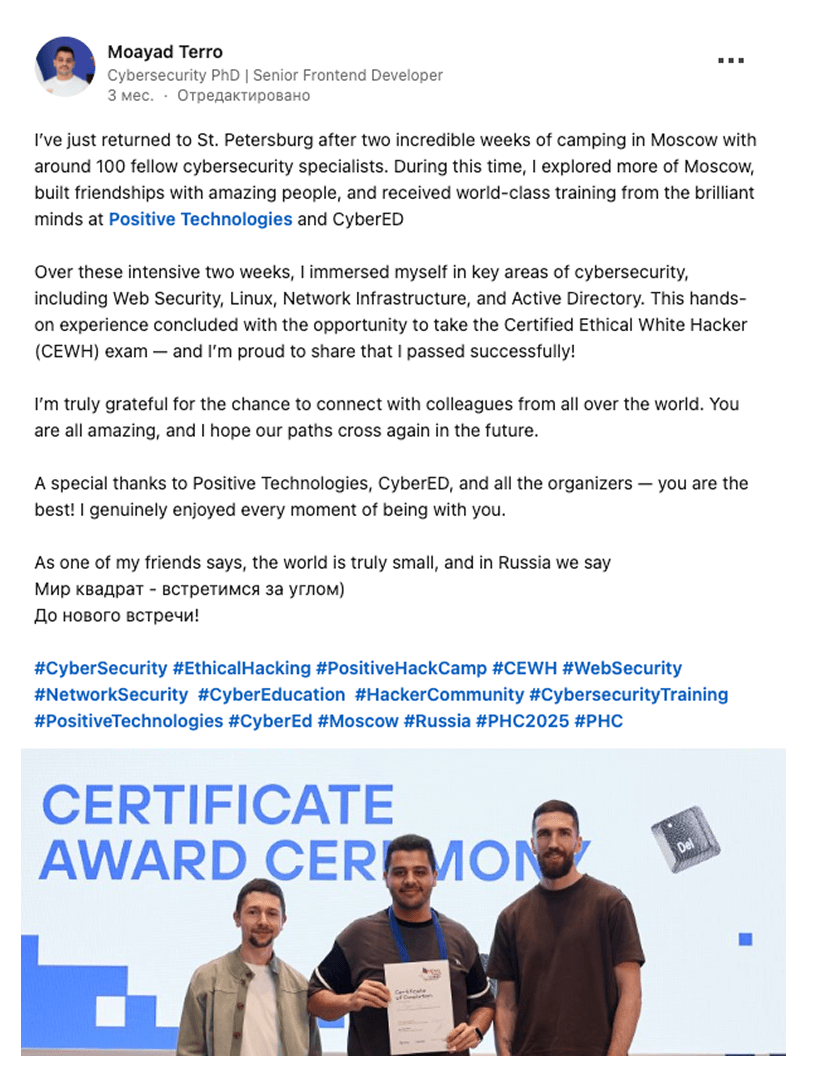
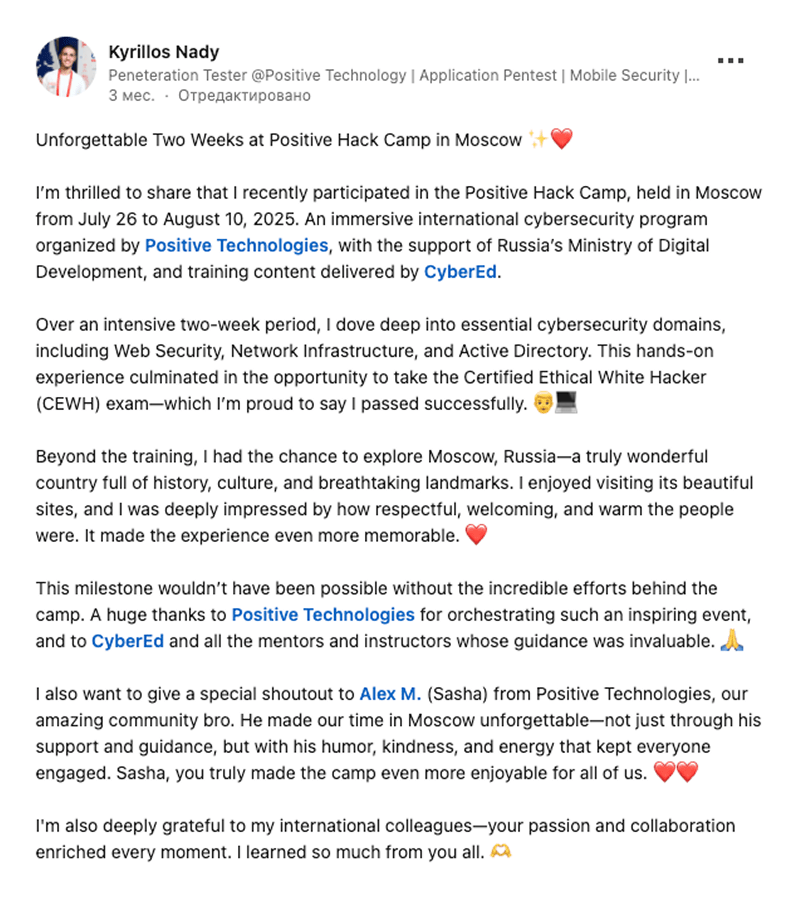
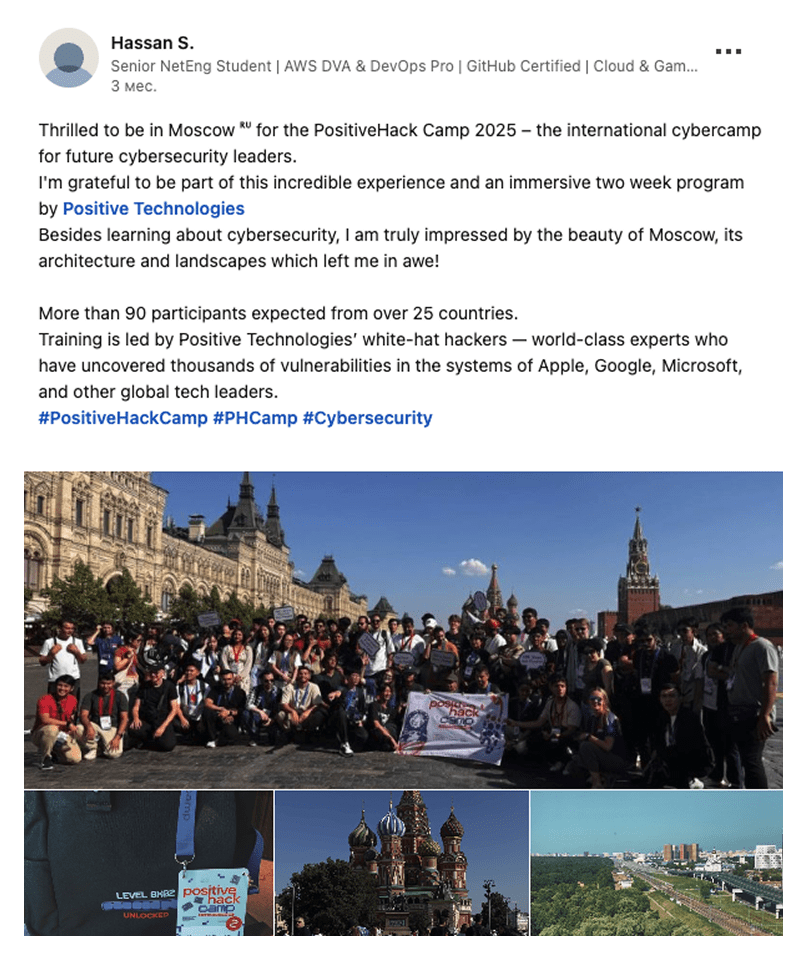
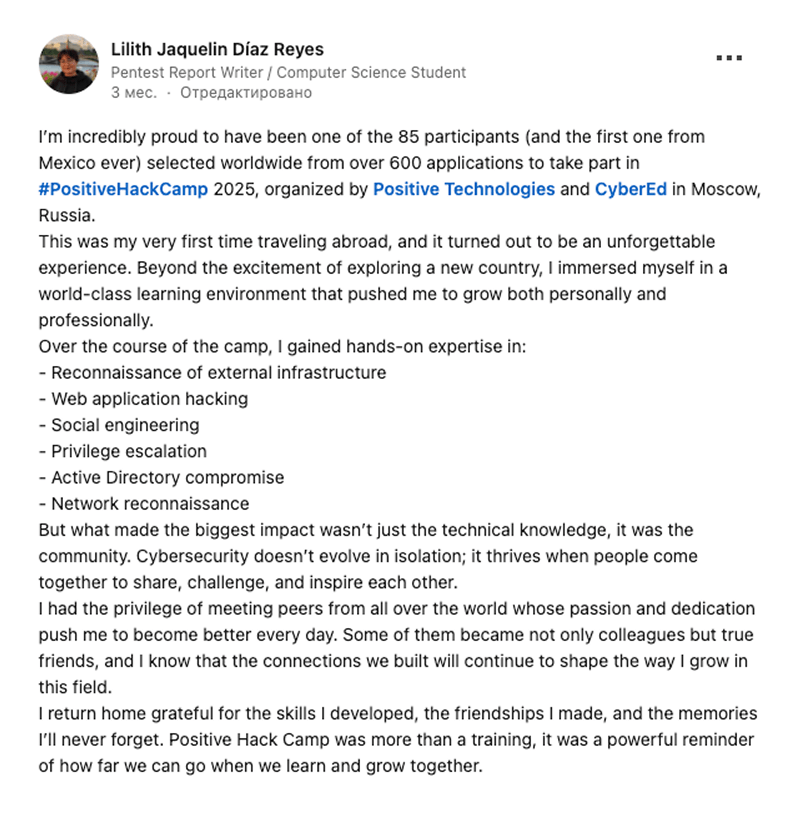
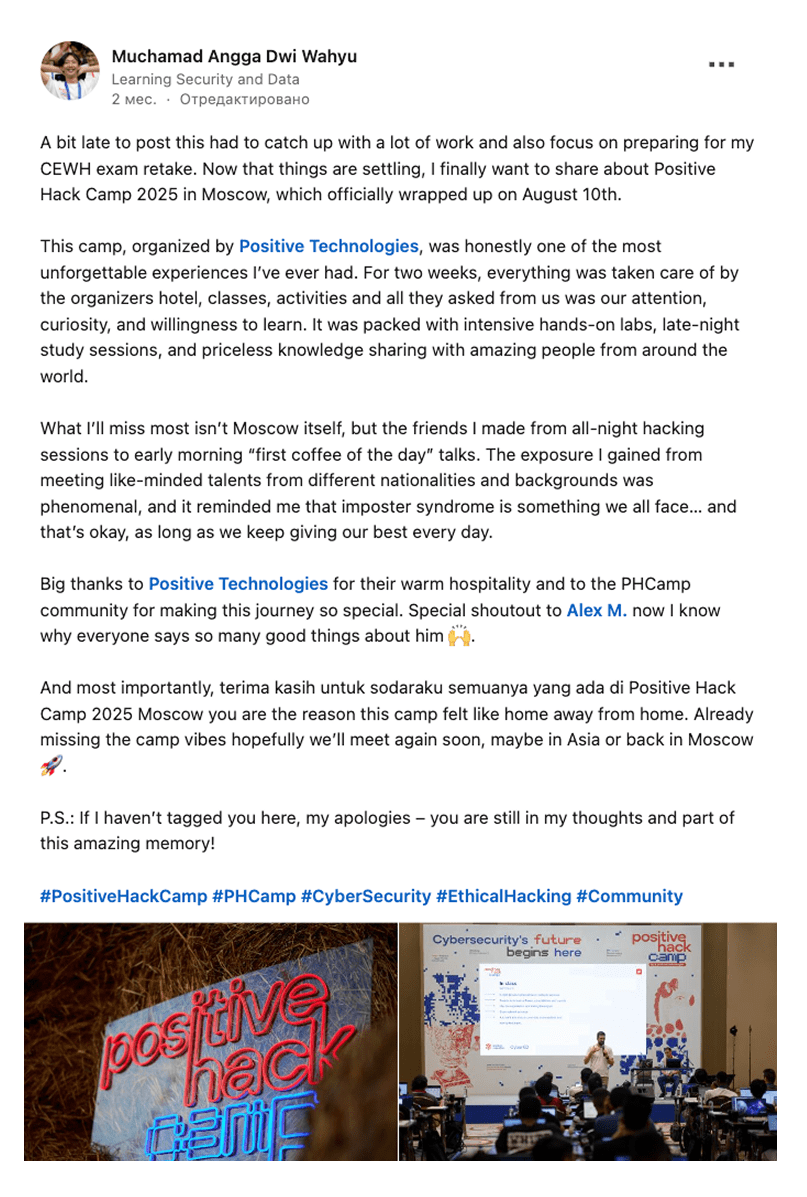
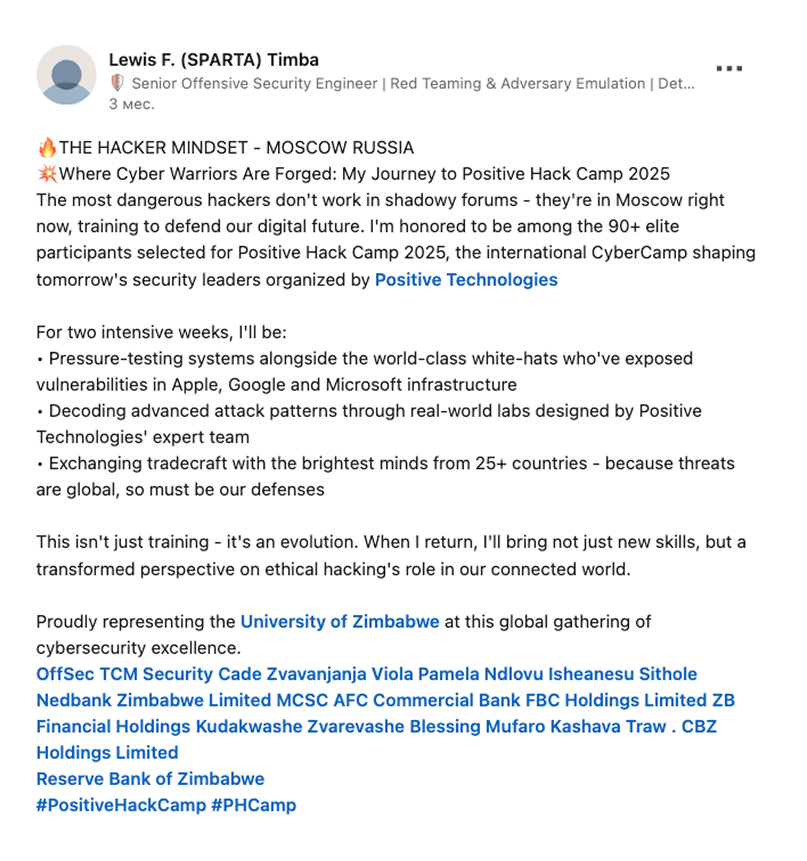
feedback
from attendees


09








+
posts and media tagged #PHCamp and #PositiveHackCamp
100+
Email us:
Social media:
instagram

youtube

linkedin

Company details:
Company name: Joint Stock Company Positive Technologies
Legal address: 107061, Moscow, intracity territory of the municipal district Preobrazhenskoye, Preobrazhenskaya Square, Building 8, Room 60
INN (taxpayer identification number): 7718668887
OGRN (primary state registration number): 1077761087117
Email: [email protected]
Phone: +7 (495) 744-01-44

























