
API Security and Threat Prevention Guide
Strong security is necessary to implement and expose API publicly. Cloud-native apps are strengthened by CNAPP platforms which rely on industry-standard protocols to secure APIs. This blogs covers an array of cloud-native security solutions guarantees end-to-end protection, compliance, and resistance against the top API vulnerabilities identified by OWASP.
Reading Time: 12 minutes
Application programming interfaces (APIs) are the foundation of almost all modern programs. APIs are useful because they make data sharing and communication with external systems simpler. The use of APIs has increased exponentially as a result of cloud computing’s widespread adoption. Enterprise API security strategies must address the rapid expansion of API attack surfaces across cloud-native environments. Enterprise API security strategies must prioritize protection of cloud-exposed APIs as a core control for reducing breach risk. They serve as the main entry point through which hackers might take advantage of weaknesses in cloud-based systems.
As to Gartner’s prediction, since 2022, APIs have emerged as the primary attack vector. Businesses that depend on microservices and cloud-native apps can’t ignore it. Static and runtime protection are areas in which cloud-native application protection platforms (CNAPP) thrive. However, it’s too soon to say whether or not they can be applied to the particular problems that APIs provide. This blog examines the many aspects of API security and the features that enhance CNAPP. Upon completion, you will possess practical advice and tactics to counteract cyberattacks that aim to compromise cloud-native and API-based services.
The need for API security is highlighted by the 2017 Equifax data breach, in which hackers used an API vulnerability to get sensitive personal data belonging to about 147 million individuals. Because APIs are widely utilized in the banking industry for account management and transactions, hackers looking to steal financial data often target these platforms. Because healthcare companies depend on APIs to transfer patient data across various systems, strong API security is essential to safeguarding private medical data. API security is about more than just data protection—it’s about preserving your company’s integrity and credibility.
- PII Protection – Attackers can use APIs to expose private information to outside systems. The usual target is organizations with sensitive financial, medical, or other data. APIs can also leak personally identifiable information (PII).
- Cybersecurity Mitigation – Strong security measures are necessary as API weaknesses are exploited by cybercriminals. Securing APIs lowers the risk of cyberattacks and improves cloud security posture. 88% of organizations experience issues with API authentication.
- Compliance and audit readiness – API security is crucial for industries adhering to regulatory compliance requirements. All guidelines like HIPAA, PCI-DSS, and GDPR require it.
- Reputation and trust – Fortifying APIs eliminates the chances of data breaches and vulnerabilities in cloud-native apps. It protects the company’s brand and builds client confidence.

Cloud-native apps looking to safeguard their APIs should make use of tools provided by a CNAPP platform.
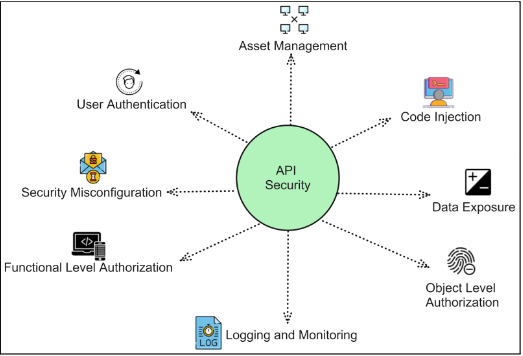
Key Measures for API Security
APIs function as the conduits for data flow within cloud-based applications and services, and enterprise API security strategies must treat them as high-value attack paths. They act as intermediaries between applications, facilitating seamless communication and data exchange. Moreover, APIs grant access to critical services and functionalities within your cloud-based applications. When an attacker compromises APIs, security controls are bypassed, which is why enterprise API security strategies must include continuous runtime protection. Access is bypassed to your cloud-based services without authorization. Data breaches, monetary losses, and reputational harm are common headlines. APIs are one of the most lucrative targets accessible today for malicious actors.
- Authenticity and authorization Authentication ensures that only authorized users access APIs, while authorization controls their actions. Implementing robust authentication and authorization mechanisms is vital for safeguarding cloud-based applications.
- Encryption. SSL/TLS encryption for APIs is fundamental to ensuring the secure transmission of data. It prevents nefarious entities from potentially intercepting data.
- Inventory Control. Precise API inventory is essential but difficult since cloud services are dynamic. API traffic and use are tracked by logging, monitoring, and discovery. Especially with runtime capabilities that are always active,
- Protection at Run-Time. API run-time security defends against a range of threats, such as DDoS, brute force, and BOLA assaults. Customized rules and checks prevent API calls that try to violate business logic. Brute force and DoS assaults are lessened by rate restrictions and throttling.
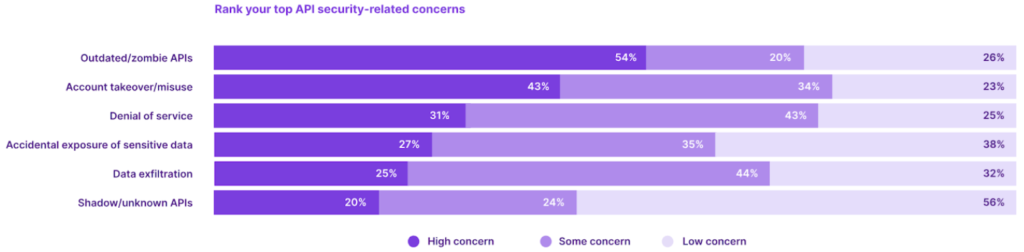
Source: https://salt.security/api-security-trends
Finance
- Token-based authentication and authorization via protocols like OAuth 2.0 are used by secure APIs in banking and financial services.
- Banks encrypt their APIs with OAuth 2.0, enabling users to access financial data via mobile apps.
- After user authentication, access tokens are granted, enabling safe and regulated access to private information.
Healthcare
- Encryption methods are used to safeguard patient records accessible via APIs.
- Transport Layer Security (TLS) can be used to encrypt data transmitted when an electronic health record (EHR) system and a healthcare provider’s system connect via an API.
- Only authorized healthcare workers may access patient information via APIs thanks to authentication and authorization techniques, including role-based access, access restrictions, and API keys.
41% of firms claim that controls and visibility over security are lacking in development processes.
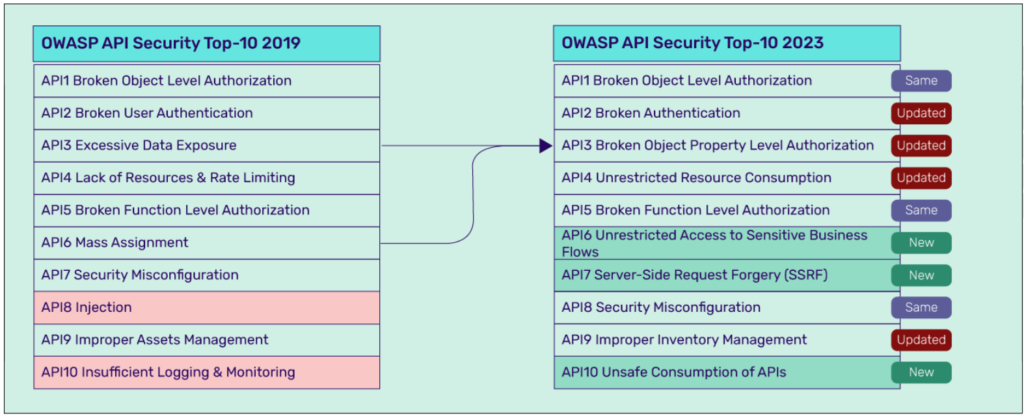
Source: OWASP Top 10 API Security Risks
Advantages of CNAPP
| Aspect | Benefit |
| Comprehensive Security | CNAPP provides runtime protection, vulnerability management, threat detection, and response capabilities, addressing web application attacks, API attacks, and cloud infrastructure threats |
| Integration of Cloud Security Categories | CNAPP combines multiple cloud security categories, such as DevSecOps, CSPM, IaC scanning, KSPM, CIEM, and CWPP, streamlining security efforts. |
| Full-stack Application Visibility | SecOps and DevOps teams benefit from enhanced visibility, facilitating efficient threat detection and response. |
| Automated Vulnerability Management | Automated detection of vulnerabilities in API code and configurations. Offers remediation recommendations based on baselines. |
| API Security | Validation and monitoring of API traffic. Guarantees secure communication between application components |
| Identity and Access Management | CNAPP manages user access, enforces role-based access control, and ensures secure authentication. |
| Compliance and Audit | The platform aids in maintaining regulatory compliance by continuously monitoring the environment and generating audit reports. |
Components of CNAPP and Their Functions
| Component | Function |
| Policy Engine | Enforces security policies, ensuring compliance with best practices. |
| Runtime Protection | Monitors application behavior in real-time to detect and block suspicious activities. |
| Vulnerability Management | Scans for potential vulnerabilities in application code, containers, and infrastructure, providing remediation recommendations. |
| API Security | Validates and monitors API traffic for secure communication. |
| Identity and Access Management (IAM) | Manages user access, enforcing role-based access control and secure authentication. |
| Compliance and Audit | Aid in maintaining regulatory compliance by continuously monitoring the environment and generating audit reports. |
API Protection Capabilities that Enhance CNAPP
Real-time Threat Detection and Mitigation
- API protection solutions ensure high efficacy rates in real-time threat detection. They identify and mitigate malicious traffic to maintain uninterrupted, business-critical transactions.
- These solutions are designed to prevent false positives that disrupt operations.
- Real-time threat detection aligns with cloud workload protection platforms (CWPP) and container network access and policy solutions. Constant vigilance against cyber threats targeting accessible applications is virtually guaranteed.
Shadow API Discovery
- Unidentified APIs used by internal groups without security team notification pose a threat to organizations.
- Shadow API discovery complements CNAPP by safeguarding against unknown APIs and cloud components. CNAPP focuses on known applications and infrastructure. This capability extends protection to the realm of the unknown.
Rapid Application Code Changes
- Cloud-deployed API applications almost always follow agile development methodologies. API specifications are changed; hence, they need to be QA’ed with security in mind.
- Unmonitored changes can lead to compliance breaches and data exposure issues.
- Seek out and address the OWASP API Security Top 10 vulnerabilities.
- Regulated inventory checks are also provided to identify and mitigate such vulnerabilities before they can be exploited.
When addressing API security, a comprehensive approach should encompass the six stages of the continuous API lifecycle, aligning effectively with CNAPP.
| Stage | Description |
| Discovery | Continuous discovery of an organization’s API attack surface, including shadow APIs implemented without security oversight. |
| Inventory | Management of both managed and unmanaged APIs from a centralized location. |
| Compliance | Ensuring API compliance with organizational security policies and industry best practices. Notifications for non-compliant APIs facilitate immediate remediation. |
| Detection | Real-time detection of API threats with minimal false positives, eliminating the need for third-party tools. |
| Prevention | Inline prevention of API cyberattacks targeting mission-critical applications without reliance on external infrastructure. |
| Testing | Assessment of APIs for conformance, risks, and sensitive data exposure before deployment. |
How Can a CNAPP Toolkit Help?
In the chain of security, broken and undefended APIs are the weakest link. Developers hardly ever prioritize security over speed, features, usefulness, and user-friendliness. As a result, a series of exploitable vulnerabilities are created. Moreover, cloud-native APIs are frequently available online. If the proper security framework is not put in place, this may make them accessible to everybody. Because of this accessibility, hackers have an easier time breaking into cloud-based services and taking advantage of API flaws.
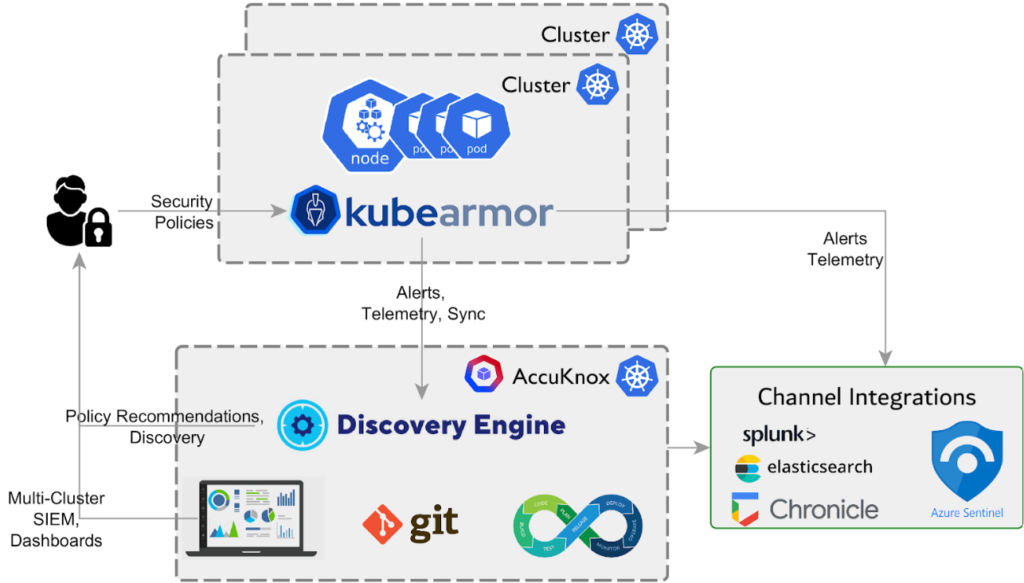
- The discovery engine’s runtime API Security monitors and filters system call activities of containerized workloads at runtime. This prevents attacks on API endpoints. Our CNAPP solution also enforces least privilege principles and whitelists allowed system calls.
- Dynamic application security testing (DAST) on APIs to identify vulnerabilities. This is done by integrating with API gateways to analyze traffic between microservices.
- Continuously scan APIs to detect misconfigurations. It checks for compliance with the OWASP API Security Top 10.
- KubeArmor, an open-source discovery engine, monitors and filters incoming and outgoing network connections to APIs. This is useful when blacklisting or blocking unauthorized access or abuse. Aids you in enforcing network segmentation and zero trust.
- Runtime controls prevent the exploitation of unpatched vulnerabilities in API endpoints. KubeArmor can block attacks in real time before they reach the application layer.
- Our CNAPP security toolkit integrates static application security testing (SAST), software composition analysis (SCA), and API protection (DAST) results into one unified platform. Get full coverage and visibility into API vulnerabilities from code to runtime.
- Granular runtime controls on pod activities protect backend resources from abuse through APIs. Restrict pod access to only what is needed.
- A combination of network traffic mirroring and eBPF means observability in API communications between microservices. Detecting anomalous behaviors has never been easier.
- Our CIEM provides identity and access management (IAM) for human and non-human identities accessing APIs.
- KubeArmor allows the creation of custom policies. These are useful when you wish to enforce security best practices for Kubernetes-hosted APIs. It recommends policies based on workload behaviors.
Conclusion
APIs are essential to modern cloud-native applications, and enterprise API security strategies must account for APIs as a primary production attack surface. A multi-layered strategy is needed throughout the development lifecycle for comprehensive API security. The past year saw a 681% spike in API attacks.
The AccuKnox Enterprise CNAPP tool offers runtime controls, observability, and vulnerability management to safeguard APIs after deployment. However, developers must incorporate secure API design concepts from the outset. OWASP offers great advice on best practices for API security. The security pillars of authentication, authorization, input validation, rate limitation, and encryption should be used by developers while designing APIs. To minimize API vulnerabilities before exploitation, developers should implement a proactive security posture that combines secure SDLC and infrastructure protections. This end-to-end security chain seamlessly incorporates the CNAPP tool.
FAQ
What makes an enterprise API security platform suitable for production environments?
A production-ready platform operates inline or close to traffic paths, delivers low-latency inspection, supports high availability, and minimizes false positives. It must handle encrypted traffic, scale with microservices, and provide audit logs for compliance and forensics.
How does runtime API security differ from traditional API gateways and WAFs?
Gateways manage routing, authentication, and rate limiting. WAFs focus on known web attack patterns. Runtime API security analyzes live API behavior, user context, and service interactions to detect abuse, logic attacks, and credential misuse that signature tools often miss.
How does this enterprise API security solution provide real-time API threat detection and blocking?
It inspects live API calls, builds behavioral baselines, and detects anomalies such as abnormal data access, token abuse, and excessive object enumeration. Enforcement occurs immediately through inline blocking or policy-based response.
How does the platform secure APIs running on Kubernetes and cloud-native microservices?
Security controls extend to the workload level using runtime enforcement, eBPF-based telemetry, and Kubernetes-native policies. This allows monitoring of service-to-service API calls, east-west traffic, and pod-level behavior without modifying application code.
Can this enterprise API security platform discover and protect internal and shadow APIs?
Yes. Continuous API discovery analyzes traffic patterns, service meshes, and network telemetry to identify undocumented or unmanaged APIs. Once identified, they can be added to inventory, monitored, and protected with the same policies as known APIs.
How does behavioral analysis help prevent API abuse and business logic attacks?
Behavioral models detect deviations such as unusual object access sequences, abnormal request rates per identity, and misuse of valid tokens. This helps stop attacks that follow protocol rules but violate intended application logic.
Does the platform protect against OWASP API Top 10 risks in production traffic?
Yes. Runtime inspection and policy enforcement address risks such as BOLA, broken authentication, excessive data exposure, mass assignment, and lack of rate limiting, directly in live traffic rather than only during testing.
How does policy enforcement work for enterprise API security across distributed environments?
Policies are centrally defined and enforced at multiple points, including gateways, sidecars, and runtime agents. This ensures consistent protection across multi-cloud, hybrid, and Kubernetes clusters.
Can this API security solution be deployed without code changes in enterprise environments?
Yes. Deployment typically relies on traffic mirroring, sidecar proxies, gateway integrations, or kernel-level telemetry. This allows protection and visibility without requiring application rewrites.
How does this enterprise API security platform integrate with SIEM, SOAR, and Zero Trust architectures?
Security events stream to SIEM for correlation, SOAR for automated response, and identity systems for context-aware enforcement. Integration with Zero Trust frameworks ensures API access decisions consider identity, device, and behavior signals.
Get a LIVE Tour
Ready For A Personalized Security Assessment?
“Choosing AccuKnox was driven by opensource KubeArmor’s novel use of eBPF and LSM technologies, delivering runtime security”

Golan Ben-Oni
Chief Information Officer
“At Prudent, we advocate for a comprehensive end-to-end methodology in application and cloud security. AccuKnox excelled in all areas in our in depth evaluation.”

Manoj Kern
CIO
“Tible is committed to delivering comprehensive security, compliance, and governance for all of its stakeholders.”

Merijn Boom
Managing Director

















